The ATM is a machine that allows customers to make banking transactions without entering the bank.
Using an ATM, the user can withdraw or deposit cash, access their bank account account, to pay his bills, change his pin, update his personal information, etc.
Since ATM is all about cash, it has become a high priority target for hackers and robbers. In recent years, hackers have found many ways to break into ATMs. Hackers are not limited to physical attacks, such as card trapping, skimming, etc.
They are exploring new ways to hack ATM software. In this article, we will look at security solutions used for ATM security.

ATM security programs
Most of the ATMs run on Windows XP and 7. Repairing individual ATMs is a rather complicated process. Because Windows XP is no longer supported by Microsoft, many ATM vendors use security solutions to mitigate threats associated with ATM attacks, such as malware-based attacks and operating system-level vulnerabilities.
These security solutions allow the application of ATMs to run in a rather restrictive environment, with limited services and procedures.
Two of these security solutions are Mcafee Solidcore and Phoenix Vista ATM.
Mcafee Solidcore:
McAfee Application Control blocks unauthorized executable files in the ATM operating system.
Allows the execution of only those applications, processes and services that are included in the list of allowed operations. Monitors modifications (changes) to code of the program and configurations through the Integrity Monitor.
Protects the application code and configuration from unauthorized changes with its change control mechanism. The ATM application and related files are first entered in the list of allowed and then executed.
Phoenix Vista ATM:
Phoenix Vista ATM is a product of Phoenix Interactive Design Inc. acquired by Diebold.
It is integrated in the application that ATMs have. It works by checking the integrity of the files where any modification / violation of the critical file related to the application, will result in the shutdown of the system.
This does not allow any unauthorized program to modify the specific file of the application.
The architecture consists of 3 levels. OS XFS Vista ATM.
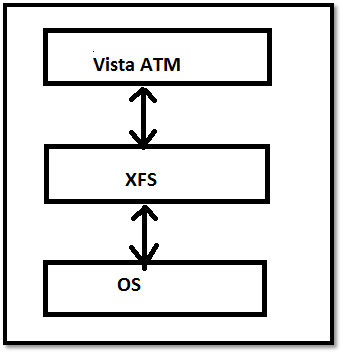
XFS (EXtensions for Financial Services) provides a client-server architecture for cost-effective applications on the Microsoft Windows platform, especially on peripherals such as ATMs that are unique to the financial industry.
It is an international standard promoted by the European Committee for Standardization (known as CEN, hence CEN / XFS). XFS provides a common API for accessing and operating different financial services devices, regardless of the manufacturer.
Vista ATM communicates with the XFS level which instructs the program, such as the ATM cash distributor, to distribute the cash. Any unauthorized modification to XFS files will activate the Vista ATM application to force restart the machine. The machine restarts 4-5 times and then enters maintenance mode which does not allow the user to make any transaction.
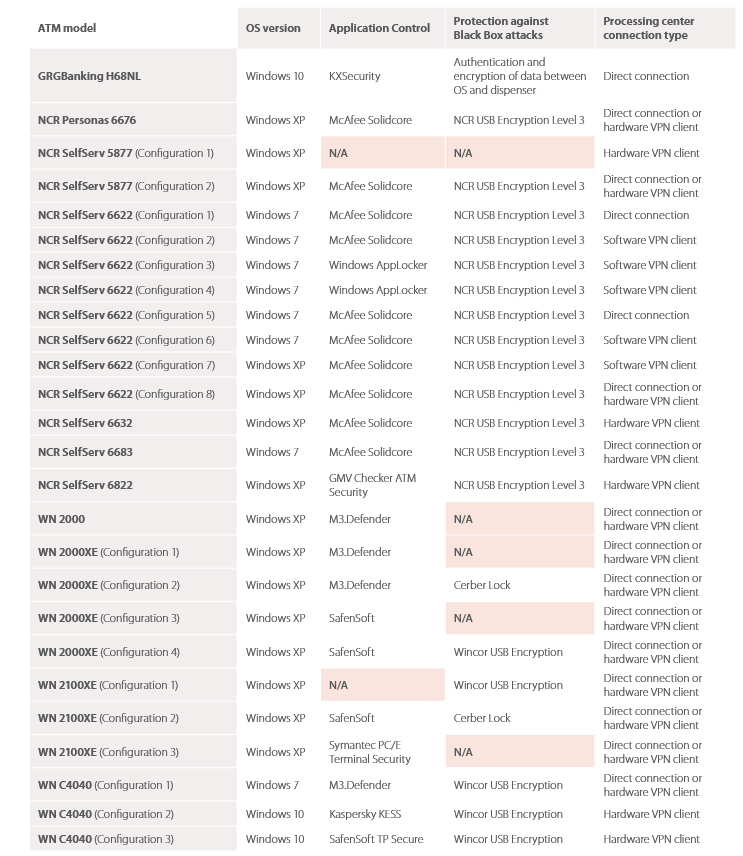
Below we will see a list of 26 ATMs, the software they use, as well as their security level.
Penetration Testing Procedure at ATMs
The approach to testing the security of ATMs remains the same. The ultimate goal is to access the operating system or deal with the application-related file to see how the application itself behaves.
An attacker, after gaining access to the operating system, can create malware that can command the system program using XFS components.
Some of the test cases that can be considered are:
- Tests related to access to the operating system and related system file
- Check if USB functionality is enabled, boot USB using ” Konboot ".
- Connect the USB and boot the system via USB.
