Evilginx2 is one Framework man-in-the-middle attack that usesfor capturing online login credentials fishing (phishing) with me cookie session, which in turn allows 2-factor authentication (2FA) to be bypassed.
This tool is the successor to Evilginx, released in 2017, which used a customized version of the nginx HTTP server for man-in-the-middle functionality. So it could act as an intermediary between a browser and a phishing site.
This version is completely written from scratch and works like a standalone application, running its own HTTP and DNS server, making it extremely easy to set up and use.
Installation
[pastacode manual=”sudo%20apt-get%20-y%20install%20git%20make%0D%0Agit%20clone%20github.com%2Fkgretzky%2Fevilginx2%0D%0Acd%20evilginx2%0D%0Amake” provider=”manual” lang=”php”/] ή[pastacode manual = ”sudo% 20make% 20install% 0D% 0Asudo% 20evilginx” provider = ”manual” lang = ”php” /]
Use
[pastacode manual=”Usage%20of%20.%2Fevilginx%3A%0D%0A-debug%0D%0AEnable%20debug%20output%0D%0A-p%20string%0D%0APhishlets%20directory%20path” provider=”manual” lang=”php”/]Video guide
https://www.youtube.com/watch?v=8mfsF5Qdqw0
Application snapshots
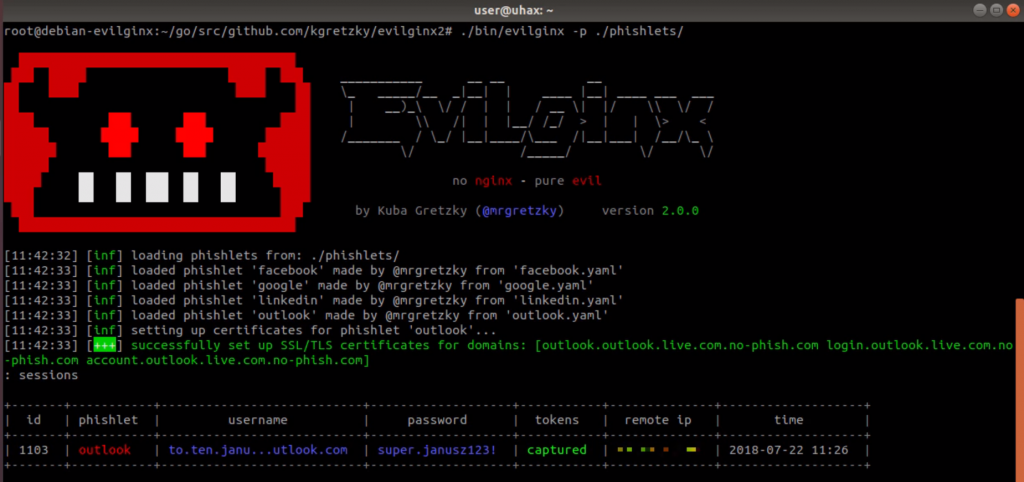
You can download the program from here.






