With about 5 billion people, from all over the world, to watch the World Cup, the event is undoubtedly in the spotlight these weeks. As the teams progress in their quest to reach the final, fans become increasingly invested in their national team's success, with many placing bets or even traveling to Qatar to show their support in person.
But as the competition increases, it is important that fans remain vigilant against the increased risks better safetys posed by threat actors, who take advantage of the situation and "run" many phishing campaigns.
What is electronic fishing (phishing);
Phishing is a type of cyberattack where fraudsters send messages pretending to come from a trustworthy person or company. Phishing emails are designed to manipulate a user into taking an action, such as downloading a maliciousυ αρχείου, το κλικ σε έναν ύποπτο σύνδεσμο ή η αποκάλυψη ευαίσθητων πληροφοριών. Ο βασικός τρόπος παράδοσης μιας επίθεσης ηλεκτρονικού ψαρέματος είναι μέσω SMS, email, κοινωνικών μέσων ή άλλων ηλεκτρονικών μέσων επικοινωνίας.
In a phishing campaign, the emails the target receives will appear to come from a known contact or organization. Attackers often create fake websites that look like a trusted entity, such as the target's bank, workplace or university. Through these sites, attackers try to collect personal information, such as usernames and passwords or payment information.
In this case, many of the recent campaigns are related to selling last-minute tickets or announcing a sports betting win. These messages or websites usually include malicious links that, once clicked, deploy malware and infect the device ή ζητούν στοιχεία σύνδεσης που οι χάκερ μπορούν στη συνέχεια να κλέψουν.
The scams related to the World Cup are on the rise
Avanan, a Check Point company, has already reported an influx of World Cup-related phishing emails deployed in multiple languages. Many of the scams reported focus on sports betting, trying to lure victims into handing over bank details. The images below show some recent examples of hackers pretending to be legitimate betting sites.

In light of this recent wave of phishing scams, Check Point Software has provided three practical tips allowing fans to focus on the game:
- Be aware of imitation: Many scam sites will use a name domain similar to the brand they are trying to replicate, but with additional letters or misspellings. To make sure you're not handing over your bank details to fraudsters, pay attention to URLs to check for anything unusual or suspicious. By taking a minute to look for telltale signs that a website may be fraudulent, you can quickly determine its legitimacy.
- Never share your credentials: Credential theft is a common goal of phishing emails. Many people reuse the same usernames and passwords across different accounts, so stealing credentials for a single account is likely to give an attacker access to others. Not all attacks are direct either. Some phishing emails deliver malware, such as keyloggers or trojans, designed to track when you type passwords on your computer. Never tell anyone your password, and if an email sends you to a login page, visit the site directly and log in from there to protect yourself from similar phishing sites.
- Protect your mobile devices: With most of us now accessing our email from our phones, and with hackers now sending malicious text messages, it's important that our mobile devices are also protected against the newest threats. Once granted access, one A cybercriminal can steal an incalculable amount of information, and a breach can even compromise a victim's known contacts. As a result, it is important to use proactive mobile threat protection solutions that protect devices from advanced mobile threats.
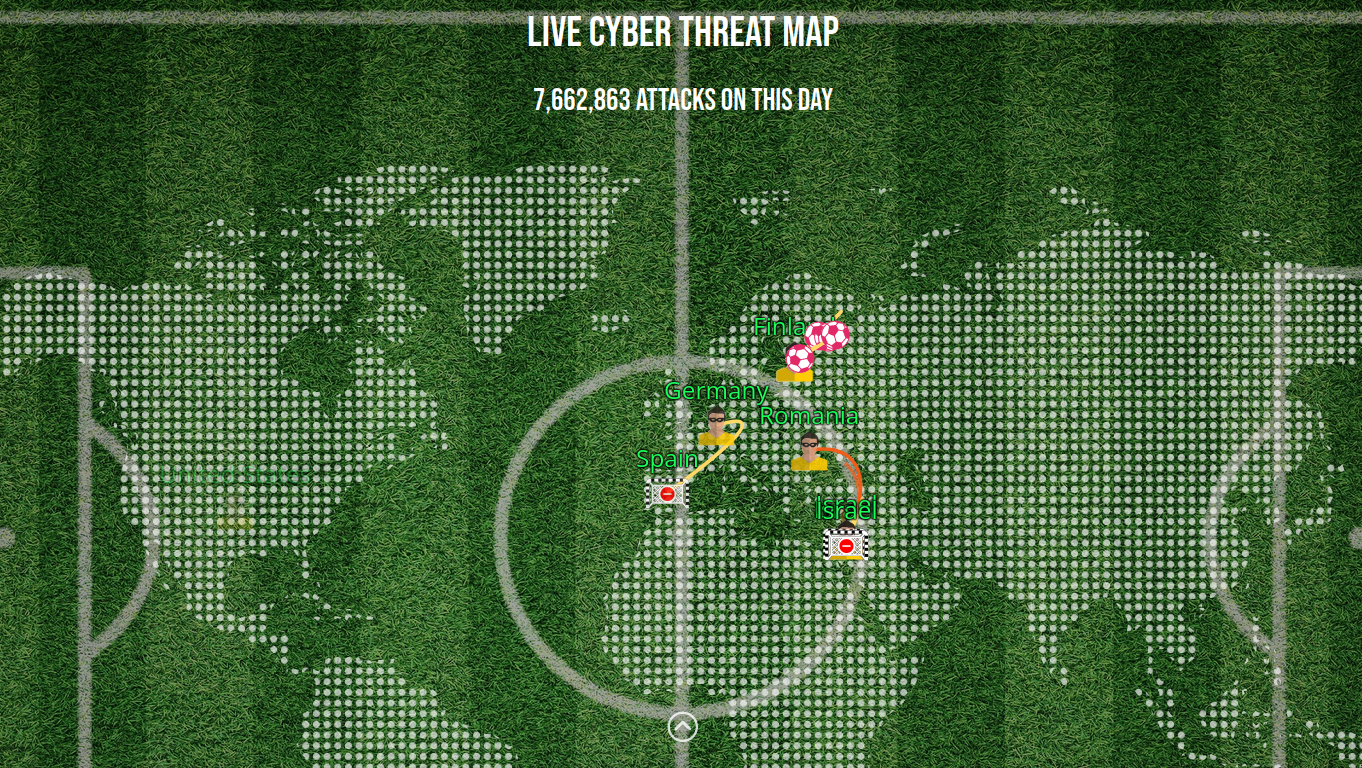
Check Point has created a live cyber threat map themed around the World Cup. This details the volume of attacks, the top targeted countries and industries, and the most used types of malware in the last day. You can see the map here.





