With the help of honeypot, you can easily monitor your operating system and monitor any hacker activity or you can say that it is the best way to hack the hacker himself.
Every large company already uses smart honeypots in its backend such as Google, Facebook and Microsoft.
In fact they want to track all the activities of all the users and if they find illegal or malicious activity then honeypot has the ability to immediately block the dangerous IP address.
Types of Honeypots
Honeypots can be categorized in two ways, based on development and design criteria.
a) Basis of development
- Production Honeypot
- Research Honeypot
b) Basis of design criteria
- Pure Honeypot
- High-Interaction Honeypot
- Low-Interaction Honeypot
How to set up a honeypot on Kali Linux
As you all know Kali Linux is one of the most popular pentesting mods having more than 600+ built-in tools hacking/ attacking preinstalled.
To install honeypot on a computer running Kali Linux, you need to download and install Pentbox, the which you can easily find through it Github repository.
Mandate: git clone https://github.com/whitehatpanda/pentbox-1.8.git
Μετά τη λήψη, μπορείτε απλά να εκτελέσετε το pentbox πληκτρολογώντας " ./pentbox.rb " μέσα στο φάκελο pentbox-1.8.
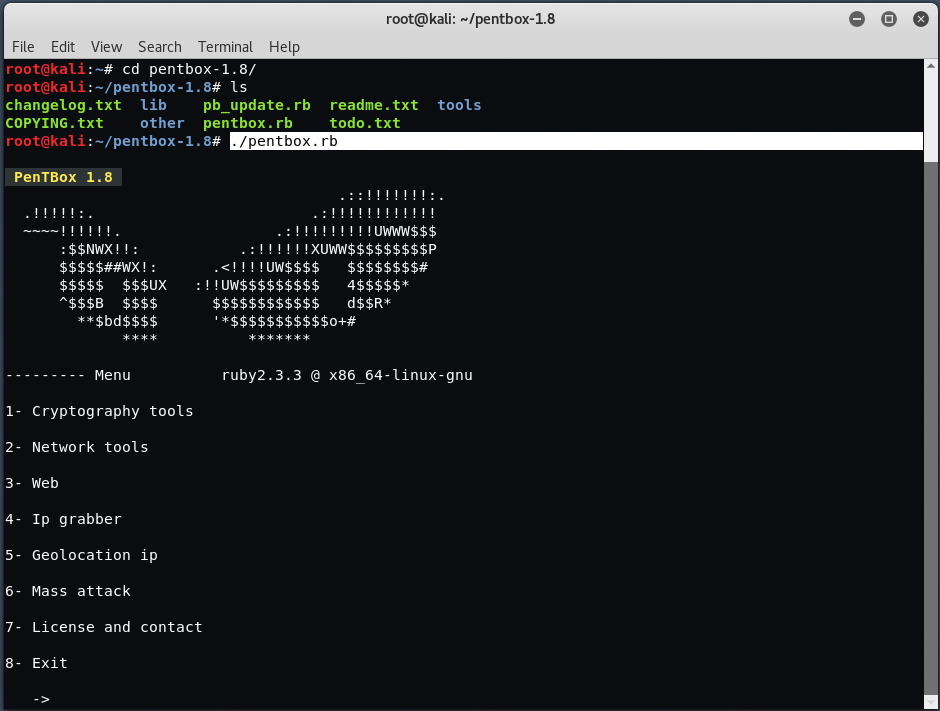
As you can see, it will display 7-8 options, which you can easily perform as follows:
- Cryptography tools
- Network tools
- Website
- IP Grabber
- IP geographical location
- Mass attack
Για να χρησιμοποιήσετε τα Εργαλεία Κρυπτογραφίας, απλώς πληκτρολογήστε " 1 " και θα εμφανίσει άλλες 4 επιλογές όπως " Base64 Encoder / Decoder "," Multi-Digest "," Hash Password cracker " and " Secure Password Generator ".
You can use any of the options according to your needs.
