Lure10 Attack over Wi-Fi Sense: Karma has long been a key man-in-the-middle attack used for authorized wireless network security assessments. However, many modern operating systems and routers provide effective countermeasures, and thus need other approaches to cheating wireless clients.
We introduce you to Lure10: a new attack that exploits the Wi-Fi Sense feature of Windows.
What is Wi-Fi Sense?
Wi-Fi Sense, which is enabled by default on Windows 10 and Windows Phone 8.1, is a feature that automatically connects users to open wireless networks that they know (have reconnected to).
Based on the information gathered from various Windows devices that were connected to these open networks, Microsoft evaluates whether they provide a good quality connection and if they do, it adds them to the list of hotspots proposed by Wi-Fi Sense.
Wi-Fi Sense will select and show the user a network when within range, will automatically accept its terms of use and automatically link it to this network.
The Lure10 technique
The success of the attack presented by the security technician George Hadjisofronius at this year's conference Hack in the Box in Amsterdam is based on the following:
- The victim's device is misleading to believe it is within the geographic area of an open wireless network that bears the Wi-Fi Sense tag
- The attacker successfully interrupts the existing Wi-Fi connection of the victim's device (by falsifying DEAUTH frames) and
- Μιμείται επιτυχώς το εν λόγω δίκτυο Wi-Fi Sense (ένα δίκτυο με το ίδιο ESSID - extended service set identifier).
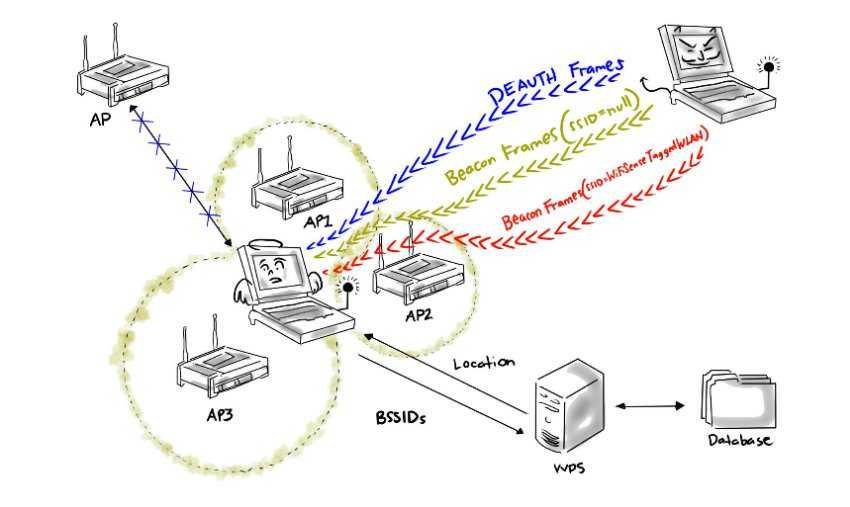
Αυτή η τελευταία προϋπόθεση μπορεί να επιτευχθεί με την εύρεση ενός δικτύου Wi-Fi Sense που υπάρχει σε κάποια περιοχή σχετικά κοντά στο θύμα (π.χ. στην πατρίδα του) και με την συλλογή του ESSID (π.χ. "AIRPORT_FREE").
At the same time, the attacker should also collect the BSSIDs of other wireless networks in the same area, as they are also used by the Windows discovery service to determine the location of a device.
With these BSSIDs, the attacker can fool Windows that think the device is in the area of the impersonation network (the first condition of the attack).
Once the attacker manages to perform these two steps, he begins to send beacon frames to the ESSID of the Wi-Fi Sense network he imitates. This is enough to automatically connect the victim's device if shared WLAN exists in the list of preferred networks and the list of available networks.
But even this last situation can be achieved. You can see the researcher presentations for more details.
How To Protect Yourself?
The Lure10 attack technique has been added to the latest version of the open source tool Wifiphisher Rogue Access Point, developed by George Hatzisoforion.
The researcher said that Microsoft has been informed about this issue, has recognized its seriousness but has not yet taken steps to correct it.
You can protect yourself from this attack by disabling Wi-Fi Sense on your device.





