Security company F-Secure appears to have discovered a strange sample “maliciousυ” software originating from the server network (botnet), which distributes the Locky ransomware.
Φυσιολογικά το malware ήταν ένα αρχείο ZIP σε μορφή JavaScript. Αν τώρα κάποιος χρήστης κάνει διπλό κλικ πάνω σε αυτό το JavaScript, το script would normally download the Locky ransomware which would immediately start encrypting the victim's data.
But this time, F-Secure researcher Päivi discovered that instead of Lócky, JavaScript put something different and completely harmless!
How is the event explained?
It seems that someone has violated Lócky's distribution network and replaced Locky ransomware with a file that is totally harmless.
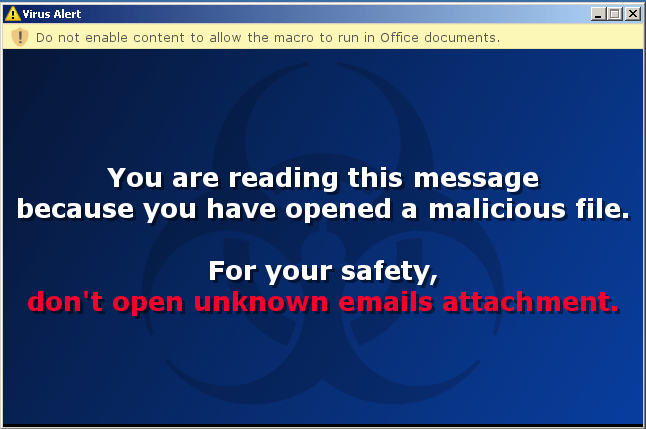
The file simply shows a prenotice if someone goes to open it, which says: “don't open email attachments from untrusted sources.”
"You have already opened a malicious file to read this message,
For your own safety, do not open email attachments from unreliable sources. ”