GrayKey: Encryption protects. The Internet would be a very dangerous place without encryption, as would Wi-Fi hotspots, or any device that uses protection with passwords like iPhone.
However, the iPhone no longer protects you as it once did. In the US, authorities use a cheap tool to bypass iPhone encryption.
Below we will deal with new tool GrayKey, what does it do, why is it dangerous and why is Apple worried?
Apple vs. FBI
Before we talk about GrayKey, let's just look at how the iPhone encryption began.
Those who are into technology (and beyond) will remember San Bernardino's iPhone. After a terrorist attack in San Bernardino, the FBI asked Apple to create one backdoor cuts to the encryption that would let them bypass the security of the iPhone of one of the dead terrorists. Apple refused, stating that if a backdoor was created, anyone could access its devices.
Eventually an Israeli security company, Cellebrite, found a way to bypass Apple's security mechanisms using an unknown vulnerability. At that time Cellebrite's service cost 5.000 dollars per device and the phone should be shipped to the company's premises.
2017 was marketed by Grayshift. It has a new revolutionary product called GrayKey. The purpose of GrayKey was not clear until Thomas Fox-Brewster revealed his function at Forbes, presenting several photos showing what exactly GrayKey's iPhone Unlocker does.
The GrayKey iPhone Unlocker
The GrayKey device is a small, gray box. It has two Lightning Cables.
The iPhone connects to the GrayKey device for about two minutes, but the actual process time varies depending on the strength of the password.
To break the device, an easy brute-force password takes about two hours to break with violent force, and for the most difficult codes (six digits) it may take three days or more.
When the iPhone passcode is detected, the phone will show a black screen showing the code along with others information device.
GrayKey downloads the entire iPhone
The program displays the device password but has downloaded the entire iPhone file system to the GrayKey device. GrayKey then connects to a Web service that performs the analysis.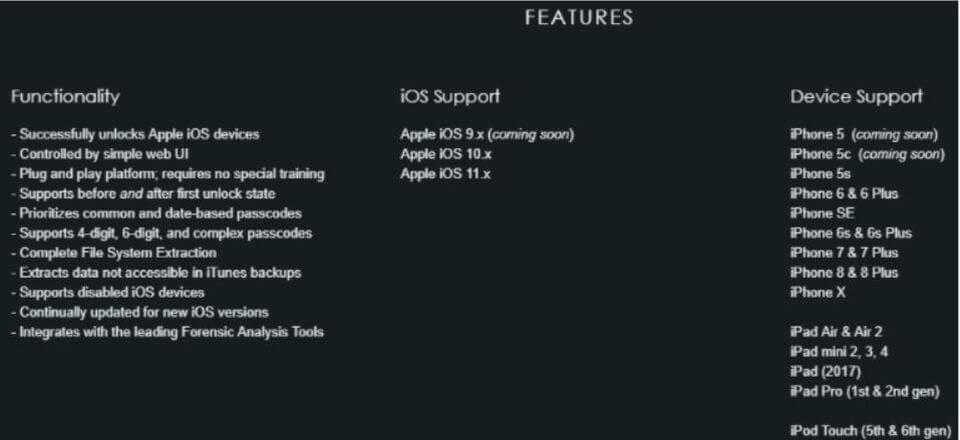
Picture Forbes
So the device can break any iPhone even the last iPhone X. When the process is complete it displays the following messages: "Password Found", "Software Version", "iTunes Backup" and "Full Filesystem". All of the above are available for download along with the SHA256 hash.
GrayKey costs…
GrayKey's iPhone Unlocker features two different versions. One version costs 15.000 dollars and requires an internet connection to operate while the second one costs $ 30.000 and is offline, and no limit on the number of uses of the GrayKey device.
The device will probably work until Apple detects the vulnerability and fixes it.
What does Apple do to stop GrayKey?
As you can imagine, Apple is not very satisfied with the situation. The company is currently testing the iOS 12 beta publicly. The new feature has a new feature that drastically restricts access to the Lightning Port on a locked iPhone.
IOS 12 may make brute-force attacks unnecessary through the Lightning Port by disabling access from this route. The new USB Restricted Mode will stop any data communication, which will make GrayKey useless.
The situation we described above may not last long, unless Grayshift continues to find vulnerabilities in Apple's operating system. So we are once again talking about the game catand mouse, which is welcomed by law enforcement as they can finally access Apple devices.
Of course Apple will have to consider a lot of questions that arise when a device is broken. Will the iPhone that "broke" be permanently vulnerable? Can the iPhone owner use his phone again normally or should he replace it?
___________________________________
- The Brave browser now has a private tour through Tor
- iPhone X is worth buying? Why some people said no
- Apple or Google? Apple or Samsung? Read before you answer





