Do you know what a VPN tunnel is? You may have heard of it, but do you understand exactly how it works? Let's dive into this topic.

Probably already know about VPNs (Virtual Private Networks) and how essential they are to staying safe on the world wide web.
However, exactly how they work can be a bit murky to the average user. If we look at how they work, how they work and the different types you might come across.
What is a VPN tunnel?
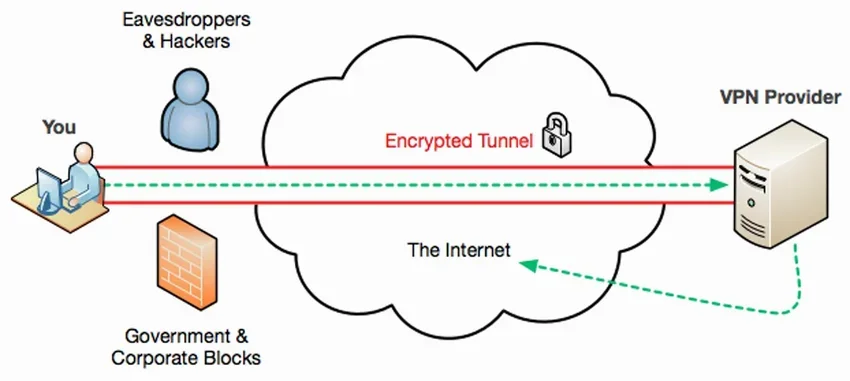
When you connect to the internet using a VPN, you create one secure link to transfer information between your device and the world wide web.
This link is called VPN tunnel (in Greek VPN tunnels) and encrypts and encapsulates every bit of your data, making it unreadable to anyone who doesn't have the specific decryption key.
It's almost like using a personal courier instead of the public ones services mail, except that this courier translates and delivers each letter to you in a language that only you understand. So even if someone steals or tries to read your mail, you have nothing to worry about!
Or almost nothing. How secure your information really is depends on the encryption protocol your VPN uses, i.e. the language your courier used to translate those letters.
In short, VPN tunnel is not a train tunnel, but the process of building a secure encrypted connection from your computer to a server. From there, the data is decrypted and delivered to its destination.

The actual process of Tunneling is as follows: It makes an encrypted packet and puts the original packet inside it, before it is transmitted over the internet. This outer packet protects the contents from public view and ensures that the packet moves within a virtual tunnel.
This layering of packets is called encapsulation. Computers or other network devices at both ends of the tunnel, called tunnel interfaces, can encapsulate the outgoing packets and re-open the normal packets.
And it was called a tunnel because it has the meaning of a short route, like a tunnel that goes through a mountain and connects two points, without having to go around the mountain. So is a VPN tunnel, it is a tunnel specifically designed to connect two private networks without the burden of translating IP addresses between private and public addresses at each end.
And it is a tunnel and not a bridge or something else, since it encrypts, that is, it hides the train in relation to a bridge that the whole world can see. Okay, metaphorical concepts that someone inspired.
There are different protocols with different use cases and security levels, which we will explore below. But first, let's take a closer look at the entire process.
How does a VPN tunnel work?
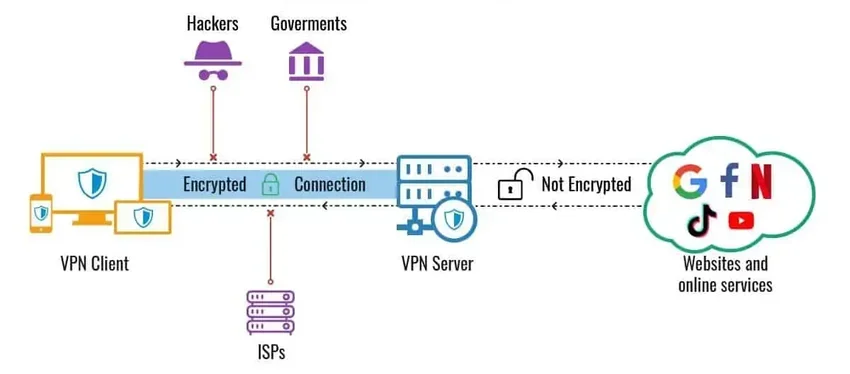
When you click on links or download files on any website, you send requests to receive information in return. When unsecured, these data requests travel from your device to your Internet Service Provider (ISP) before reaching the web and getting you what you requested.
In this way, your ISP, and any intermediary, can potentially spy on your connection, can see and identify the different parts of your information flow, and later use or sell them for extra profit.
To avoid this, you should use a VPN that creates a secure connection through a VPN tunnel to one of its servers.
Usually you download a small application (client) of the VPN Service, install it, run it and it takes care of talking to its servers services VPN. And so the process is:
step 1: You send a request to create a VPN tunnel through the client of the VPN service to one of its servers.
step 2: a negotiation takes place between your device and the VPN server, where they identify each other and verify what security measures to put in place.
step 4: They build a VPN tunnel that will transport your data.
step 5: Through the established tunnel, encrypted data travels to and from the internet that even your ISP can't see.
step 6: After a specified amount of time or information has passed, the tunnel expires and terminates automatically. If you still need to maintain a connection, a new process will start from Step 1.
Although the process may seem a bit long, it usually doesn't take long to make your internet connection more secure. The question, then, is how secure a VPN tunnel actually is. And the answer depends on the tunneling protocol.
VPN protocols

While all VPN protocols aim to secure data transfer between different networks, not all have the same strength and some sacrifice some security to gain speed, simplification, etc. But each has its pros and cons.
The truth is, there aren't that many good VPN protocols that we use widely today, but here are the main ones you'll likely come across.
SSTP: Non-open source, secure encryption, high bandwidth.
PPTP: Fastest, insecure encryption, outdated. If any vpn service uses it just avoid it.
L2TP/IPsec: Problematic in control procedures, slow, obsolete.
Shadow Socks: Open source and under continuous development, relatively fast, secure.
openvpn: Strong security, medium speed, open source, secure encryption.
IKEv2: Strong security, fast, high encryption technology, highly recommended, especially for mobile.
wire guard: Strong security, newest in class, open source, high speed.
When you can choose which protocol to use for VPN tunneling then for web browsing on a desktop or laptop, the WireGuard and OpenVPN protocols are generally good choices in terms of speed and security.
Depending on your location and VPN server availability, IKEv2 may be better if you're connected via mobile. Overall, most VPN providers offer one or two protocols, depending on the situation.
Split VPN tunnel

Split tunnel VPN allows you to choose which sites or applications will use a VPN tunnel and which ones should be left out.
This feature is useful when, for example, you want to pass everything through the VPN except your bank app. Thus, everything is protected and your bank will not block transactions from another country.
Or watch a show that is only available in your country and have all other surfing done via VPN. Another example would be using your office printer while torrenting with a VPN.
Not all VPN providers offer this feature. Even if they do, chances are that split tunneling is only available on certain devices and operating systems. So always check your options before making a long-term commitment.





