Most of you know the power of nmap and nmap scripts to identify a target and networks in general. These tools can be used for numerous tasks, from simple port scanning to service and version detection. Despite nmap's power and simplicity, it can be tediously slow for scanning very large networks. This is where the innovative Zmap scanner comes into its own.
Zmap was developed in 2013 by a team of researchers at the University of Michigan (David Adrian, Zakir Durumeric, Gulshan Singh and J. Alex Halderman). It was designed to be able to scan the entire Internet for information security purposes, rather than scanning a single IP or a range of IPs. With a 1 Gigabit connection, one can scan the entire Internet for a single port in about 45 minutes! The same scan would take months using nmap.
This kind of speed opens up all new possibilities for scanning that we couldn't even imagine before. For example, one of the Zmap developers was able to appreciate the vacation power during Superstorm Sandy by scanning all IP addresses in the area of the storm and then inferring from that information which area had power and which did not. In addition, this tool can be used to determine when and how many systems are adopting new technologies around the world. The possibilities of using Zmap seem limitless for estimating the surface of an attack on Internet!
In essence, Zmap can provide us with an almost real-time picture of an Internet attack. That's exactly what a service like CenSys tries to do by using Zmap to collect the data.

Zmap achieves its speed by using cyclic multiplicative groups. This allows ZMap to scan the same things about 1.300 times faster than Nmap (nmap sends probes and waits for the response before sending the next probe).
ZMap takes each number from 1 to 2 to a power of 32 (the IPv4 address space is 32 bits) and creates an iterative formula that ensures that each of the possible 32-bit numbers is visited once in random order.
This speed can also be used for exploitation purposes. For example, when someone is connected to a local network it is relatively simple to use all available bandwidth and create an effective denial state supply of services (DoS). Additionally, hackers are able to search the entire Internet for a specific vulnerability faster than administrators can patch their systems.
Step #1: Open Kali and download Zmap
The first step is to enable Kali and open a terminal.

Now, we need to download and install Zmap. Zmap is in the Kali repository, so all you need to do is type:
kali > sudo apt install mapping
Step #2: We give the Zmap help command
Before we start using Zmap, let's first take a look at the help.
kali > sudo mapping -h
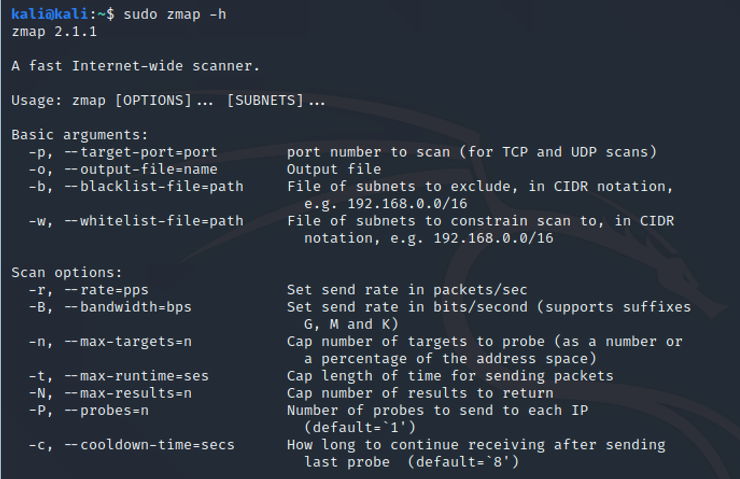
Note here the basic options. You can set the port with -p and the output file with -o. Additionally, you specify the rate and bandwidth with the -r and -B options, respectively.
