Η Check Point Research (CPR) observes the new campaign maliciousy software that exploits the verification of its digital signature Microsoft to steal sensitive information of the victims. 
By name ZLoader, malware is a banking software trojan that uses web injection to steal cookies, passwords and any sensitive information.
The ZLoader it has become known that in the past it has carried ransomware and was found on her radar CISA in September 2021 as a method responsible for its distribution Conti ransomware. During the same month, the Microsoft stated his operators ZLoader bought ads with its keywords Google to distribute various malware executives, including Ryuk ransomware.
Today, the CPR publishes a report detailing its reappearance ZLoader in a campaign that has taken over 2.000 victims in 111 countries. THE CPR attributes the campaign to the cyber criminal group MalSmoke.
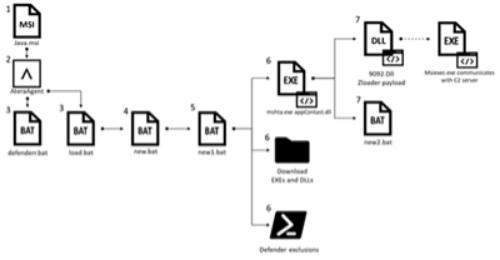
Infection chain
1. The attack begins with the installation of a legitimate remote management program that pretends to be an installation Java
2. After this installation, the perpetrator has full access to the system and can upload / download files and also execute scripts, so the attacker uploads and executes some scripts that download more scripts that run the mshta.exe with the file appContest.dll as a parameter
3. The file appContest.dll is signed by Microsoft, although more information has been added to the end of the file
4. The additional information downloads and executes the final payload zloader, stealing user credentials and personal information from victims
Figure 1. Simplified picture of the infection chain
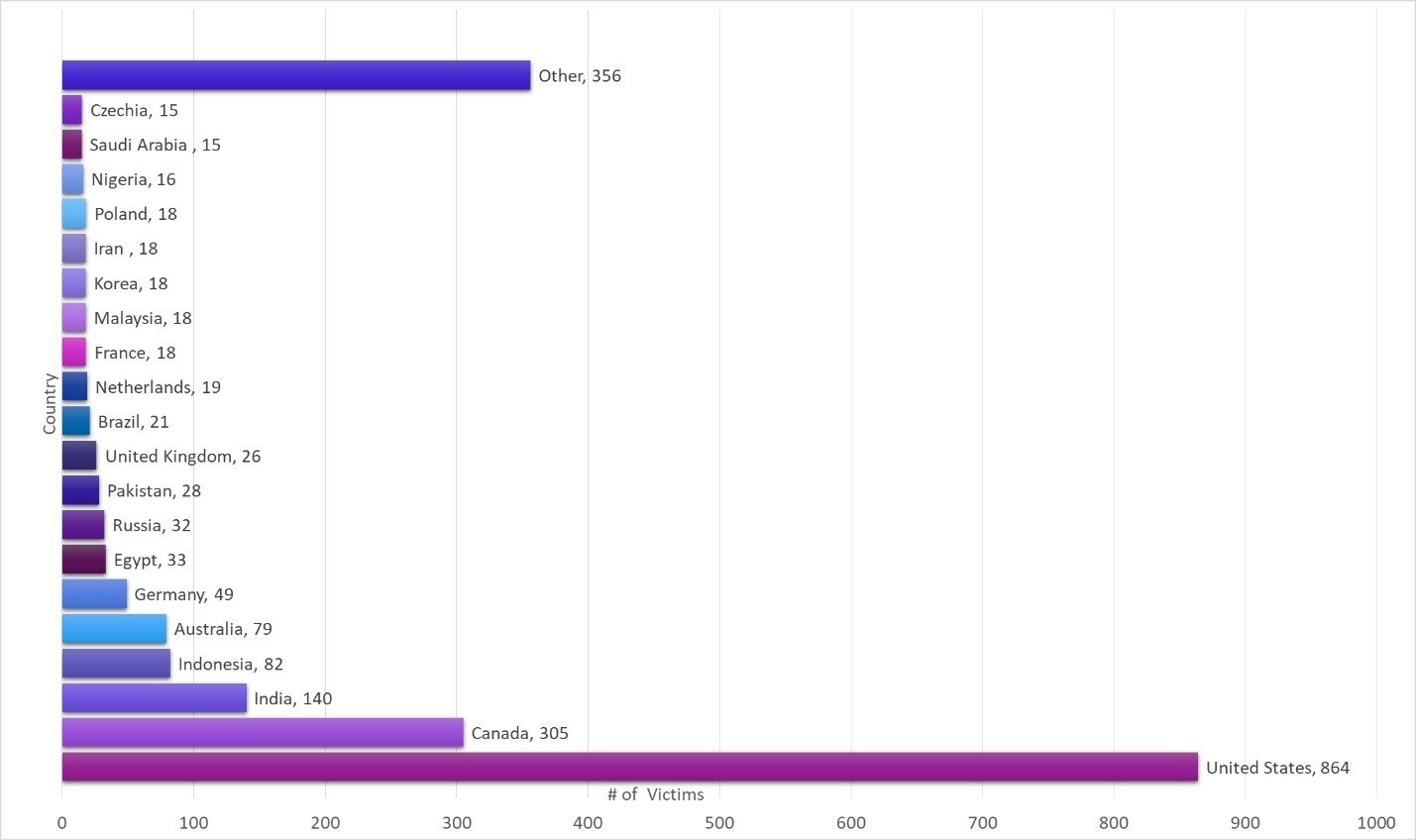
Victims
So far, the CPR has recorded 2170 unique victims. Most of the victims live in the United States, followed by Canada and India.
Figure 2. Number of victims per country
Report:
CPR estimates that the cybercriminals behind the campaign are Malsmoke, given some similarities to previous campaigns.
Revelation:
CPR informed Microsoft and Atera of its findings.
Ο Kobi Eisenkraft, Malware Researcher of Check Point said:
“People need to know that they cannot immediately trust the digital signature of a file. What we found was a new ZLoader campaign that exploits Microsoft's digital signature verification to steal sensitive user information. We started seeing each other for the first time data of the new campaign around November 2021. The attackers we attribute the attack to are MalSmoke, who seek to theft διαπιστευτηρίων χρηστών και προσωπικών πληροφοριών από τα θύματα. Μέχρι στιγμής, έχουμε μετρήσει πάνω από 2.170 θύματα σε 111 χώρες και συνεχίζουμε. Συνολικά, φαίνεται ότι οι δράστες της εκστρατείας Zloader καταβάλλουν μεγάλη προσπάθεια για την αποφυγή του εντοπισμού και εξακολουθούν να ενημερώνουν τις μεθόδους τους σε εβδομαδιαία βάση. Προτρέπω τους χρήστες να εφαρμόσουν την ενημέρωση της Microsoft για αυστηρή επαλήθευση Authenticode, καθώς δεν είναι εγκατεστημένο από προεπιλογή”
Security tips
1. Apply the Microsoft Update for strict Authenticode verification. Not applicable by default.
2. Do not install programs from unknown sources or sites.
3. Do not open links and unknown attachments that you receive by mail.





