Two Greek researchers they managed to spot a loophole security on a NASA website (subdomain), which allowed them to do so SQL injection and access the organization's database.
According to Greek researchers, the US space agency was promptly alerted to the security gap, but to date it has not made any correction.
Researchers Dimitris Chatzidimitris and Anastasis Vasileiadhs report at Secnews.gr via email:
“On August 29, we discovered a vulnerability while navigating a Nasa page (https://www.jpl.nasα.gov/which relates to various promotion systems….
Vulnerability is a type SQL injection and the link to this weakness is:
Note Secnews.gr: We do not list the link for obvious reasons but we list some of the items we received by email:
Parameter: catId (GET)
Type: boolean-based blind
Database version: 5.1.61-community-lo
"This particular vulnerability gave us access to the databases of that site"
Researchers report:
"After that we did not proceed to any possible access to the server beyond the bases as we had already confirmed that the page was not secure.
Immediately on August 27 we contacted the contact form on their page and we briefed them in detail to correct their security.
Until today 8 September we did not get any answer on this.
Security researchers:
Dimitris Chatzidimitris
Anastasis Vasileiadhs ”
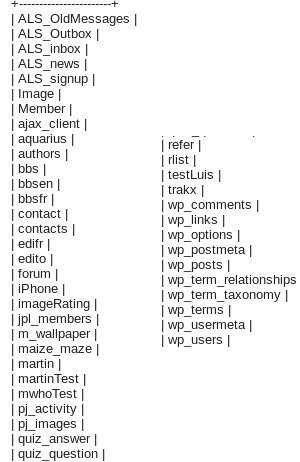
Here is a screenshot from the tables of the database. We notice that the tables also include those that record website user data (usernames and passwords).
See the image below (wp-users, contacts, Member, authors)
_____________________________________
The information remains available to interested parties, both by the researchers themselves and by Secnews.gr.
Updating vulnerabilities found in organizations is considered to be absolutely essential (especially when there are high-traffic websites), and Secnews.gr for us is a direct priority.
We hope that in this way, i.e. the direct exposure of each vulnerability and not with its "hood", we contribute to a more safe Internet.
Of course, we have met many companies and organizations, both locally and globally, that instead of working together to resolve a vulnerability, they are moving legal means to persecute the researchers by covering the security gap very carefully with the mat, trying to avoid negative impressions .





