It is always important to protect our system against external threats, ie hackers, but it is also important to protect against internal threats.
The magnitude of the damage from an internal threat can be estimated by the example of Edward Snowden, who had worked at the NSA, and had access to thousands of secret documents in NSA networks and systems.
« According to a recent report According to Verizon, internal threats account for about 14% of 2013 data breach cases.
To avoid the risk of malicious employees who abuse sensitive data, CloudFlare released one software open code encryption named “Red October"[ Red October ] , with encryption - decrypt files in style “rule of two-man”[Two-man rule].
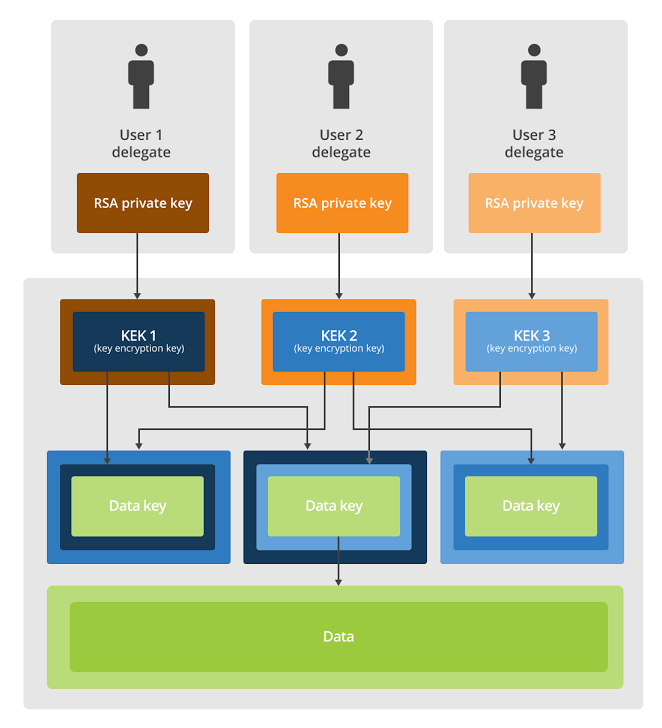
THE "a two-person rule", Is a control mechanism that aims to achieve a high level of security for particularly critical information, such as military secrets, where data decryption will only work when two or more people provide the keys.
"It comes from military history, where a nuclear missile could not be launched if two people did not agree to turn their start keys at the same time. This demand was introduced in order to avoid any mistake of a person (or deliberately) that would start the Third World War. "
All communication with the system "Red October ” is encrypted with TLS, ensuring that passwords are not sent without security.
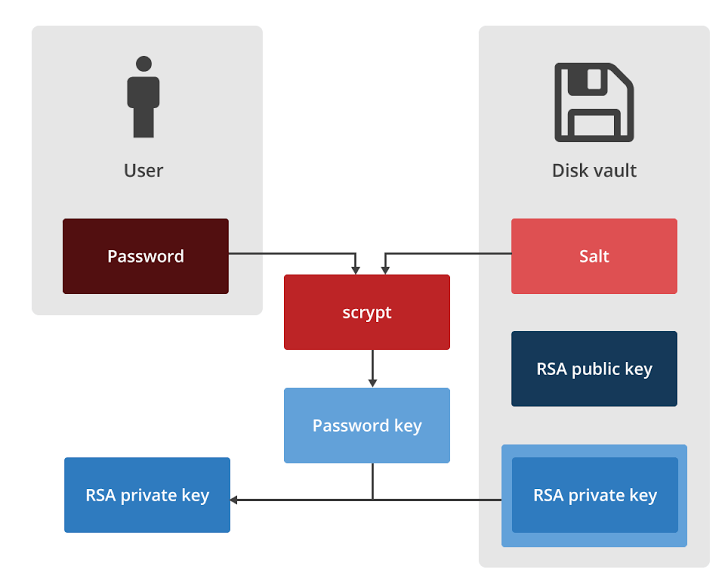
Each user has a unique, randomly generated RSA key pair. The user's private key is then encrypted with another key derived from the user's password and then salt using scrypt. Data encryption Red October creates a random 128-bit AES key.
To decrypt a file, the end user should be the administrator with the correct password. If two end users are on the list of valid users, having passed their keys, then only decryption will be done.
To prevent unauthorized access to data decryption, the Red October server will not decrypt the user's keys without their password.
We know it, hard for all this and for some incomprehensible but safe. If you want to upload your data to a cloud then you have to think about how to preserve something that is not in your home.
The software is freely available as an open source application on GitHub .