ESET Research found that more than ten different groups of APT (advanced persistent threat) exploit its recent vulnerabilities microsoft Exchange to violate email servers.
ESET identified more than 5.000 email servers affected by malicious activity related to the incident. The servers belong to organizations - businesses and governments - from all over the world.
Beginning of March, Microsoft has released updates (patches) για το Exchange Server 2013, 2016 και 2019 που επιδιορθώνουν μια σειρά ευπαθειών απομακρυσμένης εκτέλεσης κώδικα (RCE).
Vulnerabilities allow an attacker to gain control of any accessible Exchange server without the need for account credentials, making Internet-connected servers particularly vulnerable.
“The day after the updates were released, we started noticing a lot maliciousυς παράγοντες να σαρώνουν και να επιτίθενται μαζικά σε Exchange servers. Είναι ενδιαφέρον ότι όλοι είναι ομάδες APT που επικεντρώνονται στην κατασκοπεία, εκτός από έναν που φαίνεται να σχετίζεται με μια γνωστή εκστρατεία miningof cryptocurrencies. However, it is inevitable that sooner or later more and more cybercriminals, including ransomware administrators, will exploit the vulnerabilities," says Matthieu Faou, who leads ESET's research effort.
ESET researchers observed that some APT groups exploited vulnerabilities before the release of the updates. "Which means we can rule out the possibility that these groups created a reverse engineering exploit based on Microsoft updates," Faou added.
ESET's telemetry onsignalne the presence of webshells (malicious programs or scripts that allow remote control of a server through a web browser) on more than 5.000 servers in more than 115 countries.
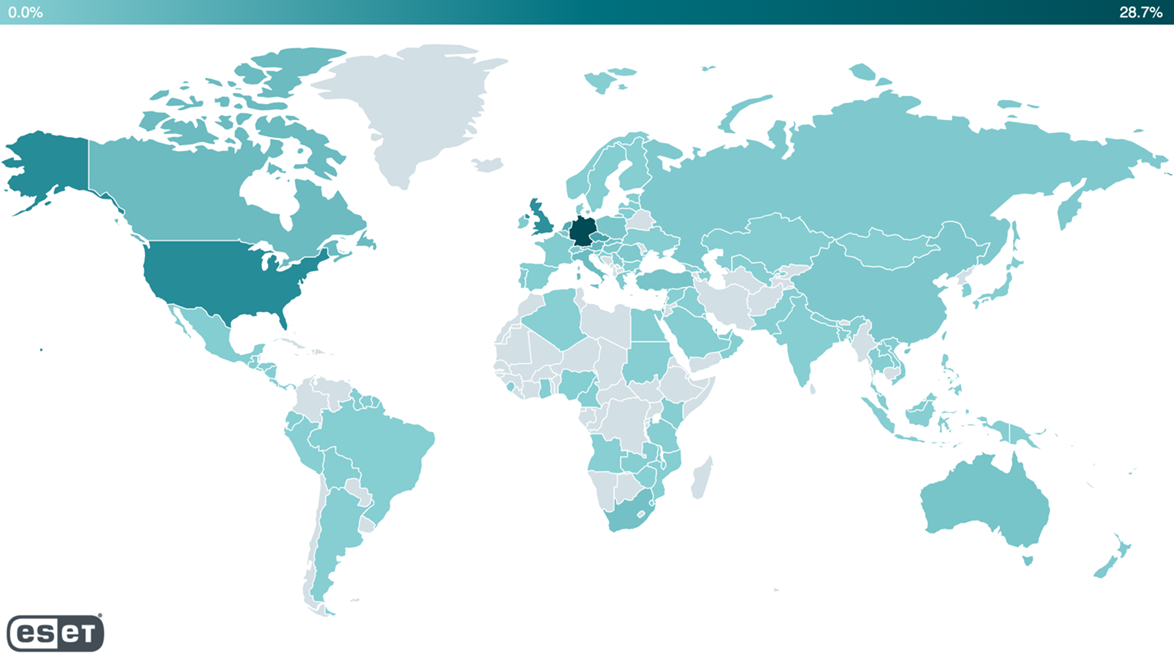
ESET has identified more than a dozen different cybercriminals who may have exploited Microsoft Exchange's recent vulnerabilities to install malware such as webshells and backdoors on victims' email servers. In some cases, different groups target the same organization.
The APT groups are: Tick, LuckyMouse, Calypso, Websiic, Winnti Group, Tonto Team, ShadowPad activity, The “Opera” Cobalt Strike, IIS backdoors, Mikroceen and DLTMiner
"It is now clear that we need to update all Exchange servers as soon as possible. Even those who are not connected directly to the internet. In the event of a breach, administrators should remove webshells, change credentials, and investigate any additional malicious activity. "This is a great opportunity to remember that complex applications such as Microsoft Exchange or SharePoint should not be open on the Internet," Faou advises.
For more technical details on attacks that take advantage of recent Exchange vulnerabilities, read the blogpost “Exchange servers under siege from at least 10 APT groups”At WeLiveSecurity.





