Do you use Skype; A new trojan that has started circulating comes equipped with characteristics which allow it to intercept files, take screenshots, and record Skype conversations.
The trojan, called T9000, is a development of the older version of T5000, found on the internet by 2013 and 2014. At that time, it targeted human rights activists, automakers, and governments in the Asia-Pacific region.
This time, Palo Alto Networks researchers report that the new T9000 has been detected in US phishing emails and that it is flexible enough to be used against any target that an attacker wants to violate.
The malicious λογισμικό μολύνει τους υπολογιστές μέσω κακόβουλων αρχείων .RTF που εκμεταλλεύονται τα τρωτά σημεία CVE-2012-1856 και CVE-2015-1641 για να εισέλθουν στον υπολογιστή του χρήστη.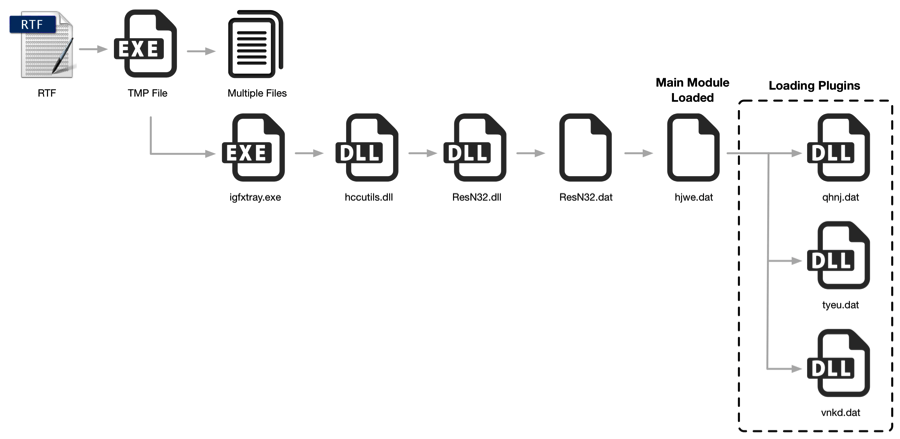
Compared with its previous version, T9000 is much more complex. Security investigators who analyzed it report that malware developers have tried hard to avoid any anti-virus detection.
The T9000 has a multi-step installation process, which checks before each phase for analysis tools from 24 security products, including: Sophos, INCAInternet, DoctorWeb, Baidu, Comodo, TrustPortAntivirus, GData, AVG, BitDefender, VirusChaser, McAfee, Panda , Trend Micro, Kingsoft, Norton, Micropoint, Filseclab, AhnLab, Jiangmin, Tencent, Avira, Kaspersky, Rising, and Qihoo 360.
This avoids detection. Once installed, the malware starts collecting the first information from the infected system and sends it to a C&C server (server or control server).
Once the infected computer is detected and logged on to the C&C server, it will start sending specific modules for each target, based on the information it received. Palo Alto researchers have identified three key modules.
The most important of them (tyeu.dat) is responsible for recording all conversations that take place in Skype chats. Once the specific module has been downloaded to the infected computer, the next time the user starts Skype, a message at the top of its window it says: "explorer.exe wants to use Skype".
 The message appears because the trojan is requesting access to the Skype API. Users who agree to allow "explorer.exe" to interact with Skype actually give the T9000 all the rights it needs to spy on them.
The message appears because the trojan is requesting access to the Skype API. Users who agree to allow "explorer.exe" to interact with Skype actually give the T9000 all the rights it needs to spy on them.
The T9000 records audio conversations, videos, along with text chats, as well as regular screenshots of video calls.
The second module of T9000 (vnkd.dat) is loaded only when the attacker wants to steal files from the victim's computer. The module can intercept files from the disk and from local removable storage devices with extensions such as doc, ppt, xls, docx, pptx, and xlsx.
The most "innocent" module is qhnj.dat, which is responsible for communicating the infected computer with the C&C server.
Those interested can read the full analysis on the Palo Alto page





