Did you know that some of the most devastating Phishing campaigns driven by very powerful cloud-based AI supercomputers? In today's article we will show you how a phishing attack is done and then look at the power behind the modern and highly successful campaigns we face today.
The phishing attacks they happen so often that if you don't know how they work, you'll probably fall victim too at some point. The best way to see what is involved in a phishing attack is to take a look from the idea of the attack to its execution. We'll show you how easy it is to make a good phishing attack and how we can take our attack to another level.

Social-Engineer Toolkit: Fake Twitter login page
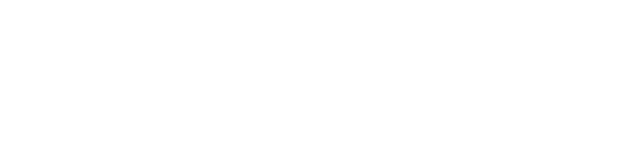
What I'm doing here is simply setting up the Social-Engineer Toolkit. This program automates the creation of a phishing attack and makes it very easy. To begin with, I will select the specific element, which is “Social-Engineering Attacks”. Next, “Website Attack Vectors” and finally I will select the third option, “Credential Harvester Attack Method”.
Next, we'll use Twitter as an example of what we'll try to clone. So, I'm going to go ahead and use “Site Cloner”.
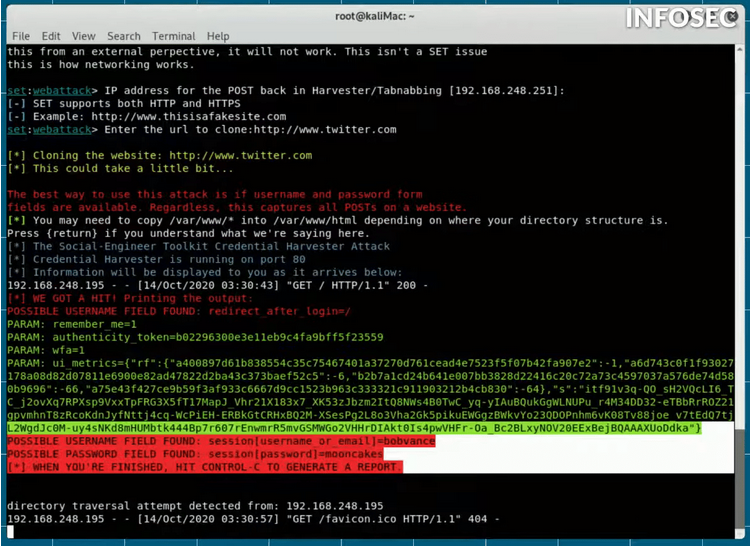
And the IP address that I want my connection to return to is going to be that machine's IP, which is 192.168.248.251. It then asks what I want to clone and I enter the Twitter URL.
Manually send a phishing email
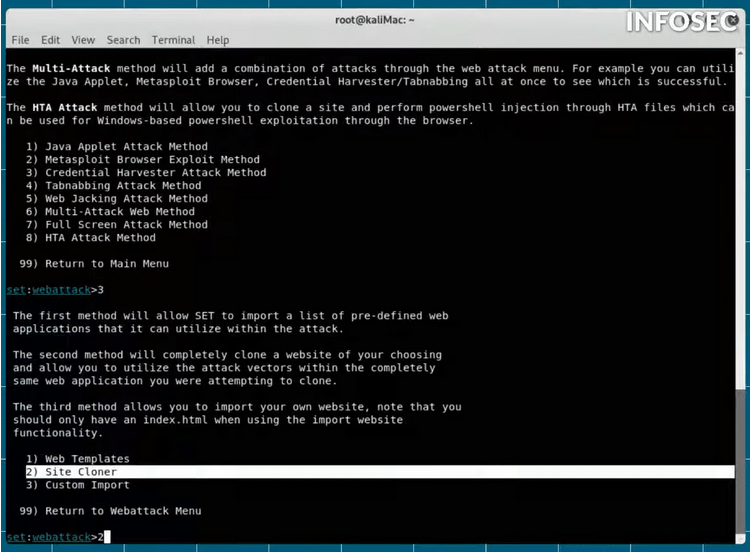
So what happens as a result? I will log into my Gmail account and send the phishing email. So I will craft a nice and fishy message carefully so as not to arouse suspicion.