- Since most of the test has to do with the operating system, keep pressing the "Shift" button at startup. This will break any sequence that is set to run at boot time in the ATM operating system. This will result in you going directly to Windows.
- If you know a valid username, enter it and press the "Enter" button. This will result in instant access to the operating system without a password.
- If you do not know a valid username, try logging in to "Administrator", as many ATMs do not deactivate the default administrator account.
- Another way is to bootable USB using Hiren boot . Boot from USB, where this will give access to the file system directly offline in Windows.
Test related to program authorization: Check if USB is enabled, try running an unauthorized program (exe file) directly from USB or using the USB auto-play feature.
Test related to program protection: Check if application-related files can be moved to another location, modified, or deleted.
Checks related to the modification of the whole process: Rename the unauthorized file with a valid and acceptable name. This will cause an unauthorized file to run when the application starts.
As the number of ATMs increases, the machine is prone to hacking attacks, robberies, scams, etc. Most ATMs still use Windows XP, which makes these ATMs an easy target for hackers. Electronic money transfer includes three components which are the communication connection, the computer and the terminal (ATM). All three components must be secured to prevent an attack. We will look at the type of assessment we can perform to analyze the overall security of an ATM.
1. Vulnerability assessment and penetration testing of the network
These two activities are common when dealing with ATM security.
At pentest we check for network level vulnerabilities in an ATM. If the ATM communicates with the support server, it must be part of a network.
Taking the address IP of the ATM, we can run a pentest within the network. As a security best practice, the ATM network is separated from the bank's shared network.
Therefore, the hacker must be on the same network as the ATM to find out the IP of the ATM and carry out attacks.
Once we enter the network where the ATM is located, we can perform a scan with it Nessus to identify its open doors, the services performed on them, as well as the vulnerabilities associated with its performed services. We can perform a full scan with NMAP to identify TCP and UDP ports and ATM services.
Configuration control is concerned with operating system security. Most ATMs run the Windows operating system. The operating system must have no security vulnerabilities, to reduce the attacker's attack range and not have many options. Some of the areas that we can consider when performing the ATM operating system configuration check are:
- Fixes and updates: Checks related to the latest operating system and security updates.
- File system security: Controls related to access to critical folders and important system files.
- System access and authentication: Checks related to password and account lock policy, user rights policy, etc.
- Checking and recording: Controls related to the operation of the ATM, application and security logs, control policy, license in the event logs, etc.
- Account Configuration: Controls related to users by admin group, presence of default users, guest account, password requirement and expiration.
2. Application security check:
We can divide this activity into two categories:
a). Thick client application penetration testing: Some of the test cases we can perform are:
- Sensitive information in application configuration files, registry credentials, sensitive code-encoded information
- Check the traffic going to the server and try to manipulate / violate the parameters or look for any sensitive information that passes between the application and the server
- Check if the application and the database communicate in plain text protocol (non-encrypted files)
- Reverse Engineering protection
b). Application Design Review: In this process, we can check for security practices followed in the application itself. Some of the test cases may be:
- Types of events recorded in the log
- The rights with which the ATM application is executed
- Access the folders related to the application
- The application allows the transaction without a pin or with an old pin
- The application allows access to the operating system during execution
- Communication with back-end hardware
- Effective network isolation
- Disconnect the customer card in case of even one invalid pin test
- It is mandatory to use a PIN for each transaction
- The software should not display the pin during the process of inserting it on the screen
Security practices to be followed by banks
Banks can implement some security practices to reduce the range of attack for the attacker. Below we will see some parameters that should be given great attention:
Protection against physical attacks:
- Detection and protection against skimming of the card.
- Detection and protection against card and cash entrapment.
- Detection against keyboard violation.
- DVSS camera application built into the ATM to record the user's facial features along with transaction details and timestamp.
- Protection of the treasury from fire, explosion, etc.
- Lock protection and again unauthorized access to banknotes or accounts.
- Protection of electricity and grid points.
- Deactivation of unused network as well as electric port.
- The ATM must be grouted on the floor to insure against robbery-related threats. The ATM can be mounted with a vibration sensor to detect the impact and movement of the ATM machine.
- CCTV camera installation. Presence of a guard.
Protection against hacking attacks:
- Protection against unauthorized booting without using a password and entering the BIOS. Most ATMs have a default boot password.
- USB protection and unauthorized access to the hard disk.
- Secure OS and fully updated on a daily basis.
- Allowed list of applications, services at the ATM.
- Operation with fewer user privileges.
- File integrity checks.
- Securing transaction logs.
- Use secure connection for communication and transaction.
- Formulation of best security practices in the application of ATMs.
- Virus protection.
- Separation of ATM network with other networks.
- Malware protection such as tyupkin, ploutus etc.
Protection against fraud-based attacks:
- Geo-blocking application. In this application, the card can only be used in the country or region of origin of the card. The user must obtain a license to use the card outside its country of origin.
- Pin-based chip-based card application for mitigating attack based on duplicate cards and skimming cards.
- An application that will detect an unusual transaction in terms of amount, place of transaction, frequency of transaction, etc.
Conclusion
With her progress technologys, hackers are finding more and more ways to breach ATMs.
In the fight to maintain the security of ATMs and maintain the trust of customers, banks must stay one step ahead of criminals, developing the latest security solutions and reducing the range of attack as much as possible.
The solutions given in this article will help you make the ATM safer, enhancing both physical and logical security.




good job