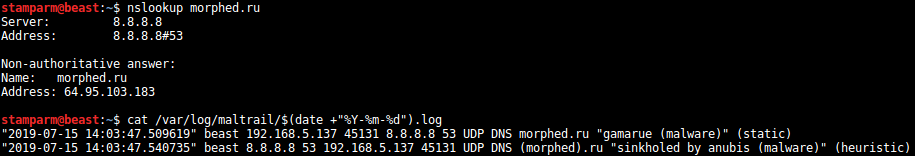
The Maltrail is a malicious traffic detection system that uses publicly available lists that contain malicious or generally suspicious "paths", along with static traces collected from various AV references and custom user-defined lists, where the trace can be anything by name , URL, IP address or user header value and HTTP.
It also uses advanced heuristic mechanisms that can help detect unknown threats.
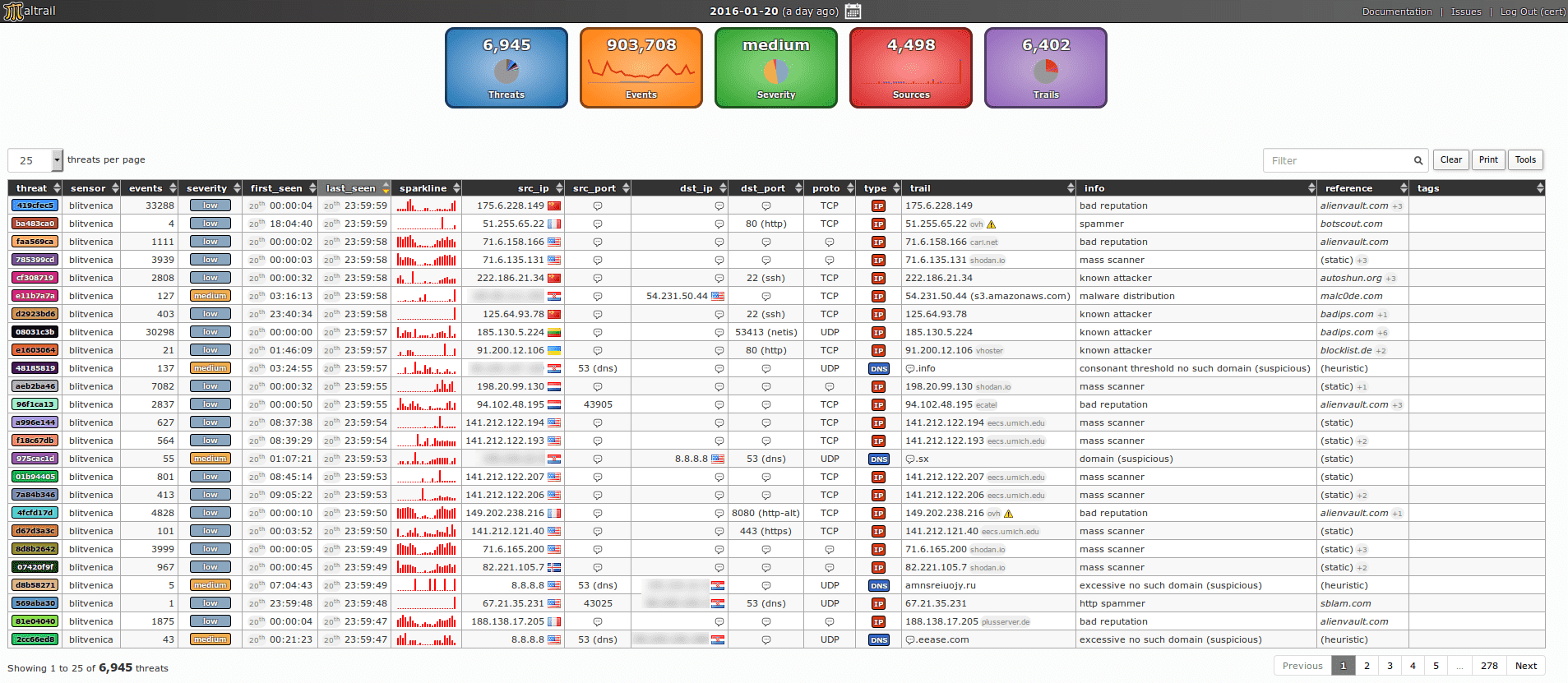
Architecture
Το Maltrail βασίζεται στην ακολουθία -> Αισθητήρας Διακομιστής Αρχιτεκτονική πελάτη. Το Sensor (s) είναι ένα αυτόνομο στοιχείο που λειτουργεί στον κόμβο παρακολούθησης (π.χ. πλατφόρμα Linux που συνδέεται παθητικά στη θύρα SPAN / mirroring ή διαφανώς ενσωματωμένη σε γέφυρα Linux) ή στο αυτόνομο μηχάνημα (π.χ. Honeypot) όπου «παρακολουθεί» την κυκλοφορία που περνά για objects / «μονοπάτια» black list (π.χ. ονόματα τομέα, διευθύνσεις URL ή / και IP).
