Two academics finally managed to get permission to publish a security research, which reveals the vulnerabilities in a wireless car locking system. Two years ago, Volkswagen, one of the carmakers using the fragile product, won a lawsuit that banned the publication.
Today, despite the court decision, Volkswagen has given permission to publish the vulnerability with minor variants. However, this case reveals the tension between security researchers and automakers.
While some companies such as Facebook, Google and Microsoft offer financial rewards to those who find bugs in their products or infrastructure, others, such as Fiat Chrysler who claim that this activity is criminal and just as Volkswagen did, are targeting in the courts - while not dealing with problems that expose customers to risk.
The automotive industry may feel intimidated, but Volkswagen's approach through the legal road, which is essentially trying to keep the information inside the walls, looks like it closes its eyes in the hope that everything will go well.
This, of course, as you understand, is a serious matter that becomes even more serious with the involvement of the courts. In any case, the Internet has little national boundaries and we have often noticed information appearing, irrespective of the court's decision.
We are talking about a new era, when information is flowing and there seems to be nothing that can stop it. Especially a piece of information concerning her better safety of the public, should probably be approached with other criteria than the judicial authorities.
From where everything started.
Το Megamos είναι ένας αναμεταδότης ασύρματων κλειδιών. Η κρυπτογράφηση που usesται από την Ελβετική εταιρεία που κατασκεύασε το Megamos είναι τόσο αδύναμη που ένας εισβολέας χρειάζεται μόνο να ακούσετε δύο μηνύματα του ήχου που εκπέμπει το κλειδί, και μπορεί να τη σπάσει.
The vulnerability exists in the weak cryptographic methods used by the device, and the researchers found that they could very easily generate the 96-bit (!) key used by the transceiver. So they can get every car which uses him in less than half an hour.
The vulnerability has been known since 2012, however, there has been no recall of the product from dozens of models from companies such as: Audi, Porsche, Bentley, Lamborghini, Nissan and Volvo using the device.
RollJam is currently available (available online and costs 20 pounds) and can unlock many well-known car brands. It also opens garage doors and deactivates some of the alarm systems.
Academic freedom against the interests of industry
Researchers who now have the right to publish vulnerability, Roel Verdult and Barıs Ege from Radboud University in Netherlands and Flavoi D Garcia of the University of Birmingham approached the maker of May 2012, explaining that they intended to present the their findings at the USENIX 2013 conference, while giving him the time to solve the problem. However, Volkswagen has used court instruments to prevent the publication of the document, and has succeeded in banning the freedom of academic publishing.
Table of models affected.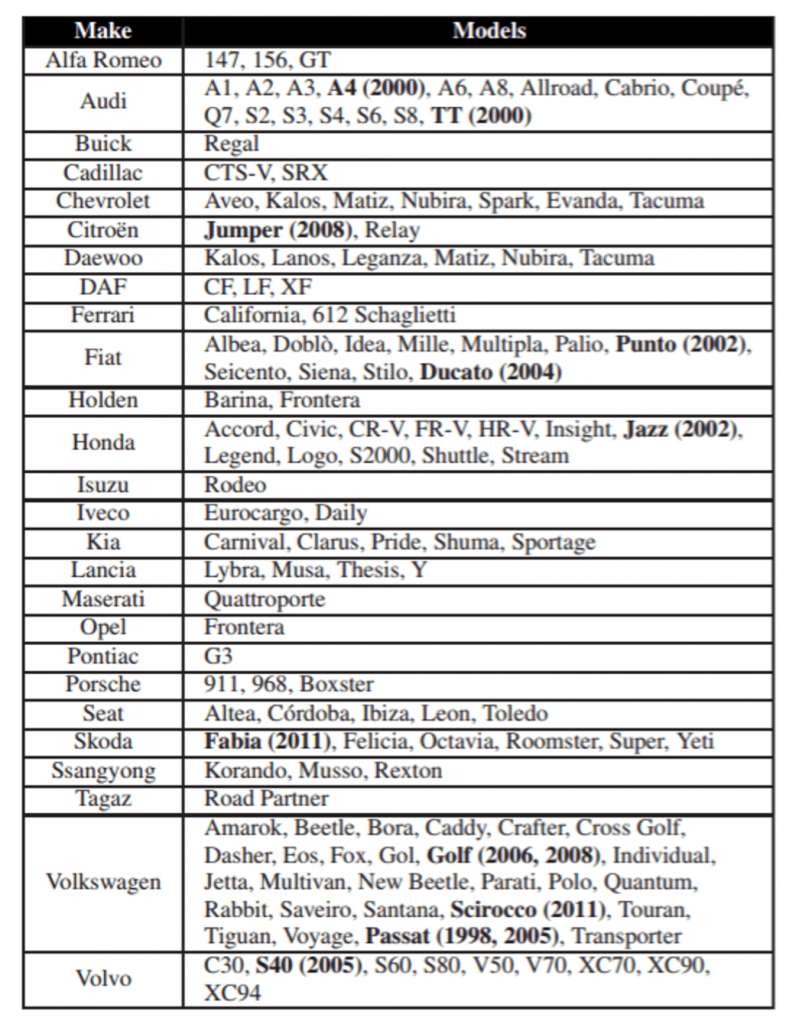
This sad story of the academic ban on academics, with a court order of silence, shows how "relevant" to the internet and security was the seat of the court. Regardless of the huge cost of recalling the defective product charged by Volkswagen to obtain the disclosure ban, the court should have regard to public safety, freedom of speech, and, more generally, freedom of scientific publication.
All this seems to have been set aside for a financial cost… Of course we have seen similar ways of silencing on the part of governments, but this is another chapter.
Information from TNW





