One of the experts in its Global Research and Analysis Team Kaspersky Lab conducted field research (hacking) at a private clinic in an effort to discover potential security weaknesses and ways to address them. Vulnerabilities were found in medical devices that "opened the door" for digital criminals to access patients' personal data and more broadly their "well-being". 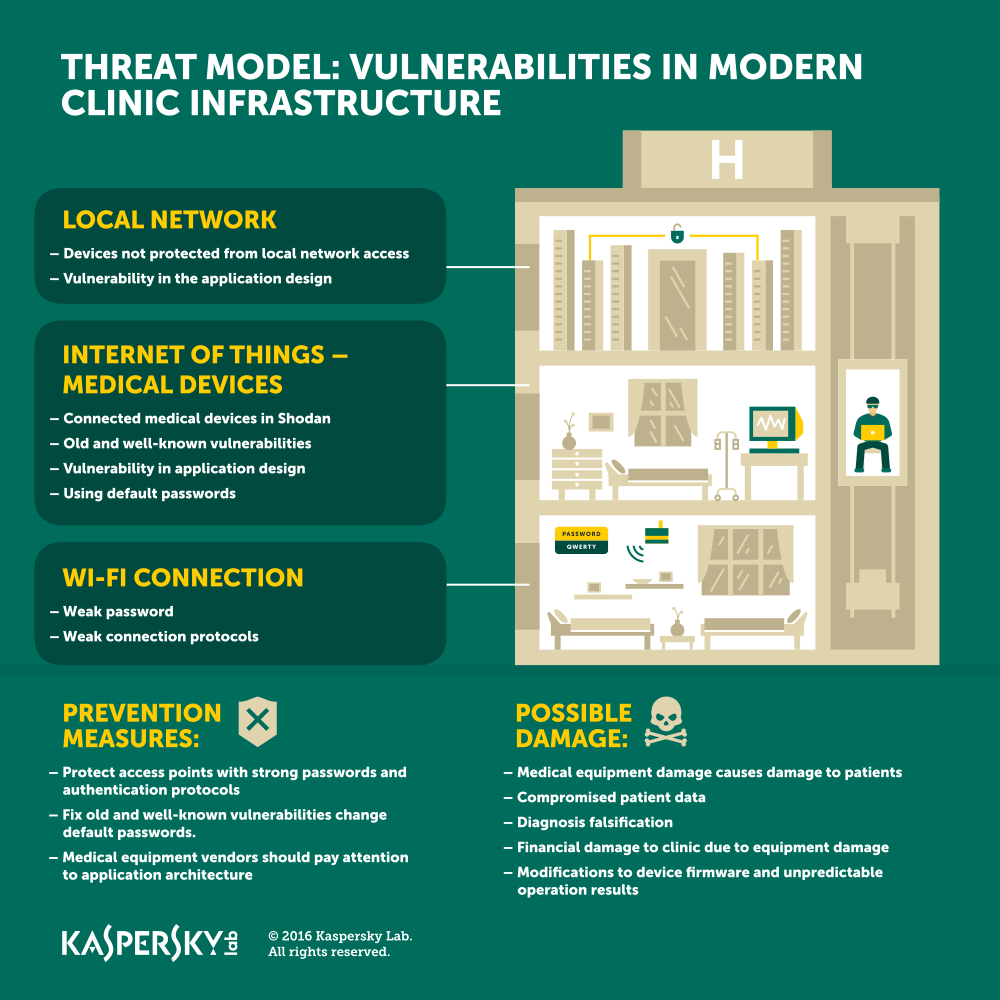
A modern clinic is a complex system. It has sophisticated medical devices that include fully functional computers, with an operating system and installed applications. Doctors rely on computers and all information is stored in digital form. In addition, all technologies in the Healthcare sector are connected to the Internet. So it's no surprise that both medical devices and hospital IT infrastructures have been targeted by hackers before. The most recently examples of such incidents are ransomware attacks against hospitals in USA and Canada. However, a large-scale malicious attack is only one of the ways in which criminals could exploit the IT infrastructure of a modern hospital.
Clinics store their patients' personal information. They may also have in their possession and use very expensive, difficult to repair and replace equipment, features that make them a potentially valuable target for data blackmail and theft.
The result of a successful hacking against a medical organization could vary in detail, but it is always dangerous. Among other things, it could include the following:
- Malicious use of personal patient data, such as reselling the information to third parties or soliciting paymentRansomware from the clinic to retrieve sensitive patient information
- Deliberate misrepresentation of exam results or diagnoses
- Damage to medical equipment that could cause both physical harm to patients and enormous financial losses in the clinic
- Negative impact on the reputation of a clinic
Report on the Internet
The first thing the Kaspersky Lab expert decided to investigate was understanding how many medical devices around the world are now connected to the Internet. Modern medical devices are fully functional computers with their own operating system. At the same time, most of them have a communication channel with the Internet. By hacking them, criminals could affect their functionality.
A quick look at the Shodan search engine for Internet-connected devices has shown that hundreds of devices - from MRI to cardiology equipment, nuclear medicine devices and other related devices - are registered there. This discovery leads to worrying conclusions. Some of these devices still run old operating systems like Windows XP, which do not have the relevant patches for the vulnerabilities that have been discovered. Also, some of the devices still use the default passwords, which can be easily found in publicly accessible manuals.
Using these vulnerabilities, criminals could gain access to a device's interface and potentially affect how it works.
Inside the clinic's local network
The above scenario was one of the ways digital criminals could gain access to vital clinic infrastructure. But the most obvious and logical way is to try to attack its local network. During the investigation, a vulnerability was detected in the clinic's Wi-Fi connection. Through a weak communication protocol, access to the local network was obtained.
Investigating the local network of the clinic, the Kaspersky Lab expert identified some medical equipment previously found in Shodan. This time, however, to gain access to the equipment, no one needed a password, because the local network was a reliable network for medical equipment applications as well as for users. And that's the way a digital criminal can access a medical device.
Investigating the network further, the Kaspersky Lab expert discovered a new vulnerability in a medical device application. A command shell was implemented in the user interface. The latter could give cybercriminals access to personal patient information, such as medical history and information about medical analyses, as well as their addresses and data their identity. Furthermore, the entire device controlled through this application could be compromised through this vulnerability. For example, among these devices could be MRI scanners, cardiac equipment, nuclear medicine devices and surgical equipment. What could this entail? First, criminals could change how the device works and cause physical harm to patients. Second, criminals could damage the device itself, causing a huge financial loss to the hospital.
“Clinics no longer consist only of doctors and medical equipment, but also of IT services. The work of a clinic's internal security services affects the security of patient data and the functionality of its devices. Medical software and equipment manufacturers put a lot of effort into creating a useful medical device that will save and protect human life, but sometimes they completely forget to protect it from unauthorized external access. When it comes to new technologies, the issues safety issues should be addressed during the first stage of the Research and Development (R&D) process. IT security companies could contribute at this stage by helping to address security issues.” commented Sergey Lozhkin, Senior Researcher, Kaspersky Lab's Global Research and Analysis Team.
Kaspersky Lab specialists propose the following steps to protect clinics from unauthorized access:
- Use strong passwords to protect all external connection points
- Updating information security policies and developing early patch and vulnerability assessment systems
- Protect the applications of medical devices on the local network with passwords in the event of unauthorized access to the trusted site
- Protect infrastructure from threats such as malicious software and hacking attacks through a credible security solution
- Back up critical information on a regular basis and maintain an offline backup
More information about health insurance is available in a related blogpost, on the site Securelist.com.





