A developing attack involving the dropbox goes around the world. We have already seen within the first two weeks of September, 5.550 such attacks.
Hackers use it dropbox to create fake login pages that eventually lead to a credential collection page.
This is yet another example of how hackers use legitimate services in what we call attacks BEC 3.0. The attacks Business Email Compromise 3.0 refer to the use of legitimate websites - such as dropbox- για την αποστολή και φιλοξενία υλικού Phishing. The legitimacy of these sites makes it almost impossible for email security services to stop them and for end users to detect them.
These attacks are on the rise and hackers are increasingly using hotspots such as Google, dropbox, QuickBooks, PayPal and other. This is one of the smartest innovations we've seen, and given the scale of this attack so far, it's one of the most popular and effective.
In this brief update on the attack, her email investigators Check Point Harmony analyze how hackers use social engineering with a dropbox server, with the aim of gaining the user's attention and extracting their credentials.
The attack
In this attack, hackers use documents of dropbox to host websites that collect credentials.
- Carrier: email
- Type: BEC 3.0
- Techniques: Social Engineering, Credential Gathering
- Target: Any end user
Example Email
This attack starts with one Email which comes directly from dropbox.
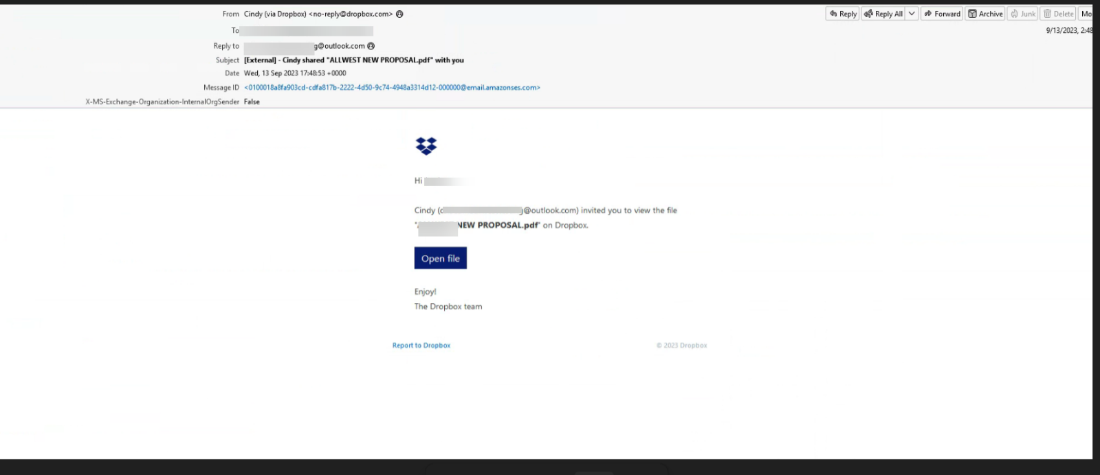
This is a standard email that everyone receives from dropbox, which informs him that there is a document to view.
From there, the user is taken to a legitimate page dropbox:

Although the content is that of a page that looks like the OneDrive, the address URL hosted at dropbox.
Όταν κάνετε κλικ στο "Get Document", ο χρήστης οδηγείται σε αυτή την τελική σελίδα. This is the credential collection page.
Technical
Η infringement of business e-mail has undergone a fairly rapid evolution.
Ήταν μόλις πριν από λίγα χρόνια που γράφαμε για τις λεγόμενες απάτες με "κάρτες δώρων". Αυτά ήταν μηνύματα ηλεκτρονικού ταχυδρομείου που προσποιούνταν ότι προέρχονταν από έναν διευθύνοντα σύμβουλο ή ένα στέλεχος, ζητώντας από έναν υφιστάμενο να αγοράσει "δωροκάρτες". Η ιδέα ήταν ότι οι χάκερς θα χρησιμοποιούσαν στη συνέχεια τις δωροκάρτες για προσωπικό όφελος. Αυτά τα μηνύματα ηλεκτρονικού ταχυδρομείου προέρχονταν συνήθως από πλαστογραφημένη διεύθυνση gmail - As the CEO@gmail.com instead of CEO@company.com.
The next development came from hacked accounts. This could be an exposed internal user, such as someone in finance, or even an exposed partner user. These attacks are even more difficult because they originate from a legitimate address. But you may see a link to a fake login page on O365 or a misspelled one language that can detect it NLP.
But now we have it BEC 3.0, which is attacks from legitimate services. The NLP είναι άχρηστο εδώ - η γλώσσα προέρχεται απευθείας από νόμιμες υπηρεσίες και τίποτα δε δείχνει λάθος. Η σάρωση URL is also not going to work since it will direct the user to a legitimate site dropbox or other location.
These attacks are incredibly difficult to stop and detect, both for security services and end users.
Education is vital. End users need to ask themselves: Do I know this person who is sending me a document? And even if you click on the document, the next thing to ask: does a page make sense OneDrive in a document dropbox;
Asking these questions can help. As well as hovering over the address URL on his own page dropbox.
But this requires a lot from the user.
This is why these attacks are increasing in frequency and intensity.
Her researchers Check Point they contacted her dropbox to inform her about this campaign on September 18.
Best practices: Guidance and recommendations
To protect against these attacks, security professionals can do the following:
- Adopt technology with artificial intelligence, capable of analyzing and identifying numerous indicators Phishing to proactively prevent complex attacks.
- Adopt a comprehensive security solution that includes document and file scanning capabilities
- Develop a strong protection system URL which performs thorough scans and simulates websites for enhanced security





