The security company ESET posted on blog new features and features for the Win32 / Sality DNS changer.
The Win32 / Sality is a family of malware used by a peer-to-peer botnet, since at least 2003. This is a file infector and one trojan downloader, primarily used to send spam, although it has been used for various purposes, such as imitation of ad network traffic, distributed denial of service attacks or cracking in VoIP accounts. All commands and files exchanged via the Sality P2P network are digitally signed. Its architecture, as well as the longevity of the botnet, show that it has been designed and programmed flawlessly.
Η ESET has been monitoring the Win32 / Sality network for some time and has recorded more than 115000 IP addresses that use the so-called "super peers" to keep the botnet alive. The botnet thus transmits their commands to regular peers aka peers.
The security company has been monitoring and recording network behavior for quite some time now. Recently, researchers discovered some new features of it: it acquired the ability to change the primary DNS address of routers, which is very different from a normal theft κωδικού πρόσβασης FTP ή την λειτουργία ενός spambot που γνωρίζαμε από το Win32/Sality. Σύμφωνα με τα στοιχεία της telemetryς της ESET, το νέο χαρακτηριστικό εμφανίστηκε για πρώτη φορά στο τέλος του Οκτωβρίου 2013. Τότε αναφέρθηκε για πρώτη φορά από την Dr. Web, η οποία δημοσίευσε μια technique analysis of a feature, the IP address scanner. They called it Win32/RBrute.
The new goal: changing the primary DNS of a router
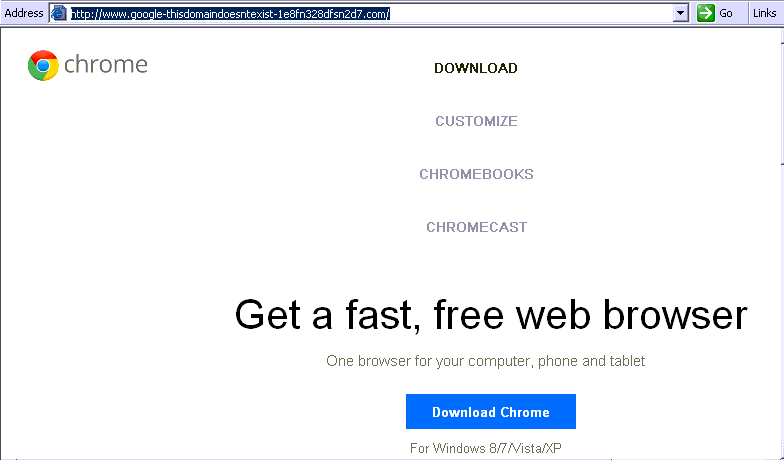
This feature adds a new dimension to Win32 / Sality mode. The first component, detected by ESET as Win32 / RBrute.A, scans the Internet for router management pages to change the entry of the master DNS server. The DNS servers that the malware adds redirect users to a fake Google Chrome installation page each time they try to open pages that the url contains the words "google" or "facebook". The binary distributed through this installation page is actually Win32 / Sality, thus providing a way for Sality botnet owners to further increase the number of their victims with infected routers.
The IP address used as the primary DNS on the victim's router is part of the Win32 / Sality network. In fact, Win32 / Sality installs another malware, detected by ESET as Win32 / RBrute.B. Win32 / RBrute.B runs a DNS or HTTP proxy to deliver the fake Google Chrome installation program.
the company
ESET has published a list of routers that are vulnerable to Win32 / RBrute.A malware:
- Cisco routers matching "level_15_" in the HTTP realm attribute
- D-Link DSL-2520U
- D-Link DSL-2542B
- D-Link DSL-2600U
- Huawei EchoLife
- TP-LINK
- TP-Link TD-8816
- TP-Link TD-8817
- TP-Link TD-8817 2.0
- TP-Link TD-8840T
- TP-Link TD-8840T 2.0
- TP-Link TD-W8101G
- TP-Link TD-W8151N
- TP-Link TD-W8901G
- TP-Link TD-W8901G 3.0
- TP-Link TD-W8901GB
- TP-Link TD-W8951ND
- TP-Link TD-W8961ND
- TP-Link TD-W8961ND
- ZTE ZXDSL 831CII
- ZTE ZXV10 W300
When the malware discovers the router's management website, the centre command and control (C&C) sends a short list of about ten passwords to the bot and instructs it to perform a brute force attack to discover the router's password. When the bot succeeds in connecting, it immediately changes the settings of the router's primary DNS server. Once it does, all DNS queries users make go through the "spoofed" DNS server, which redirects them to a fake Chrome installation page.
If you are interested in technical analysis of Win32 / Sality DNS changer you can find it on its website ESET