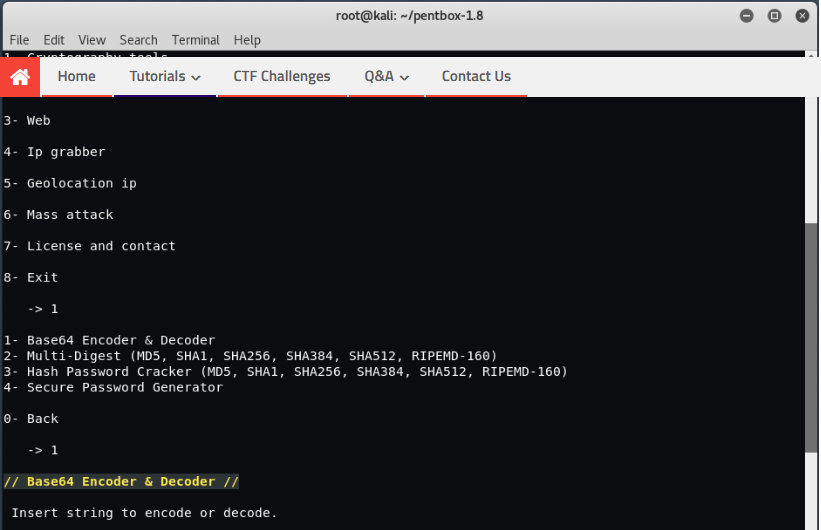
Τώρα έχουμε Εργαλεία Δικτύου στην επιλογή αρ. 2 μέσω των οποίων μπορείτε να εκτελέσετε " Net Dos Test "," TCP port scanner "," Honeypot "," Fuzzer "," DNS and Host gathering" and " Mac address geolocation ".
Για να χρησιμοποιήσετε το honeypot, απλώς πληκτρολογήστε " 3 " on your terminal.
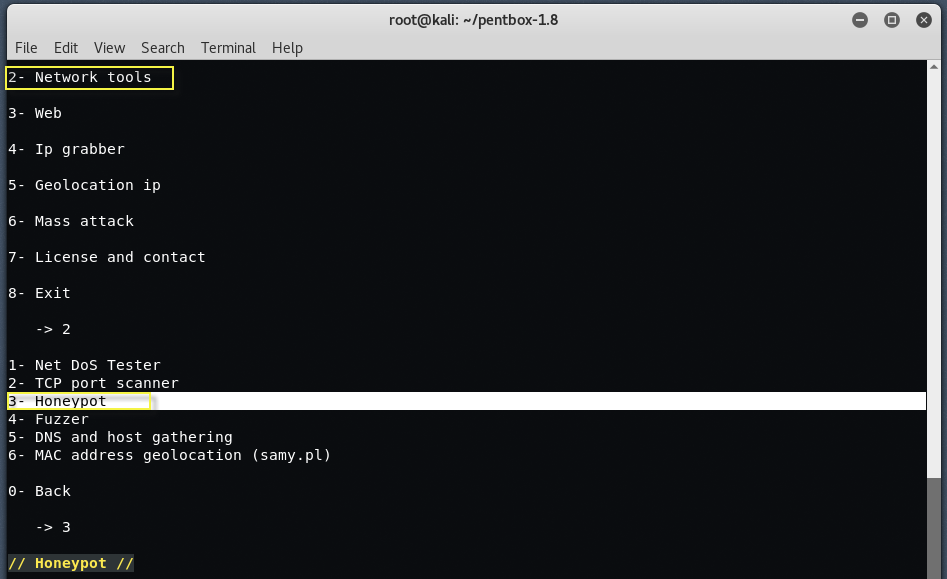
Now you can see that there are two options through which you can configure your honeypot.
