Checksum is a sequence of numbers and letters used to control the data for errors.
If you know the Checksum of an original file, you can use a control utility to confirm that the copy on your computer is the same.
To create a Checksum, you are running a program that checks the file for an algorithm. The typical algorithms used are MD5, SHA-1, SHA-256 and SHA-512.
The algorithm uses a cryptographic hash function that produces a string (sequence of numbers and letters) of constant length. The file you can check can be from 1 MB or some huge file in GB. But regardless of the size of the file, you will end up with a checksum of the same length. Checksums can also be called "hashes".
Small changes to the file can create very different checksums. For example, in two text files that are nearly the same, if a dot changes in exclamation, it produces different checksums.
When Checksum is useful
You can use the checksums to check your files for errors during a file transfer or storage. For example, in case of network problems when transferring a file or problems on your hard disk could cause damage to that file. So if you know the checksum of the original file, you can check it. If the checksums agree, you know that the file you saved is identical to the original.
What is the difference between MD5, SHA-1 and SHA-256 Sums?
Control sums are a useful way to make sure that a file has no error. If there is an error due to downloading problems, the checksum will be different.
However, these cryptographic fragmentation functions are not always perfect. Security researchers have discovered "collisions" in MD5 and SHA-1. In other words, they discovered two different files that produce the same MD5 or SHA-1 hash.
This is almost unlikely to happen by accident, but an attacker could use the technique to present a malicious file as normal. This is why you do not have to rely on MD5 or SHA-1 checksums to verify a file.
At the moment there are still no reports of "collisions" with SHA-256, so checksums should be generated in SHA-256 instead of MD5 and SHA-1. SHA-256 is stronger, and more safes algorithm.
How can I check checksums
If you know the checksum of an original file and want to check it on your computer, you can do so easily. All operating systems (Windows, macOS and Linux) have built-in utilitiesletterto generate checksums. So you don't need third-party utilities.
In Windows, the PowerShell Get-FileHash command calculates the control sum of a file. To use it, first open PowerShell. In Windows 10, look for "PowerShell".
In the window that opens, type Get-FileHash, and then tap the tab to add a space.
Type the path of the file you want to calculate the checksum. Otherwise, drag n drop the file from the File Explorer in the PowerShell window and its path will be filled in automatically.
Press Enter to run the command and you will see the SHA-256 hash of the file. Depending on the file size and the speed of your computer, the process may take a few seconds.
If you need another algorithm, you should add it to the end of the command:
Get-FileHash C:\διαδρομή\για\το\αρχείο.iso -Algorithm MD5
Get-FileHash C:\διαδρομή\για\το\αρχείο.iso -Algorithm SHA1
If the checksum matches, the files are the same. If not, there is a problem and maybe your file has been corrupted. If you downloaded it from the web, try downloading it again.
On Linux systems, the control can be performed by the terminal, with the following commands
for the MD5 algorithm the checksum tool is: md5sum
for the SHA-1 checksum tool algorithm is: sha1sum
for the SHA-256 checksum tool algorithm is: sha256sum
So if you want to check a file open a terminal in the folder that contains it and type the corresponding command with the file name.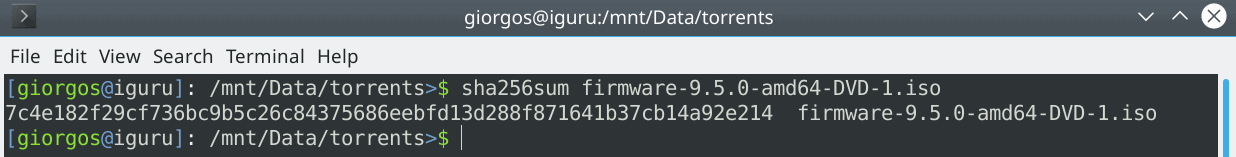
_____________________
- Firefox tweaks for better and faster performance
- Download and print free 92 rulers in real size
- Library with over 1,800 free kids ebooks






Interesting !!!.
And obviously it works in all types of files and not just .iso