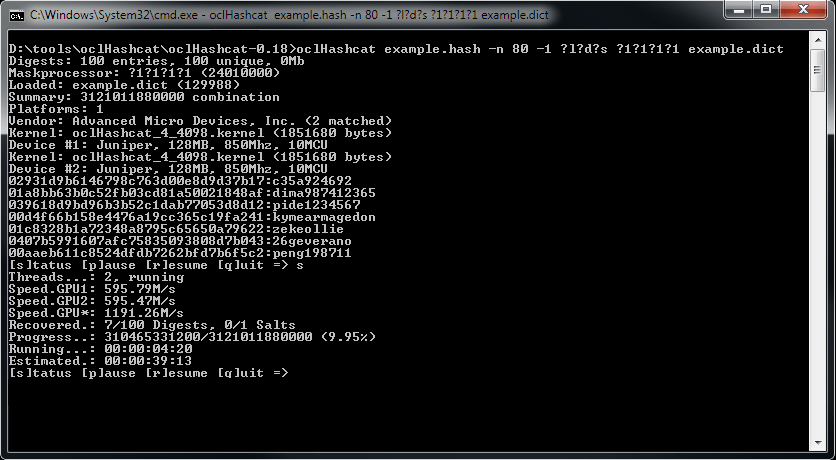
The oclHashcat is one of the fastest password cracking tools that uses GPU to "decode" md5crypt, phpass, mscash2 and WPA / WPA2. The first and only one he uses GPGPU rule engine.
Those of you who know the tool and look for it oclHashcat-plus, you should know that particular version has been abolished but all of its services are in oclHashcat. The application runs on all versions of Windows and Linux on 32 and 64 bit.
IGuRu.gr presents this tool to protect your systems and ONLY for that reason. We are against any kind of malicious use of the tool.
Download latest version
| Name | Version | md5sum | Date: |
|---|---|---|---|
| oclHashcat for AMD | v1.30 | 4e6e77bbdb15df534348f7745dbc5d0a | 2014.08.21 |
| oclHashcat for NVidia | v1.30 | 1e17da4d927c6745c560af2c608337aa | 2014.08.21 |
GPU Driver requirements:
- NV users require ForceWare 331.67 or later
- AMD users require Catalyst 14.6b or later
- Worlds fastest Password cracker
- Worlds first and only GPGPU based rule engine
- Free
- Multi-GPU (up to 128 gpus)
- Multi-Hash (up to 100 million hashes)
- Multi-OS (Linux & Windows native binaries)
- Multi-Platform (OpenCL & CUDA support)
- Multi-Algo (see below)
- Low resource utilization, you can still watch movies or play games while cracking
- Focuses highly iterated modern hashes
- Focuses dictionary based attacks
- Supports distributed cracking
- Supports pause / summarizes while cracking
- Supports sessions
- Supports restore
- Supports reading words from fillet
- Supports reading words from stdin
- Supports hex-salt
- Supports hex-charset
- Built-in benchmarking system
- Integrated thermal watchdog
- 100 + Algorithms implemented with performance in mind
- ... and much more
oclHashcat Screenshot
Attack-Modes
- Straight *
- Combination
- Brute-force
- Hybrid dict + mask
- Hybrid mask + dict
* accept Rules
Algorithms
- MD4
- MD5
- SHA1
- SHA-256
- SHA-512
- SHA-3 (Keccak)
- RipeMD160
- Whirlpool
- GOST R 34.11-94
- HMAC-MD5 (key = $ pass)
- HMAC-MD5 (key = $ salt)
- HMAC-SHA1 (key = $ pass)
- HMAC-SHA1 (key = $ salt)
- HMAC-SHA256 (key = $ pass)
- HMAC-SHA256 (key = $ salt)
- HMAC-SHA512 (key = $ pass)
- HMAC-SHA512 (key = $ salt)
- LM
- NTLM
- DCC
- DCC2
- NetNTLMv1
- NetNTLMv1 + ESS
- NetNTLMv2
- Kerberos 5 AS-REQ Pre-Authentication 23
- AIX {smd5}
- AIX {ssha1}
- AIX {ssha256}
- AIX {ssha512}
- FreeBSD MD5
- OpenBSD Blowfish
- descrypt
- md5crypt
- bcrypt
- scrypt
- sha256crypt
- sha512crypt
- DES (Unix)
- MD5 (Unix)
- SHA256 (Unix)
- SHA512 (Unix)
- OSX v10.4
- OSX v10.5
- OSX v10.6
- OSX v10.7
- OSX v10.8
- OSX v10.9
- Cisco-ASA
- Cisco-IOS
- Cisco-PIX
- GRUB 2
- Juniper Netscreen / SSG (ScreenOS)
- RACF
- Android PIN
- Android FDE
- MSSQL
- MySQL
- Oracle
- Postgres
- Sybase
- DNSSEC (NSEC3)
- IKE-PSK
- IPMI2 RAKP
- iSCSI CHAP
- WPA
- WPA2
- 1Password, cloudkeychain
- 1Password, agilekeychain
- LastPass
- Password Safe v2
- Password Safe v3
- TrueCrypt 5.0 + PBKDF2 HMAC-RipeMD160 + AES
- TrueCrypt 5.0 + PBKDF2 HMAC-SHA512 + AES
- TrueCrypt 5.0 + PBKDF2 HMAC-Whirlpool + AES
- TrueCrypt 5.0 + PBKDF2 HMAC-RipeMD160 + BEA + boot-mode
- TrueCrypt 5.0 + PBKDF2 HMAC-RipeMD160 + BEA + hidden-volume
- TrueCrypt 5.0 + PBKDF2 HMAC-SHA512 + BEA + hidden-volume
- TrueCrypt 5.0 + PBKDF2 HMAC-Whirlpool + BEA + hidden-volume
- TrueCrypt 5.0 + PBKDF2 HMAC-RipeMD160 + BEA + hidden-volume + boot-mode
- SAP CODVN B (BCODE)
- SAP CODVN F / G (PASSCODE)
- Lotus Notes / Domino 5
- Lotus Notes / Domino 6
- Lotus Notes / Domino 8
- PeopleSoft
- Citrix Netscaler
- Netscape LDAP SHA / SSHA
- Apache MD5-APR
- Skype or Whatsapp
- hMailServer
- EPiServer
- Drupal
- IPB
- Joomla
- MyBB
- osCommerce
- Redmine
- SMF
- vBulletin
- PHPS
- Mediawiki B type
- Woltlab Burning Board
- xt: Commerce
- WordPress
- phpBB3
- MD5 Half (Left, Mid, Right)
- Double MD5
- Double SHA1
- md5 ($ pass. $ salt)
- md5 ($ salt. $ pass)
- md5 (unicode ($ pass) $ salt)
- md5 ($ salt.unicode ($ pass))
- md5 (sha1 ($ pass))
- md5 ($ salt.md5 ($ pass))
- sha1 ($ pass. $ salt)
- sha1 ($ salt. $ pass)
- sha1 (unicode ($ pass) $ salt)
- sha1 ($ salt.unicode ($ pass))
- sha1 (md5 ($ pass))
- sha256 ($ pass. $ salt)
- sha256 ($ salt. $ pass)
- sha256 (unicode ($ pass) $ salt)
- sha256 ($ salt.unicode ($ pass))
- sha512 ($ pass. $ salt)
- sha512 ($ salt. $ pass)
- sha512 (unicode ($ pass) $ salt)
- sha512 ($ salt.unicode ($ pass))
Tested OS
- All Windows and Linux versions should work on both 32 and 64 bits
Tested GPU
- All CUDA and Stream enabled cards should work