The purpose of AORT is to assist bughunters and pentesters in identifying their targets. It is an open source program, written in python, where it is the first move to discover important information about the target one wants to attack.
It is fast enough, easy to use and fully automated even for novice users, giving the best possible results.
Installation
Installation is done with two simple ways. The first way we recommend is through the python repositories by running the following command in your terminal:
pip3 install aort
or alternatively, by running the following commands:
git clone https://github.com/D3Ext/AORT
cd AORT pip3 install -r requirements.txt
Program options
AORT - All in One Recon Tool
options:
-h, --help show this help message and exit
-d DOMAIN, --domain DOMAIN
domain to search its subdomains
-o OUTPUT, --output OUTPUT
file to store the scan output
-t TOKEN, --token TOKEN
api token of hunter.io to discover mail accounts and employees
-p, --portscan perform a fast and stealthy scan of the most common ports
-a, --axfr try a domain zone transfer attack
-m, --mail try to enumerate mail servers
-e, --extra look for extra dns information
-n, --nameservers try to enumerate the name servers
-i, --ip it reports the ip or ips of the domain
-6, --ipv6 enumerate the ipv6 of the domain
-w, --waf discover the WAF of the domain main page
-b, --backups discover common backups files in the web page
-s, --subtakeover check if any of the subdomains are vulnerable to Subdomain Takeover
-r, --repos try to discover valid repositories and s3 servers of the domain (still improving it)
-c, --check check active subdomains and store them into a file
--secrets crawl the web page to find secrets and api keys (e.g. Google Maps API Key)
--enum stealthily enumerate and identify common technologies
--whois perform a whois query to the domain
--wayback find useful information about the domain and his different endpoints using The Wayback Machine and other services
--all perform all the enumeration at once (best choice)
--quiet don't print the banner
--version display the script version
Use
A list of examples for using the tool in different ways
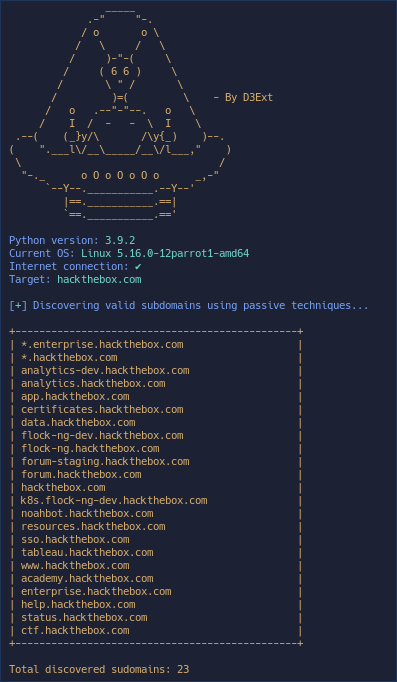
The most basic of these is finding subdomains
python3 AORT.py -d example.com
Find subdomains and save them to a file
python3 AORT.py -d example.com --output domains.txt
Display specific information using different parameters
python3 AORT.py -d example.com -n -p -w -b --whois --enum # You can use other parameters, see help panel
Perform all functions together
python3 AORT.py -d domain.com --all
Specifications
![]() Enumerate subdomains using passive techniques (like subfinder)
Enumerate subdomains using passive techniques (like subfinder)
![]() A lot of extra queries to enumerate the DNS
A lot of extra queries to enumerate the DNS
![]() Domain Zone transfer attack
Domain Zone transfer attack
![]() WAF type detection
WAF type detection
![]() Common enumeration (CMSs, reverse proxies, jquery...)
Common enumeration (CMSs, reverse proxies, jquery...)
![]() Whois target domain
Whois target domain
![]() Subdomain Takeover checker
Subdomain Takeover checker
![]() Scan common open ports
Scan common open ports
![]() Check active subdomains (like httprobe)
Check active subdomains (like httprobe)
![]() Wayback machine support to enumerate endpoints (like waybackurls)
Wayback machine support to enumerate endpoints (like waybackurls)
![]() Email harvesting
Email harvesting
You can download the program from here.





