Check Point Research (CPR) observes attempts by Russian cybercriminals to circumvent OpenAI restrictions in order to use ChatGPT for malicious purposes.

In underground forums hacking, hackers discuss how to bypass checks on IP addresses, cards paymentς και των αριθμών τηλεφώνου – όλα αυτά είναι απαραίτητα για να αποκτήσουν πρόσβαση στο ChatGPT από τη Russia. CPR subsequently shares screenshots of its audits and warns of rapidly increasing hacker interest in ChatGPT and escalating malicious activity.
- Scenario #1: Cybercriminal asks what's the best way to use stolen payment card to pay for user upgrade to OpenAI
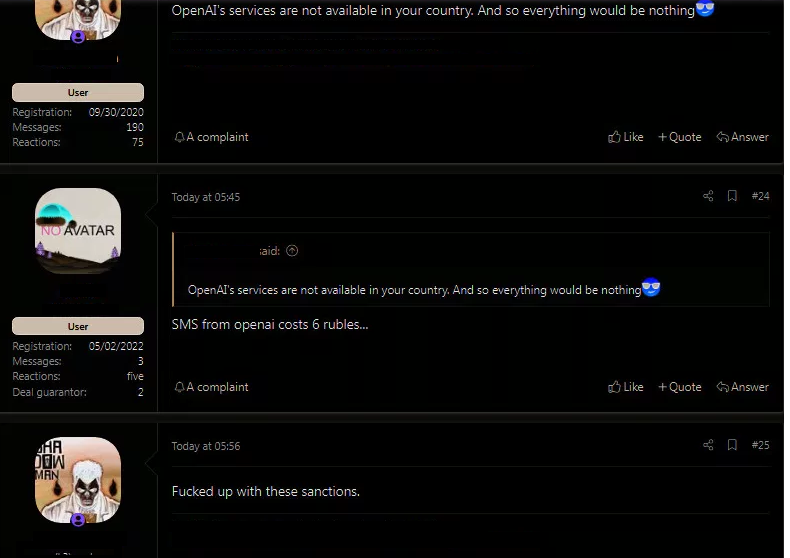
- Screenshot #2: Discussion on how to bypass OpenAI's geo-controls
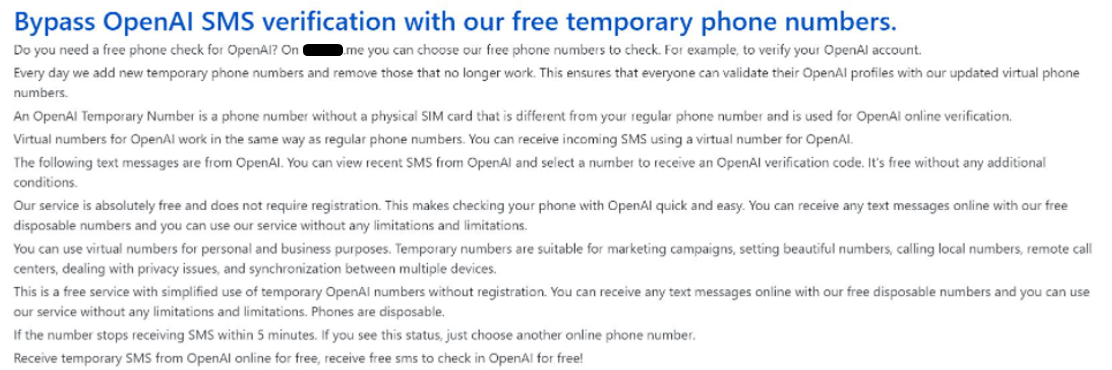
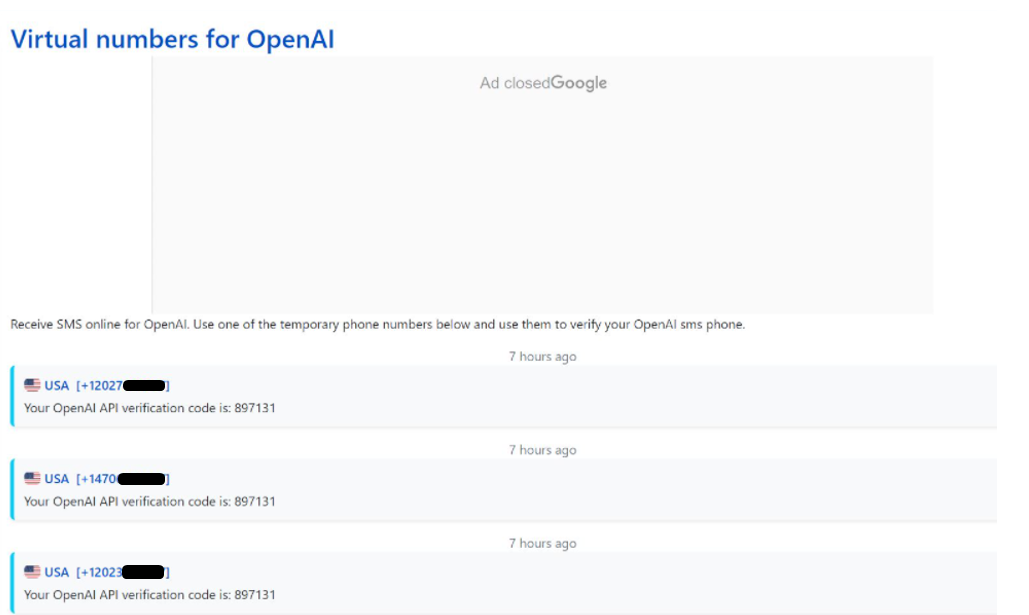
- Snapshot #3: Seminars in Russian semi-legal online SMS services on how to use them to join ChatGPT
Check Point Research (CPR) documents attempts by Russian cybercriminals to circumvent OpenAI's API restrictions. In underground Russian hacking forums, hackers discuss how to bypass the restriction of IPs, payment cards and phone numbers – which are necessary to gain access to ChatGPT.
