Why FluBot is a major threat to Android users, how to avoid it, and how to get rid of malware if your device is already infected.
The malware Android known as FluBot continues to wreak havoc in some European countries and there is speculation that cybercriminals hiding behind it may decide to strike in other geographical areas, such as the United States.
The FluBot malware targets mainly Android and iPhone users and was first discovered in Spain in late December 2020 by cybersecurity company ESET. Apart from Spain, it has spread to Germany, Poland, Italy and the Netherlands to date, and it is very likely that the cybercriminals behind it will decide to target other countries, including Greece.
From the end of December 2020 until the end of February 2021, the main target of FluBot was clearly the Spanish Android users. By the end of February, an estimated 60.000 Android devices in Spain had fallen victim to FluBot. In addition, more than 11 million telephone numbers, almost all of them Spanish, had fallen into the hands of FluBot operators.
Here's why you need to be careful
If someone falls victim to a malicious attack, then the cybercriminal gains access to his device. This means that the cybercriminal will be able to steal credit card numbers and gain access to the victim's online bank accounts.
So he deceives his victims
The victim first receives an SMS message that appears to have been sent by an acquaintance company logistics services such as FedEx, DHL and, in the case of Spain, Correos.
The message prompts the user to click on a link to download and install an application that appears to belong to the same company as the one that sent the SMS.
It's actually a malicious application that has the FluBot malware built into it. A sample of the SMS message and the application installation message (in German) can be seen below:
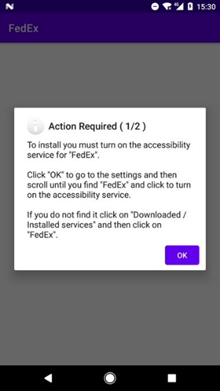

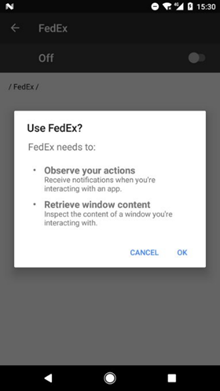
Once installed and licensed, FluBot releases a host of features, including SMS spamming, credit card and credit card number theft, and spyware software.
The contact list is then sent to servers under the control of fraudsters, providing them with additional personal information and allowing them to launch new attacks on other potential victims.
Cybercriminals can get in the way messages SMS και ειδοποιήσεις από εταιρείες τηλεπικοινωνιών, να ανοίξουν σελίδες του προγράμματος browsing and using screen overlay techniques, request and extract credentials.
The malware also disables Google Play Protect to avoid detection by the operating system's built-in security. Also, due to the excessive permissions (permissions) granted, cybercriminals are able to block the installation of third-party anti-malware solutions.
What can you do
If you receive an unknown or unexpected SMS with a link, avoid clicking on the link and delete the message immediately.
If the malware has been installed on a device and banking or other activity has taken place since the installation, contact the interested parties immediately and block access. Also, change passwords where needed - remember to use unique and strong passwords.
It is also worth noting that these tips they'll help protect you from other strains of Android malware as well.
In recent days, cybercriminals have begun targeting Europeans with TeaBot (also known as Anatsa or Toddler). This is a family of Android malware that uses exactly the same technique as FluBot to spread and entice users to disclose their sensitive data.
FluBot and TeaBot are detected by ESET products as variants of the Android / TrojanDropper.Agent family.





