Two-factor authentication is a key security tool for online accounts. See how it works and how to start using it.

Two-factor authentication is a vital method of protecting your online accounts. It is available almost everywhere and offers drastically increased security, compared to locking your account with just one password.
Let's look at what two-factor authentication is, how it protects your accounts, and how you can get started.
| What is two-factor authentication? |
Two-factor authentication (often referred to by the English abbreviation 2FA), is a connection method that requires you to present two sections to sign in to an account. This is in contrast to one-factor authentication, where you only need to enter a password to access your account.
In general, there are three types of "agents" that can be used for authentication. They are:
- Something you know: Any information you know and no one else knows (hopefully), such as a password.
- Something you have: Your possession, such as a telephone or security key.
- Something you are: A part of it body that uniquely identifies you, such as a fingerprint, or your face.
Some people use the terms "two-factor authentication" and "two-step authentication", but they are not the same.
Two-factor authentication requires agents from different categories, such as the above. Like a password and a password from your phone. Two-step authentication uses two verification methods from the same category, such as a password and a security query.
Actual two-factor authentication is more powerful because it does not require two pieces of data that have the same vulnerabilities.
| Why do you need two-factor authentication? |
In today's world of passwords, passwords alone are often not enough to protect your accounts. There are two reasons for this.
Part of the problem is that most people are lazy with passwords. Making common password mistakes, such as using it same password everywhere or the use of passwords with little complexity, facilitate the breach of your accounts.

Short passwords made up of dictionary words or common patterns are easy to crack on machines with enough computing power. And if you use a password on multiple sites, an attacker who finds a password could lead to multiple accounts.
You can resolve these issues using a password manager to create strong, unique passwords for each site. But this method is not infallible.
Even if you have a very strong password, a malicious person can break it if you fall victim to cyber fishing or some similar digital password theft technique.

Your password could also be exposed, without your own fault, by a site security breach. In these cases, it does not matter how strong your password is when it is in someone else's hands.
The consequences of someone stealing your accounts
In either case, someone could use your broken password to log in to your account and do whatever they want. Depending on the account, this can result in someone stealing your bank account information, learning personal information about your family, being able to pose like you on social media, etc.
Because many of our online accounts are online, a thief who has access to even one can cause a lot of problems. This is especially true for email accounts, as attackers can send password reset emails to other accounts to your inbox.
| How does two-factor authentication work? |
In practice, two-factor authentication adds an extra step to the process of linking to websites and services. After entering your username and password correctly, you will see a prompt to enter a password (or otherwise confirm the second authentication agent). If you do not enter the second factor (password) correctly, you will not be able to log in.

To make the process a little smoother, most services allow you to select a box labeled "Do not require passwords in this browser" or something similar. This bypasses 2FA for future visits, while still demanding it elsewhere. This is convenient for the devices you use all the time, as long as you keep them safe, of course, and always be behind their keyboard.
When using two-factor authentication, there are some important points to know before you get started.
Account recovery when using two-factor authentication
You must have an account recovery plan when using 2FA. On almost any website, it is easy to reset your password, if you forget it, with a simple link to an email. However, if you lose access to the 2FA method, you will have more problems.
For security reasons, sites can't just let you disable 2FA if you lose access to the generator code (or whatever method you use). As a result, you may be locked out of your account if you are unable to log in using any 2FA method.

To address this possibility, when you set up two-factor authentication on most sites, you'll be given a list of backup recovery codes. You can enter them in place of regular 2FA codes to successfully log in. It is vital that you have access to these codes in case something unexpected happens. Keep them somewhere safe, like in a password manager or a archive on your computer.
If you lose these codes and have no other way to log in, you should turn to any advanced account recovery method offered by service. This usually takes several days to complete and may require more extensive steps to prove that you are the rightful owner of the account.
Use password for unsupported services
While two-factor authentication is now possible on many services, it is not compatible with some older devices. For example, if you have two-factor authentication on your Microsoft account and try to sign in to Xbox 360, it will not work properly.
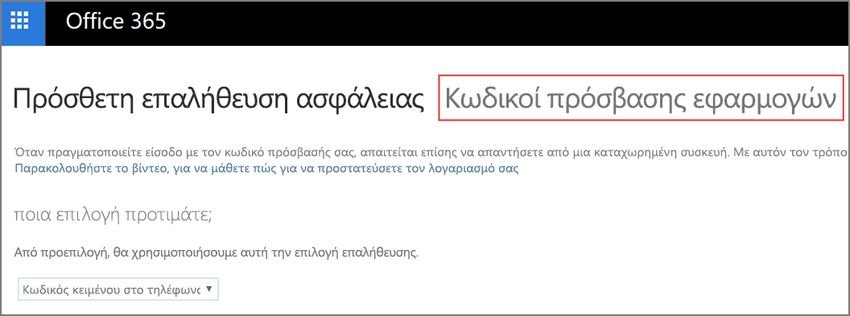
To overcome this limitation, the services allow you to set application codes when using 2FA. The application codes (App Passwords) are created as a one-off and used instead of your usual account password. If you have problems connecting on a device using a 2FA-protected account, check your account settings for an application password or application password option to resolve it.
| Two-factor authentication methods |
Two-factor authentication is available in many forms. Some sites offer only one option, while others give you many options. We will summarize the most common here. See the advantages and disadvantages of different two-factor methods for more information.
Passwords by SMS or email
With this method, you will receive an SMS text message or an email containing a one-time code that you need to log in. While this process is convenient and simple, it is also sensitive in monitoring. Additionally, if you do not have cell service or a reliable Internet connection, you cannot receive these codes.
These authentication methods are better than nothing, but we suggest you use another method when available.
This method is usually used by banks in Greece, in their online transactions, where in order to complete a transaction, in addition to the fact that you have to log in to their website, they also send you a unique code on your mobile phone to pass it.
Authentication applications
Authentication apps are the best balance between security and comfort. These applications generate short codes that change on a regular basis. You just need to copy the password from the authentication application to connect to 2FA.
When you enable this method, the sites will guide you on how to add them to the authentication application. Usually, all you need to do is scan a QR code to start generating codes, and then enter one to make sure everything is working properly. These codes work without an Internet connection, which is an additional improvement over SMS codes.
The authy is one of the best 2FA authentication applications. It is available on all platforms, offers encrypted backups and is easy to use.
Another good application is Google Verifier. Works for both your Google Account and other services. You can also install it on Android and on iPhone.
Physical security keys
For maximum security, you can turn a USB drive into a security key or use a tool such as YubiKey. This 2FA method requires you to insert a device into your computer (or scan it with your phone) and press an authentication button.

While these cost money, security keys are a powerful option, as intruders cannot steal a physical device as easily as they can have a password or security code sent via email. However, they are quite inconvenient compared to authentication applications and can become a huge problem if you lose them.
| Where should you use two-factor authentication? |
Now that you understand two-factor authentication, it's time to turn it on in your accounts. For best results, you should use it everywhere when you have the choice. Combined with a strong password created by a password manager, it becomes very unlikely that someone will hack your accounts.
For more, take a look at Two-Factor Auth . This is an easy-to-use resource that lets you search any service or site and see if it offers 2FA. And if so, what methods does it support? You can search or browse by category.
| Two-factor authentication will protect you |
We've seen how two-factor authentication is a relatively painless way to keep your accounts protected. It only takes a little time to set it up and your accounts will have multiple levels of protection.





