According to Kaspersky Digital Footprint data market, the percentage of enterprise devices infected with data-sniffing malware has increased by a third since 2020. Additionally, the malware was executed more than once in 21% of these cases. In response to the growing threat posed by infostealers to corporate users, the Kaspersky Digital Footprint Intelligence team draws attention to businesses and employees, while offering tactics to counter the respective risks.
Kaspersky revealed a worrying trend: corporate devices face an ever-increasing threat from infostealers. According to data extracted from data-stealing malware logs available on the dark web, the percentage of enterprise users exposed to such malware has increased by 34% from 2020 to today.
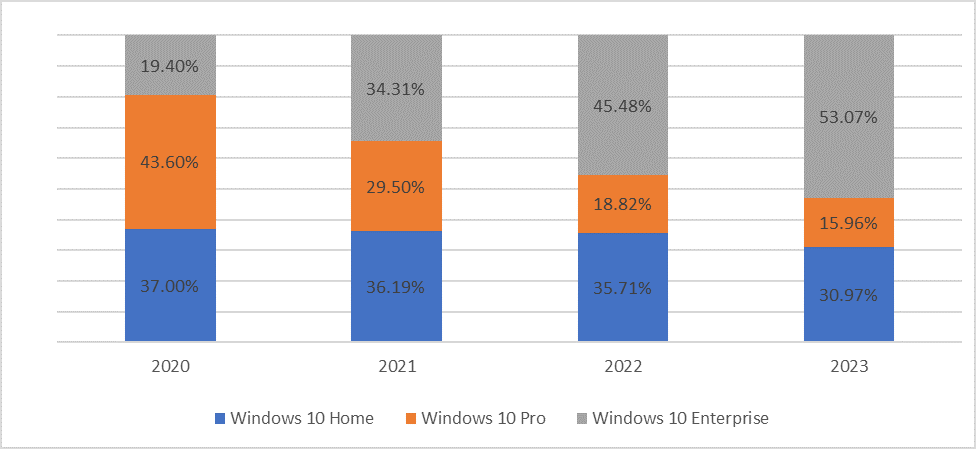
In 2023, Kaspersky experts concluded that more than half of devices (53%) infected with credential-stealing malware were corporate. At the same time, based on the findings, the largest share of infostealer infections was found in version Windows 10 Enterprise. The chart below shows the distribution of attacks between different versions of Windows 10, spanning from 2020 to 2023.
Distribution of attacks across Windows 10 releases, 2020-2023
Μολύνοντας απλά μια και μόνο συσκευή, οι κυβερνοεγκληματίες μπορούν να αποκτήσουν πρόσβαση σε όλους τους λογαριασμούς - προσωπικούς και εταιρικούς. Σύμφωνα με στοιχεία της Kaspersky, ένα αρχείο καταγραφής περιέχει τα προσωπικά στοιχεία εισόδου, κατά μέσο όρο, σε 1,85 εταιρικές εφαρμογές web, συμπεριλαμβανομένων μεταξύ άλλων των εφαρμογών web mail, συστημάτων επεξεργασίας δεδομένων πελατών και εσωτερικών συστημάτων.
"We were interested in finding out if corporate users re-execute the malware, thereby allowing cybercriminals to regain access to data collected from a previously compromised device without having to re-infect it," comments Sergey Shcherbel, an expert at Kaspersky Digital Footprint Intelligence.
«Για να το διερευνήσουμε αυτό, εξετάσαμε ένα δείγμα αρχείων καταγραφής που τα δεδομένα αφορούσαν περίπου 50 τραπεζικούς οργανισμούς από διάφορες χώρες. Διαπιστώσαμε ότι το 21% των εργαζομένων επανεκτέλεσαν το κακόβουλο λογισμικό, ενώ το 35% των περιπτώσεων συνέβη περίπου τρεις ημέρες μετά την αρχική contamination. Αυτό μπορεί να υποδηλώνει διάφορα προβλήματα, όπως η ανεπαρκής ενημέρωση των εργαζομένων, τα αναποτελεσματικά μέτρα ανίχνευσης και αντιμετώπισης των απειλών, η πεποίθηση ότι η change of the password is sufficient if the account has been compromised and reluctance to investigate the threat further.
More information on the infostealer threat landscape can be found at Kaspersky Digital Footprint Intelligence website.
To reduce the impact of a infringementof data caused by infostealer, we suggest you follow the steps below:
• Immediately change passwords for compromised accounts and stay alert for any suspicious activity.
• Advise any infected users to run antivirus scans on all devices to remove any malware
• Monitor the dark web for compromised accounts to identify compromised accounts before they impact customer or employee digital security. Here you can find a detailed control guide.
• Use Kaspersky Digital Footprint Intelligence to detect potential threats and deal with them immediately.
• For enhanced protection against infostealers threats, develop a security training program for employees, thereby offering continuous updating and evaluation.