Sergey Shykevich, Threat Intelligence Group Manager at Check Point Software Technologies, stated:
“It is not extremely difficult to bypass OpenAI's country-specific restrictions to access ChatGPT. Right now, we see Russian hackers discussing and looking for ways to bypass geofencing to use ChatGPT for their malicious purposes. We believe that these hackers are probably trying to implement and test ChatGPT in their daily criminal activities. Cybercriminals are increasingly interested in ChatGPT because the AI technology behind it can make a hacker more cost-effective.”
Screenshots from the Underground Hacking Forum
1) Russian cybercriminals want access to OpenAI API and ask what is the best way to use stolen payment card to pay for upgraded user in OpenAI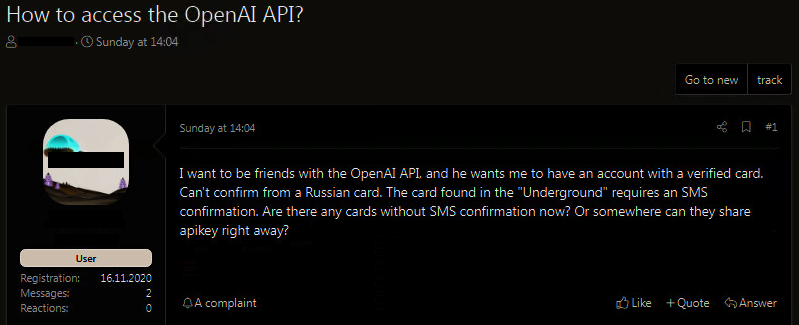
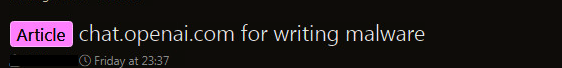
2) Discussion on how to bypass OpenAI's geographic controls
3) In general, there are many tutorials on Russian semi-legal online SMS services on how to use it to register on ChatGPT and we have examples of it already being used :