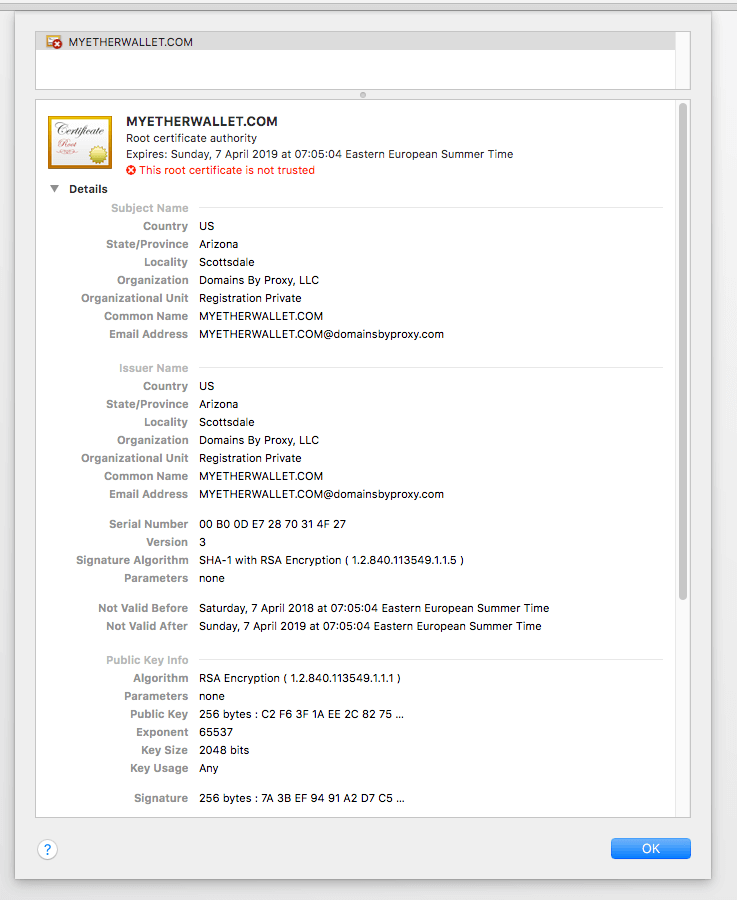
BGP hijacking: Last night, MyEtherWallet users started noticing something strange. Upon connecting to the service, an unsigned SSL certificate and of course a warning were displayed.
It was unusual, but it was the kind of problem that usually some react without thinking.
But anyone who clicked on that certificate warning was redirected to a server at Russia, who emptied the user's digital wallet. Judging by the trading activity, the attackers seem to have already acquired more than 17 millions dollars to Ethereum.
MyEtherWallet confirmed the attack on a statement at Reddit.
"We are currently in the process of verifying the servers to resolve this issue as soon as possible," the company told users. “We advise users to run a local (offline) copy of MyEtherWallet. ”
The attackers did not appear to have violated MyEtherWallet itself, but used an Internet infrastructure blocking myetherwallet.com's DNS requests. So they made the Russian server look like the legitimate owner of the address.
To hinder these requests, hackers used a technique known as BGP hijacking. This technique spreads misleading routing information to trap movement during transport. Typically, the use of such a hijacker requires invasion of BGP servers operated by an ISP (Internet Infrastructure Provider). In this case, hijacking happened to an ISP from Chicago, although the root of the evil is still unknown.
So far, MyEtherWallet is the only confirmed service to have this kind of attack.
Let's say that BGP hijacking has long been known as a fundamental weakness on the internet. History is a great example of what can happen when we operate automated, or impulsively without thinking.
See the certificate used: