A security researcher known as “Mobile Hacker", shown how vulnerable phones are Android which have not been updated.
In his demonstration, he revealed a potentially devastating zero-click attack that is being exploited recently security gaps on Bluetooth to install malware via Metasploit, a popular penetration testing framework, on devices that had not been updated.
'Mobile Hacker' used exploitation scripts to create a proof-of-concept (PoC) released by Marc Newlin earlier this month. These scripts are freely accessible on GitHub and exploits CVE-2023-45866, CVE-2024-21306, and CVE-2024-0230 (more information).
What's really worrying about these scripts is that they work perfectly on devices where Bluetooth is enabled and active. The attack can be launched from another mobile device within Bluetooth range without requiring any interaction from the victim (zero-click), and leaves no obvious signs of tampering.
This vulnerability highlights the importance of updating our devices immediately.
Zero-click attacks, for those who may not know, are cyber threats that require no interaction from the victim, no clicking on suspicious links or λήψη applications. The hacker simply needs proximity to perform these malicious actions over Bluetooth. The vulnerability in question affects many operating systems on different devices, but is particularly concerning for older versions of Android.
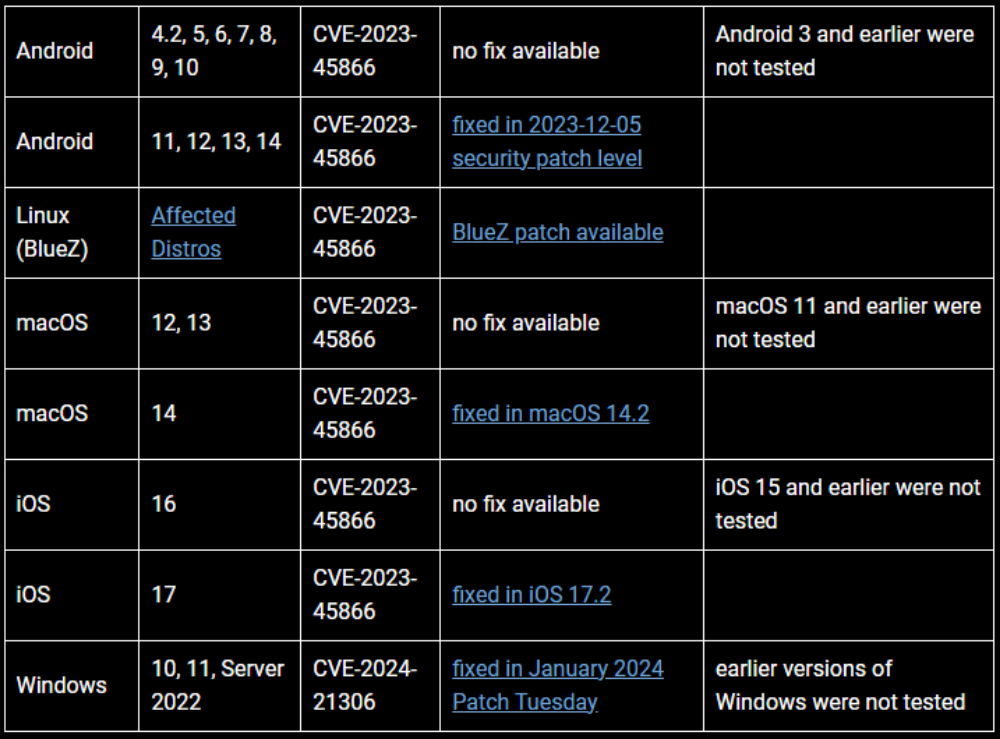
Why; Most Android vendors stop supporting devices after just two years and follow infrequent update cycles (quarterly at best). This means security updates are delayed for months making these devices ripe targets for hackers.
To give you a clearer picture, all Android devices from version 10 and earlier are vulnerable. For newer versions such as Android 11 to 14 that have active support, the flaws were addressed in the December 2023 update.