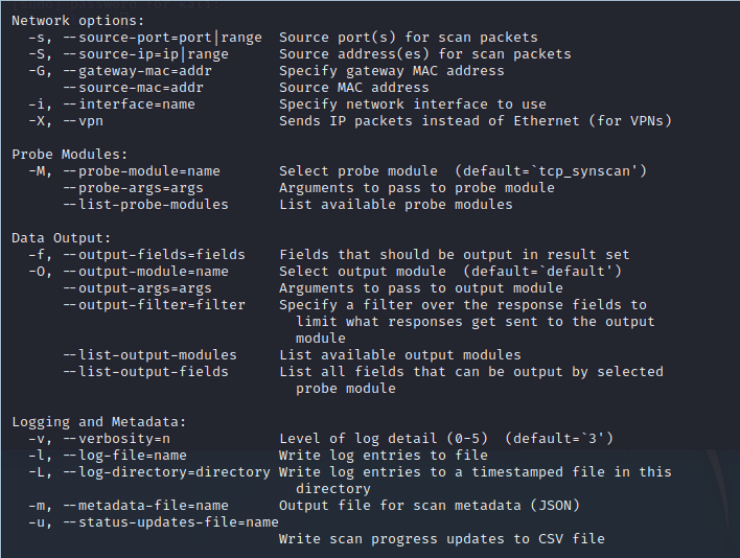
In network options, note that you can specify source port (-s), source IP (-S), gateway (-G), interface (-i) and vpn (-X).
It is also important to note that Zmap uses TCP SYN scanning by default and outputs the results in ASCII format to stdout or to an output file specified with the -o option in .csv format.
Step #3: Run a scan with Zmap
The basic syntax for running Zmap is simple,
mapping -p
So, to scan 255 IP addresses on a Class B network, we issue the following command:
kali > sudo mapping -p 80 172.217.0.0/24 -o IResults.csv
Where:
-p 80 = scan on open port 80
172.217.0.0/24 = scans the 255 IP addresses
-o IResults.csv = send the results to a csv file named IPresults.csv
When we press enter, Zmap starts scanning the IP addresses and displays its results on the screen (stdout).
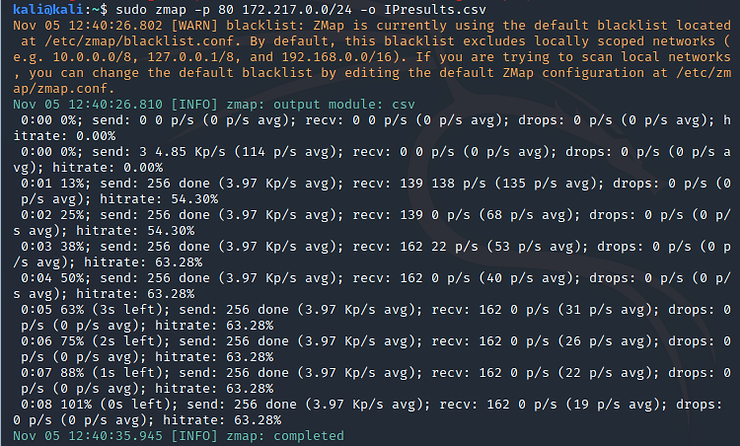
As you can see, Zmap completed the process in a few seconds, while nmap would probably take hours. To see its output, we can type:
kali > moins IResults.csv
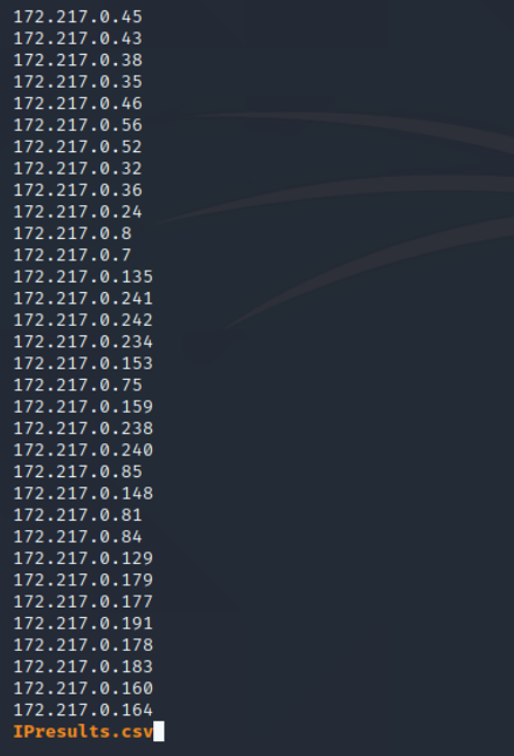
To see the total number of IP addresses on open port 80 in this IP address range, type:
kali > wc -l IResults.csv
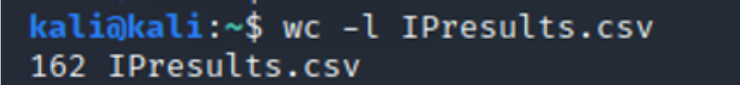
As you can see, Zmap found that 162 IP addresses out of a total of 255 had port 80 open.
