Espionage is a network packet sniffer that tracks large amounts of data passing through an interface.
The tool allows users to perform regular and detailed motion analysis showing a live data flow, revealing packet directions, protocols, flags, etc.
It can thus forge ARP so that all data sent from the target is redirected via a MiTM attack.
Espionage supports IPv4, TCP / UDP, ICMP and HTTP. Scapy support is also available so users can run in-depth sniffs using the Scapy library. Espionage is written in Python 3.8, but also supports version 3.6. This is the first version of the tool, so contact the developer if you would like to contribute and add more to Espionage.

Installation
1: git clone https://www.github.com/josh0xA/Espionage.git
2: cd Espionage
3: sudo python3 -m pip install -r requirements.txt
4: sudo python3 espionage.py –help
Use
- sudo python3 espionage.py –normal –iface wlan0 -f capture_output.pcap
Command 1 will execute a clean package sniff and save the results to the pcap file. Replace wlan0 with whatever your network interface is. - sudo python3 espionage.py –verbose –iface wlan0 -f capture_output.pcap
Command 2 will execute a more detailed (root) package sniff and save the supplied pcap file. - sudo python3 espionage.py –normal –iface wlan0
Command 3 will continue to run a clean packet sniff, but will not save the data to a pcap file. It is recommended to save the packages. - sudo python3 espionage.py –verbose –httpraw –iface wlan0
Command 4 will execute a root packet sniff and will also display raw http / tcp packet data in bytes. - sudo python3 espionage.py –target
address> –iface wlan0
Command 5 will spoof ARP packets to address ip of the destination and all data sent will be returned to the attackers machine (to you / localhost).
- Press Ctrl + C to stop tracking packets and save the data as it exits the file.
Options menu
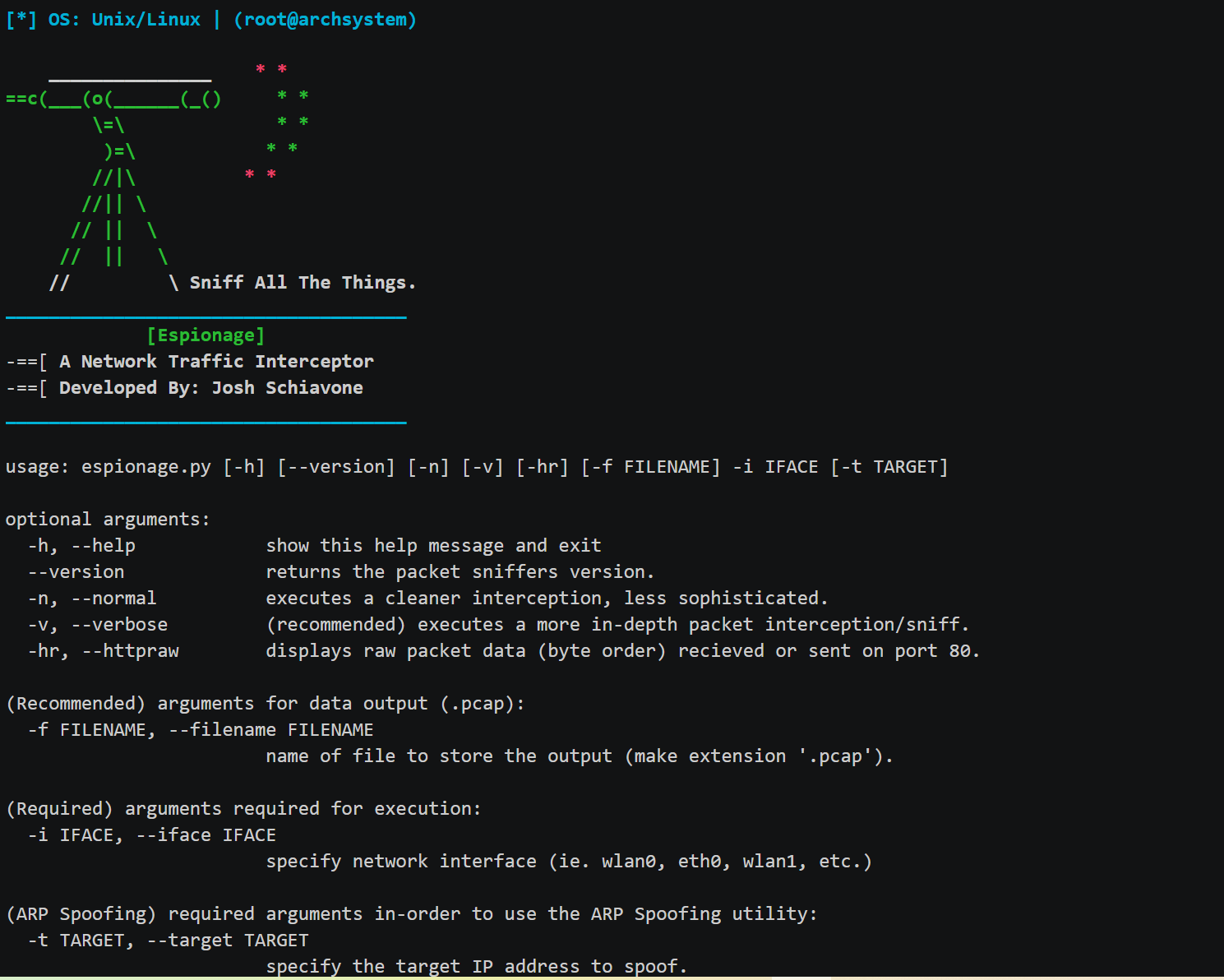
usage: espionage.py [-h] [--version] [-n] [-v] [-hr] [-f FILENAME] -i IFACE [-t TARGET] optional arguments: -h, --help show this help message and exit --version Returns the packet sniffers version. -n, --normal executes a cleaner interception, less sophisticated. -v, --verbose (recommended) executes a more in-depth packet interception/sniff. -hr, --httpraw displays raw packet data (byte order) recieved or sent on port 80. (Recommended) arguments for data output (.pcap): -f FILENAME, --filename FILENAME name of file to store the output (make extension '.pcap'). (Required) arguments required for execution: -i IFACE, --iface IFACE specify network interface (ie. wlan0, eth0, wlan1, etc.) (ARP Spoofing) required arguments in-order to use the ARP Spoofing utility: -t TARGET , --target TARGET specify the target IP address to spoof.
Video guide
https://asciinema.org/a/suAKny1Hh7Ai7L6jedrDoJqbZ





