The program Your browser may store sensitive data, including usernames, passwords and session cookies operation, to clear text in memory. Check how yours behaves.
According to CyberArk security researcher Zeev Ben Porat, most Chromium-based web browsers, including the famous Chrome, seem to be affected by this inability to program.
But he's not the only one. Both Microsoft Edge and Brave are susceptible, and even its Firefox web browser Mozilla are also affected by the problem.
Which is the subject; That your browser caches all your sensitive data in plain text and not encrypted. Viewing stored passwords and names does not require physical presence on the target machine, nor administrator privileges, as remote access or even the execution of malware software on the target machine is sufficient to extract the data.
Η better safety two-factor authentication may not even be sufficient to protect user accounts if cookie data is in memory.
Security researcher Zeev Ben Porat describes many different types of credential data in text form that can be extracted from the browser's memory. Such as:
- Username + password used when logging in to a targeted web application
- URL + Username + Password are automatically loaded into memory when the browser is started by password management
- All URL + username + password entries stored in login data
- All cookies that belong to a specific web application (including session cookies)
The problem was reported to Google and the response was "it will not be fixed". The reason given is that Chromium will not fix issues related to physical local access attacks.
Try your own browser

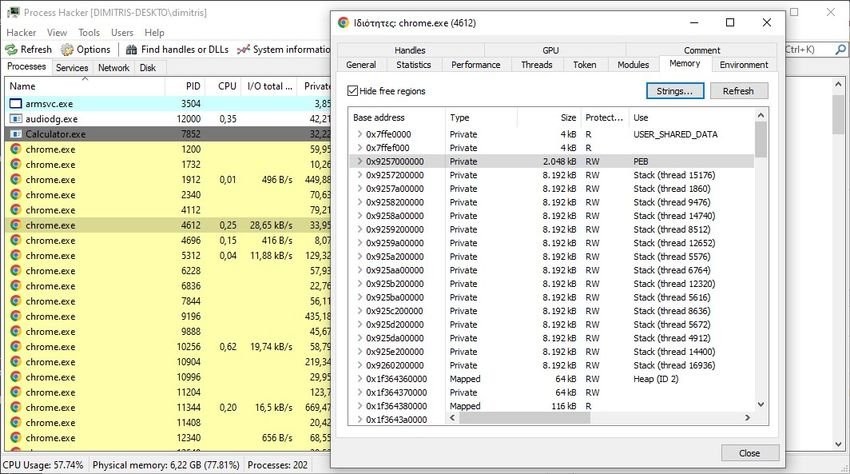
Windows users can use free Process Hacker tool to test their browsers.
Simply download the portable version of the program, extract its zip file and run the file Processhacker.exe to get started. Then do the following test:
Step 1: Enter a username, password, or other sensitive data on a random page in the browser you want to try.
Step 2: Double-click the main browser process in the Process list Chippers, to display details.
Step 3: Go to the Memory tab.
Step 4: Activate the Strings button on the page.
Step 5: Click OK on the page.
Step 6: Activate the Filter button in the window that opens and select "Contains" from the context menu.
Step 7: Enter the password of step 1 or other sensitive information in the "Enter the filter pattern" field and select ok.
Process Hacker will return your data if it is found in process memory.