Step #4: Scan your local network
Next, let's try using Zmap to scan our local network. We can use the same command and options as above, but let's use a local IP address.
kali > sudo mapping -p 80 10.0.2.15 -o LANresults.csv
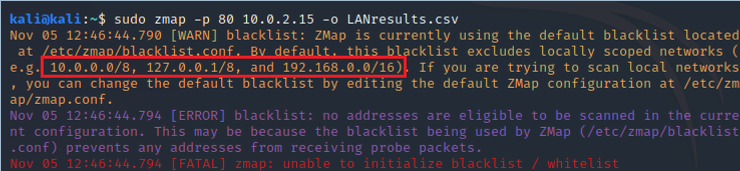
As you can see above, Zmap refuses to scan our local network because - by default - Zmap blacklists all private IP addresses.
We can fix this by simply opening the file blacklist.conf in any text editor and commenting out the IP addresses we want to scan. Zmap's blacklist is on file /etc/zmap/blacklist.conf.
kali > sudo mousepad /etc/zmap/blacklist.conf
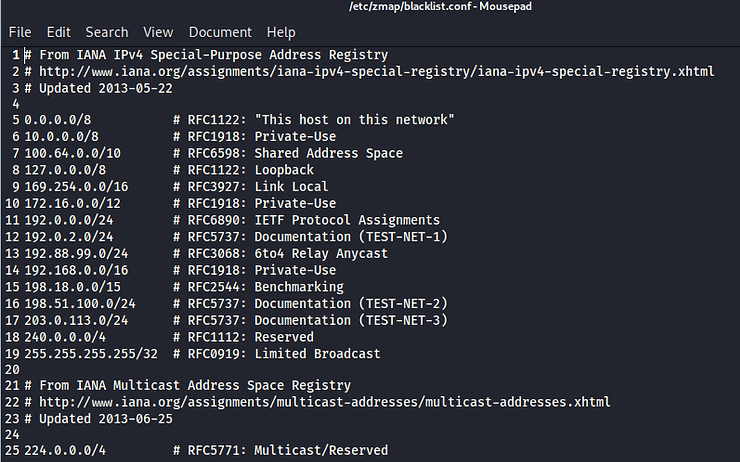
Now, let's try scanning our local network again.
kali > sudo mapping -p 10.0.0.0/16 -o LANresults.csv
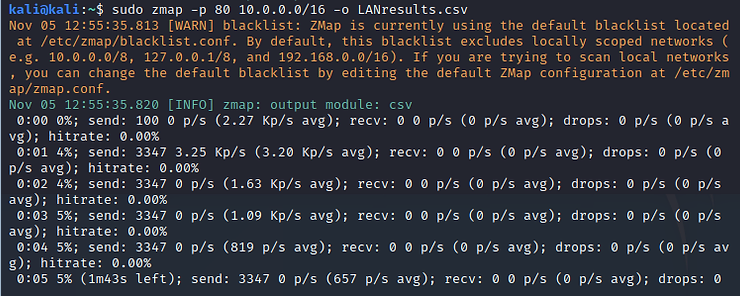
Be careful when using Zmap on your local network. It can easily overload your network and cause a denial of service (DoS) situation. It is recommended to limit the bandwidth used by Zmap to 10k packets per second to avoid saturating the network bandwidth. To do this, simply enter the bandwidth-limit option -B followed by 10M, such as:
kali > sudo mapping -B 10M -p 80 10.0.0.0/16 -o LANresults.csv
Summary
Zmap is a great tool for gathering information about the attack spectrum of the entire Internet or a very large network. While it's useful for quickly scanning large networks where nmap scans would be time-consuming and tedious, its real beauty is its ability to collect information from EVERY IP address spanning the globe. Both cybercriminals and security researchers can gather amazing insights into the global attack surface with this tool.