I'll put it on theme as “new twitter message. As a Subject in the email I can say something like: "did you see what is being posted about you on Twitter?".
So I sent my victim this message. I will make the link visible so you can see the content it points to. I'll just put a link on the machine, “http://192.168.248.251”. Now we could modify it and make it say “twitter.com”. But I want you to see what the link looks like. So we're going ahead and sending this message as is.
How the victim gets their credentials
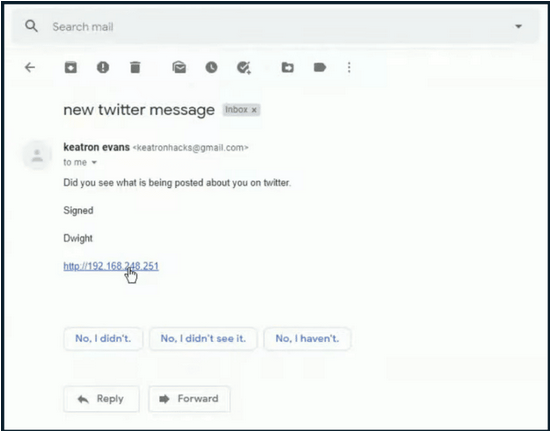
Now we will play the victim. Remember, we're still at procedure of the attack. So we go to the victim's machine. The victim goes and opens their Gmail. In this case, it's Bob.
So Bob logs into his Gmail account. He sees a new message and opens it. He checks to see what people are tweeting about him. He gets there and realizes he needs to log in. So Bob logs into his Twitter account by clicking login.
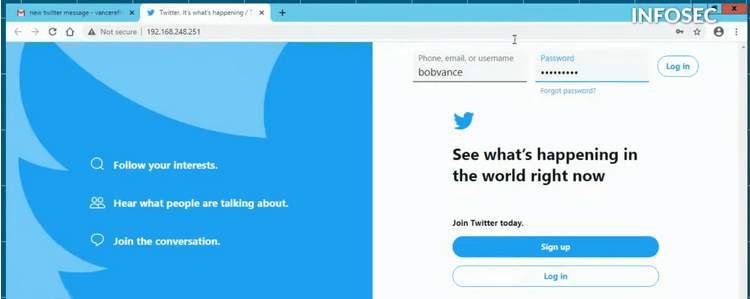
Then the victim puts in their email and password, what we see from the attacker's side and below you see how things look from the attacker's side.
Using machine learning and AI in phishing attacks
An easy technique and simple that we could certainly expand it to 100.000 people easily and quickly. But what happens when we have 100.000 responses to manage instantly and find out who clicked?
What if we could read those 100.000 responses in real-time and within a millisecond construct another attack based on the feedback and kill everyone again using that AI? Then repeat this over and over, achieving a higher hit rate with each attack.
This is where machine learning comes in. APT teams now use machine learning algorithms combined with massive computing power to execute these highly effective campaigns. This is made possible by cloud service models.
First, they create training models that will be trained based on feedback from phishing attempts. Then the phishing attacks begin. Once the answers come back, all these data fed into cloud servers designed to efficiently manage massive amounts of data. We're talking about 1.000 machines with four terabytes of RAM, for example. This is where machine learning and massive computing power from cloud servers are critical.
After all the answers are calculated and passed through machine learning models, the results are generated and recycled through machine learning. Immediately everyone will be phished again and this process will be painfully effective.
We could do all this manually, but it would waste a lot of time. This is one of the main reasons why phishing attacks today are so effective and improving so quickly.
This is also why it's important to make sure that if you're trying to defend against them, you're using something that can match the power and intelligence of these machine learnings. It's also important to make sure you're using a phishing testing solution capable of mimicking this behavior.