- a) Fast automatic configuration
- b) Manual configuration (for advanced users)
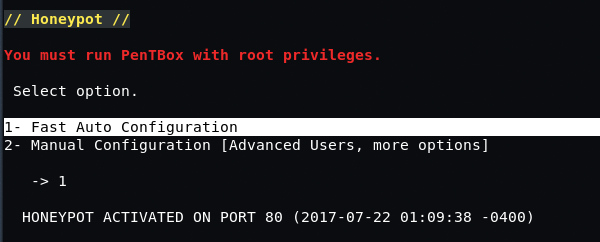
You can set any of the options, but for novice users, it is recommended to choose Quick Auto-Configuration. As you can see, the honeypot starts at the above snapshot screens.
Your honeypot will only monitor all activity on the PORT 80, but if you want to monitor some activity on another port, you can select the second Manual configuration option.
Port 80 means, when someone opens your IP / Host in their browser, then they will immediately record this request and display all possible information of this request as shown below:
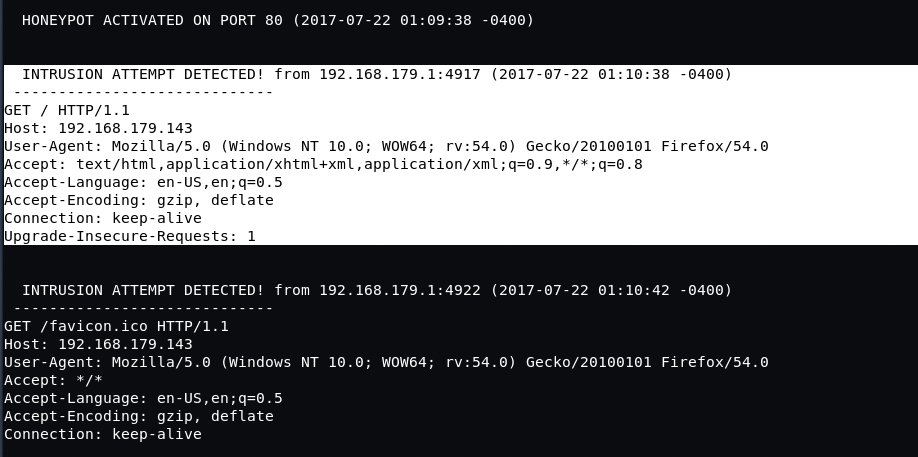
The information you can see:
- IP address
- Details of its operating system
- browser
- various other information
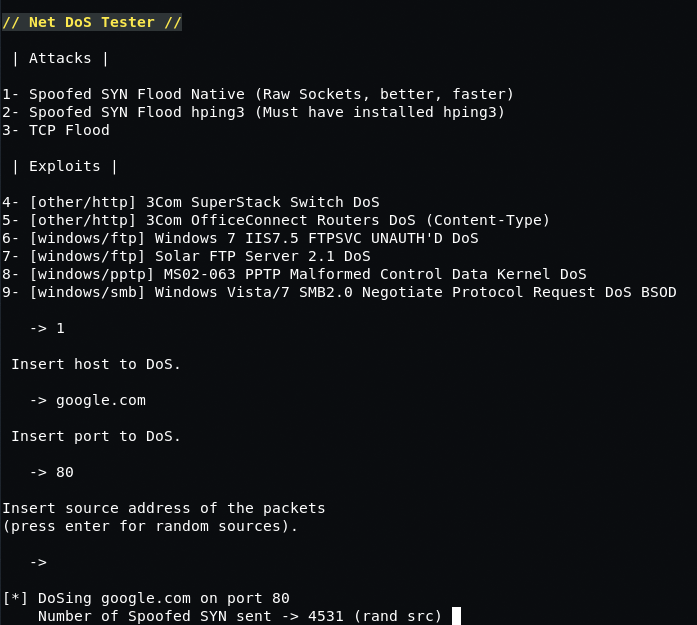
Κάτω από τα ίδια εργαλεία δικτύου, υπάρχουν επίσης μερικές ενδιαφέρουσες επιλογές όπως " Net Dos Tester " μέσω των οποίων μπορείτε εύκολα να κάνετε DOS κάποιον με SYN και TCP flood επιθέσεις.