Αν νομίζετε ότι ένας υπολογιστής που δεν είναι συνδεδεμένος σε δίκτυο, δεν έχει κάποιο USB sticks που να συνδέεται με αυτόν και δεν δέχεται κανενός είδους ηλεκτρονική αίτηση connectionς, είναι αρκετά ασφαλές από χάκερ και από όλα τα κακόβουλα προγράμματα, τότε κάνετε λάθος .
We inform you that German scientists have developed a theory that some malware could allow a hacker to infect your computers and other digital devices using only audio signals.
Just imagine, a cyber attack using high frequency sound waves to infect machines, but also stolen data that can also be transmitted back to the attacker without a network connection. Sounds too scary?
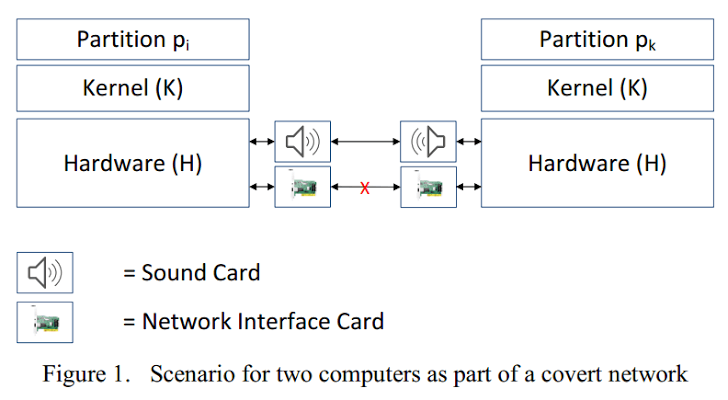
But now German researchers have publish a document on how malware can be designed to cross the air by transmitting information through the speakers and recording through the microphone.
Instead of relying on TCP-IP, they used a stack network originally developed for underwater communication and the signal is propagated through the use of a modem software.
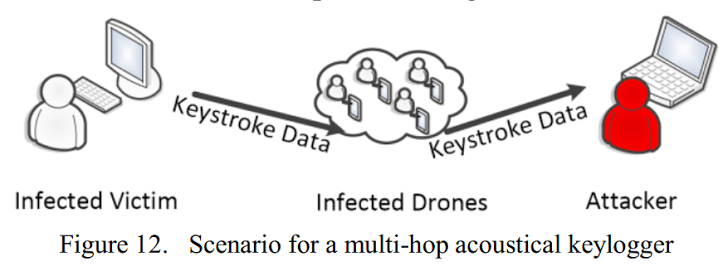
In a possible hacking scenario it could: “The infected victim sends everything recorded on the keyboard to a disguised grid of the acoustic network. Contaminated other computers transmit the information inside the secret network until it is received by the attacker, who is now able to read what the infected victim has typed from a distant placeExplained the researchers.
In another project, researchers used sound waves to send information to a computer connected to a computer network, which then sent the information to the attacker via e-mail.
Researchers of POC Malware are able to transfer data to 20 bits per second, a speed that is particularly low but capable of transferring your password or credit card number to the hacker within seconds.
It looks like science fiction film and maybe some that we sit down and talk about something that can be done in 10 years. But we remind you that computer technology is growing rapidly and perhaps unreachable. What today may seem unbelievable may in a month already be operating somewhere in the world. Remember what you said when we suggested you before 1 time to cover your camera because there is a virus that can turn it on and send your images to hackers.
However, some basic countermeasures that one can take to protect oneself from this type of malware are:
- Απενεργοποίηση των συσκευών εισόδου και εξόδου ήχου από το system.
- Filter audio that blocks high frequency or non-audio frequencies.
- Using a monitor - sound detector.
Let's see how the antivirus companies will handle these threats to protect home users in the near future.