Bookworm: Ένα νέο trojan που ανακαλύφθηκε από την Palo Alto Networks χρησιμοποιεί λογισμικό ασφαλείας που υπάρχει εγκατεστημένο στον computer of the user to load archives DLL required to install it.
This new trojan was called Bookworm by them researchers from Palo Alto, and has some similarities to RAT PlugX.
For now, Palo Alto reports that the trojan is only released in Thailand.
Regarding its internal structure, Bookworm appears to be part of a new upward trend in vertebrate malware,
The malicious threats it contains begin to install on the victim's computer in multiple stages to avoid detection. They allegedly use a remote C&C server (administration and control) to control what components they upload to the victim's computer, based on the target profile.
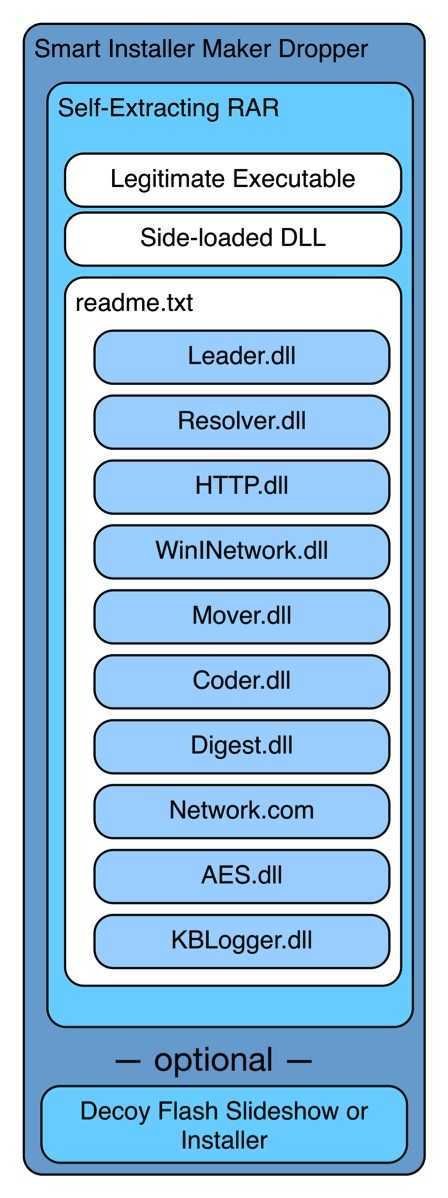
The internal architecture of the trojan Bookworm is simple. Many malicious DLLs are encrypted using the XOR algorithm and stack together in a Readme.txt file.
This Readme.txt then works with purely executable DLLs and some other than a self-extracting RAR file, which in turn incorporates the Smart Installer, an application for creating installation packages.
When the installer runs, the self-extracting hardware that discharges the malware from the Readme.txt, clean DLL, and the clean EXE.
But the interesting thing is that after the completion of the preletterτος εγκατάστασης, λανσάρει αυτόματα το καθαρό EXE που μόλις έχει δημιουργηθεί. Αυτό το εκτελέσιμο αρχείο αρχίζει να αναζητεί εκτελέσιμα αρχεία των εφαρμογών Microsoft Malware Protection (MsMpEng.exe) and Kaspersky Anti-Virus (ushata.exe)..
When it discovers them, it loads the clean DLL files into those executables and uses the permissions of those applications to install as service of Microsoft.
So Bookworm. has all the permissions it needs to run all the modules in the readme.txt file, and starts communications with the C&C server, adding new malicious files while sending stolen data to the server.
The researchers did not say what other modules were found, as Bookworm is difficult to analyze, as it uses at least four encryption algorithms when communicating with the C&C server (RC4, AES, XOR, and LZO).