The researchers of ESET, according to the recent reportssolutions των banking Trojans που πλήττουν τη Λατινική Αμερική, προχώρησαν στην ανατομία του Guildma, του πιο ισχυρού και προηγμένου banking Trojan that they had ever encountered of this group in that particular area.
This malicious software specifically targets banking institutions, trying to steal credentials for email accounts, e-shops and streaming services in Brazil. It has infected at least 10 times more victims than other Latin American banking Trojans analyzed by ESET. During the peak period – a massive campaign in 2019 – ESET recorded up to 50.000 attacks per day. Guildma spreads exclusively through spam emails with malicious attachments.
In one of its latest releases, Guildma used a new way of distributing command and control servers, abusing profiles in YouTube and Facebook. However, its operators stopped using Facebook almost immediately and, at least at this stage, rely entirely on YouTube.
“Guildma uses very innovative execution methods and sophisticated attack techniques. The actual attack is orchestrated by the C&C server. In this way, its operators can react more flexibly to the countermeasures applied by the banks when they are attacked," explains Robert Šuman, the ESET researcher who leads the team analyzing Guildma.
Guildma has multiple backdoor functions, such as taking screenshots, recording keystrokes, simulating mouse and keyboard functions, blocking shortcuts (such as disabling Alt + F4 to make it harder for fake windows to disappear) , and / or reboot. In addition, Guildma has a highly modular architecture, currently consisting of at least 10 modules. The malware uses tools that are already on the machine and reuses its own methods. "From time to time new techniques are added, but for the most part, developers just seem to be reusing techniques from older versions," says Šuman.
In one of the first editions of Guildma in 2019, the possibility of targeting institutions (mainly banks) outside Brazil was added. However, in the last 14 months, ESET has not detected any international campaigns outside the country. In fact, the attackers went so far as to block downloads from IP addresses outside Brazil.
Guildma's campaigns escalated slowly until the massive campaign in August 2019, when the ESET Research Team recorded up to 50.000 samples per day. This campaign continued for almost two months, reaching more than double the amount detected 10 months ago.
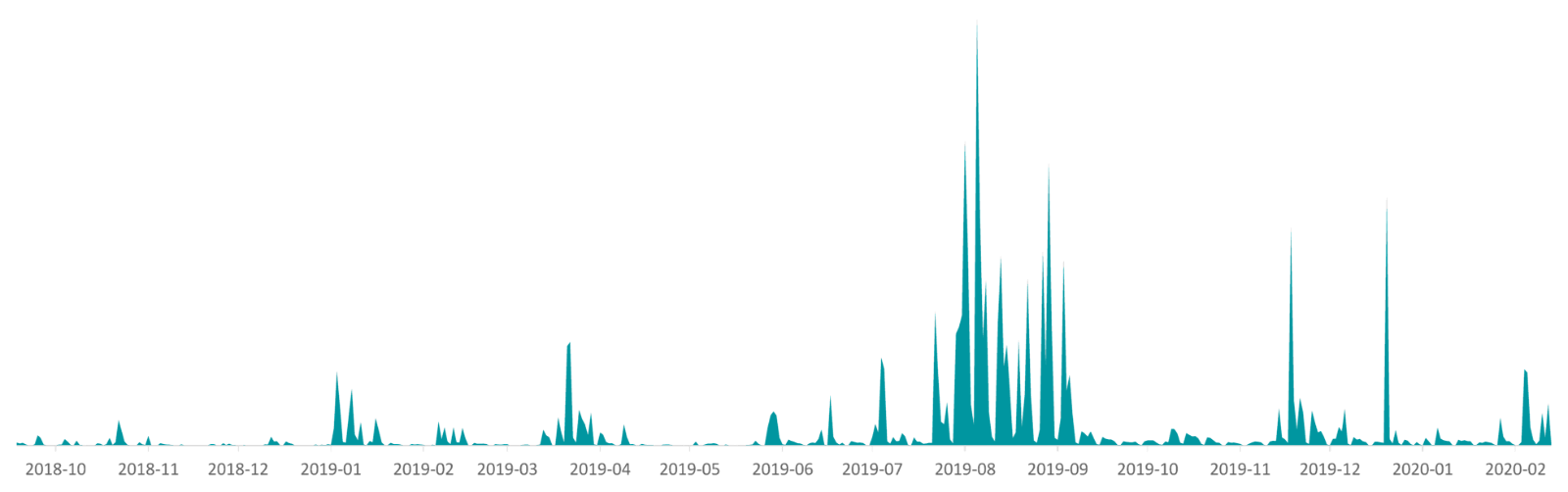
The trojan has changed many versions during its development, but there has usually been very little evolution between versions due to its "rigid" architecture.
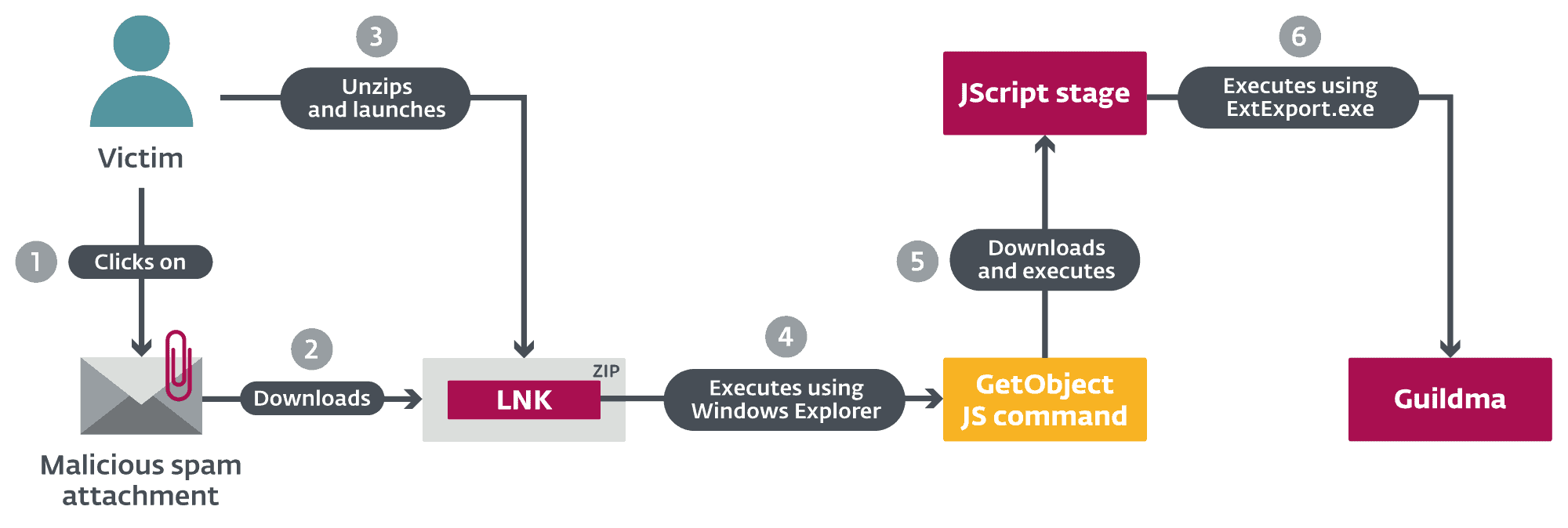
Guildma has several of the key features of Latin American banking trojans. For more technical details, read the blog post «Guildma: The devil electric drives»On WeLiveSecurity.





