Cybercriminals have an unbridled thirst for credit card details. There are many ways to intercept information online, but Point of Sale (POS) is the most attractive goal.
An estimated 60% of Retail Point of Sale (POS) are made using a credit or debit card. Considering that large retail chains can process thousands of transactions daily, it makes sense that their terminals would become a target for cybercriminals looking for large amounts of credit card data. cards. You will find detailed information and details on how attacks are carried out at Points of Sale and how you can protect yourself in the whitepaper Attacks on Point of Sale Systems.
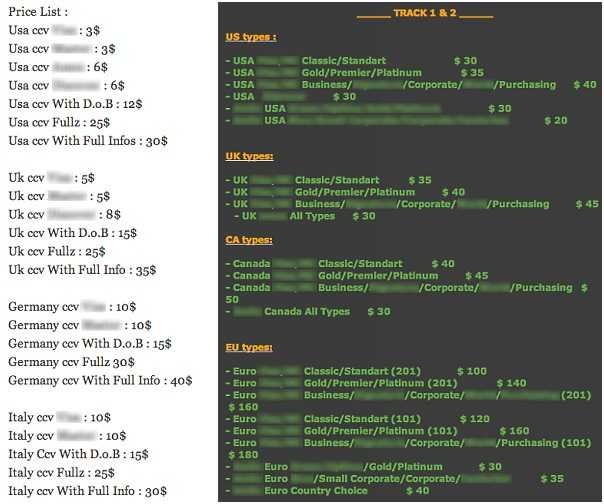
There are currently a number of online forums selling credit and debit card data in various formats. The most common is "CVV2" where the vendor provides the card number, along with the additional CVV2 security code, which is located on the back of the card. This data is enough to facilitate online purchases. However, some sellers offer the most lucrative "Track 2" data. It's the abbreviation of the data stored on the magnetic chip on the card. This data is more profitable as it allows criminals to clone cards for use in physical stores or on ATMs if the PIN is available. The value of the data is reflected in the online selling price and the prices vary widely. CVV2 data is sold for the amount of $ 0.1 to $ 5 per card, while Track 2 data may cost up to $ 100 per card.
So how do criminals obtain this data? Skimming is one of the most popular methods. This includes installation additional hardware in the POS terminal, which is then used to read the track 2 data from the cards. But as it requires physical access to point-of-sale systems and expensive equipment, it is difficult for criminals to implement on a large scale. To address this particular problem, attackers have turned to software solutions in the form of POS malware. By targeting major retailers with this malware, criminals can extort millions of card data with a single campaign.
The POS malware exploits the security gap and the way companies manage credit card data. While credit card data is encrypted as it is sent for a debit authorization, it is not encrypted when the payment is processed, e.g. at the moment the card is passed to the terminal for the payment of the goods. Fraudsters took advantage of 2005 for the first time when the campaign launched by Albert Gonzalez led to 170 million data theft.
Since then an entire market has been created related to the supply and sale of malware that reads Track 2 data from the POS terminal memory. Most POS systems have a Windows operating system, making them relatively easy to add malware to. This malware is known as memory-scraping malware, where it searches memory for data matching the Track 2 data pattern. Once it finds this data in memory, which is done at the time the card is used, it saves it to a folder on the terminal, which the attacker can then retrieve. The most well-known of the POS malware is BlackPO, which is sold on cybercrime forums. THE Symantec identifies this malware by name Infostealer.Reedum.B.
Armed with POS malware, the next challenge for attackers is to integrate it into POS terminals. POS terminals are not usually connected to the internet but have some connectivity to the corporate network. The attackers will try to penetrate the corporate network first. This can be done by exploiting vulnerabilities in external systems, such as SQL penetration on a Web server, or finding a peripheral device that still uses the manufacturer's default password. Once on the network, they will use a number of hacking tools to gain access to parts of the network that host POS systems. After installing POS malware, attackers will take the necessary steps to ensure that their activity goes unnoticed. These measures include canceling log files or compromising security software, which ensure that the attack will persist and collect as much data as possible.
Δυστυχώς, η κλοπή δεδομένων καρτών αυτής της φύσης είναι πιθανόν να εξακολουθεί να γίνεται στο επόμενο διάστημα. Η κλοπή δεδομένων καρτών έχει περιορισμένη duration ζωής καθώς οι εταιρείες που διαθέτουν πιστωτικές κάρτες αντιδρούν άμεσα στον εντοπισμό ανωμαλιών στα πρότυπα δαπανών, αφού υπάρχουν συστήματα παρατήρησης των κατόχων καρτών. Αυτό συνεπάγεται ότι οι εγκληματίες χρειάζεται να προμηθεύονται συνεχώς ‘φρέσκα' δεδομένα πιστωτικών καρτών.
Τα καλά νέα είναι ότι οι επιχειρηματίες λιανικής πώλησης θα πάρουν μαθήματα από αυτές τις επιθέσεις και να λάβουν τα απαραίτητα μέτρα που θα εμποδίσουν την επανεμφάνιση αυτού του τύπου της επίθεσης. Η τεχνολογία πληρωμών θα αλλάξει επίσης. Πολλοί επιχειρηματίες λιανικής πώλησης στις ΗΠΑ έχουν προχωρήσει στις συναλλαγές μέσω EMV, ή στις τεχνολογίες πληρωμής “chip and pin”. Οι κάρτες Chip and Pin είναι πολύ πιο δύσκολο να κλωνοποιηθούν, γεγονός που τις κάνει λιγότερο ελκυστικές στους επιτιθέμενους. Και φυσικά τα νέα models πληρωμής θα κερδίσουν μεγαλύτερο μερίδιο αγοράς. Τα smartphones θα γίνουν οι νέες πιστωτικές κάρτες, καθώς οι φορητές τεχνολογίες πληρωμής ή η τεχνολογία NFC θα γίνουν ευρέως αποδεκτές.
There is no doubt that cyber criminals will find a way out of these changes. But as retailers adopt newer technologies, security service companies continue to watch the attackers, so that large-scale theft will become even more difficult and certainly less profitable.







