A new targeted attack has been detected, via TeamViewer, targeting her theft financial information from government and financial targets across Europe and beyond.
Check Point researchers announced on Monday that the attacks targeted government and financial officials, as well as representatives of various embassies in Europe, Nepal, Kenya, Liberia, Lebanon, Guyana and Bermuda.
Η επίθεση ξεκινούσε με ένα τυπικό ηλεκτρονικό μήνυμα phishing το οποίο περιείχε ένα κακόβουλο συνημμένο που ισχυρίζεται ότι ήταν ένα "άκρως απόρρητο" έγγραφο από τις Ηνωμένες Πολιτείες.
Η γραμμή θέματος ανέφερε "Πρόγραμμα Στρατιωτικής Χρηματοδότησης" και το έγγραφο .XLSM διέθετε το logo του Υπουργείου Εξωτερικών των USA.
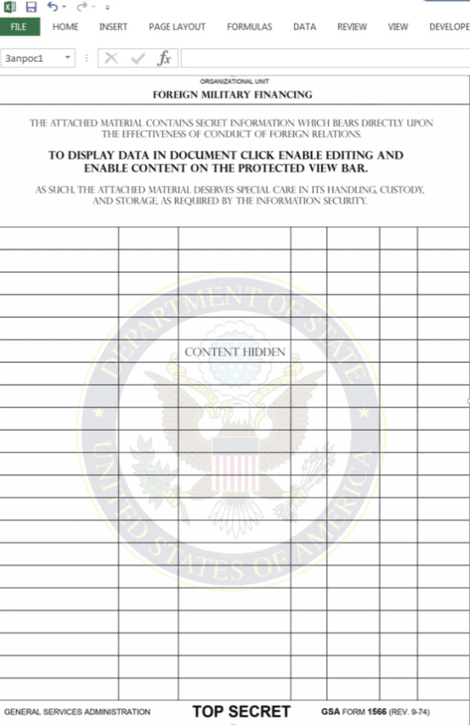
Αν λοιπόν κάποιος άνοιγε το έγγραφο και ενεργοποιούσε τις μακροεντολές, έβγαιναν δύο αρχεία - ένα κανονικό πρόγραμμα AutoHotkeyU32.exe και ένα κακόβουλο TeamViewer DLL.
The AutoHotkeyU32 program was used to send a POST request to the server orders and control (C&C) of the attacker, but also to download more malicious scripts that were capable of taking snapshots of screenof the target computer, to steal information and then send it to the attacker.
TeamViewer is often used by businesses for remote PC access. However, due to its capabilities, the software is also used by scammers to gain access to remote systems.
The malicious variant with TeamViewer DLL provided attackers with modified functionality, and hid any connection to TeamViewer. So the victims did not know that someone was connected to their computer.
The main targets of this attack as mentioned above were public financial sector players and according to the researchers the would-be hacker was a Russian.
_________________
- GR and EL domains: Attack to the Greek Internet Name Registry
- Windows 10 Fall Creators support fee immediately upgrade
- Mathesis: Ancient Greek Technology 1 (Basic Technologies)
- Edge with Chromium allows video streaming on 4K
- Mark Zuckerberg: help from regulators & governments