In case of a positive match, it sends the details of the event to the (central) server where they are stored in the appropriate log directory (ie LOG_DIR described in the Configuration section).
If the sensor is running on the same computer as the server (default configuration), the logs are stored directly in the local log directory. Otherwise, they are sent via UDP messages to the remote server (ie LOG_SERVER described in the Configuration section).
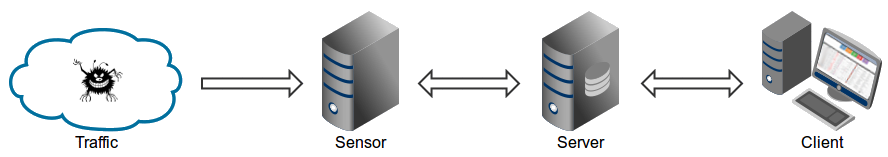
The primary role of the server is to store event details and provide support for the web reporting application. In the default configuration, the server and sensor will work on the same computer.
Thus, in order to avoid possible interruptions in the sensor activities, the front-end reference section is based on the “Fat client” architecture (ie all data after processing is done in the presence of the client's web browser).
The events (i.e. log entries) for the selected period (24 hours) are transferred to the client, where the web reporting application is solely responsible for the presentations. The data is sent to the client in compressed parts, where it is processed sequentially. The final report is created in a condensed format, allowing virtually an unlimited number of events to be presented.
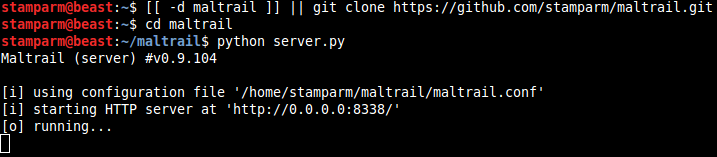
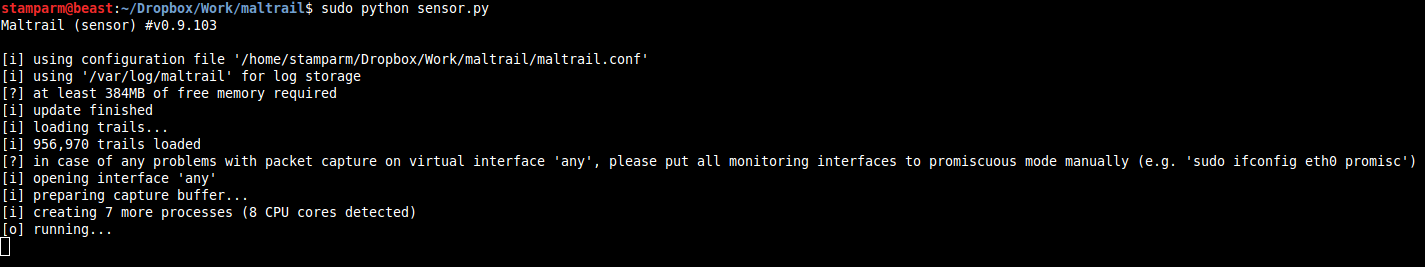
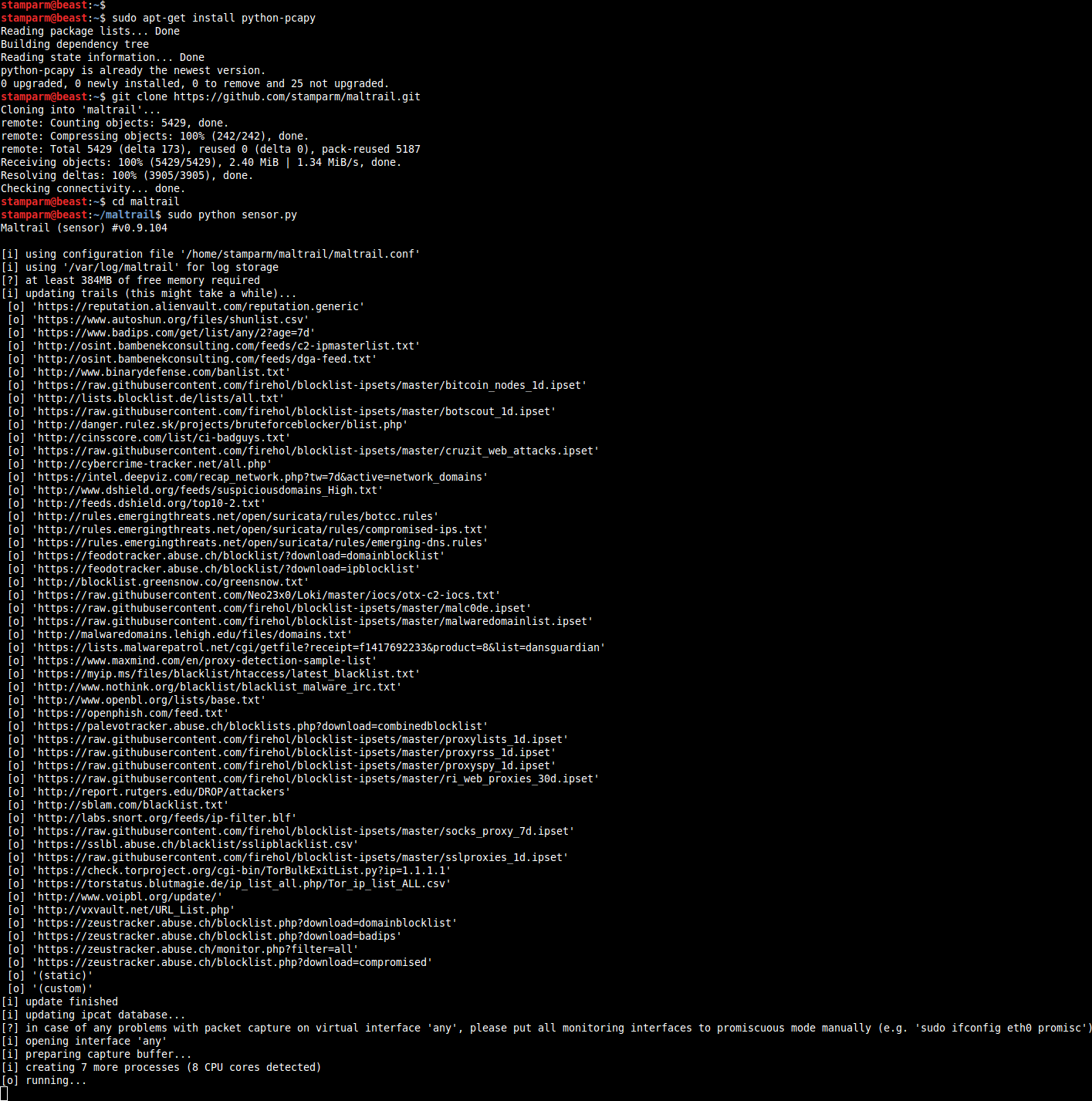
Installation
sudo apt-get install python python-pcapy git
git clone https://github.com/stamparm/maltrail.git
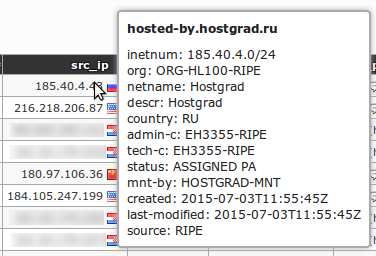
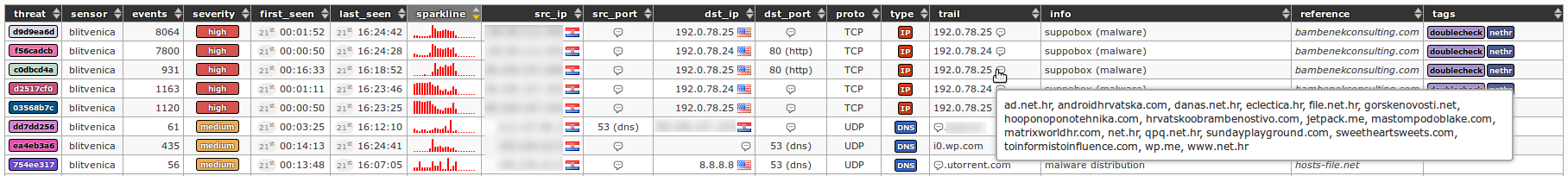
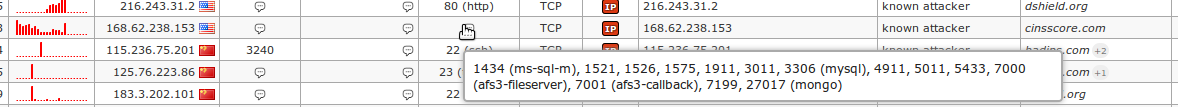
Application snapshots
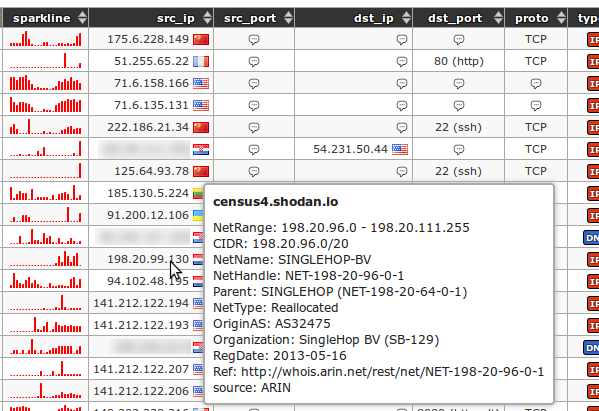
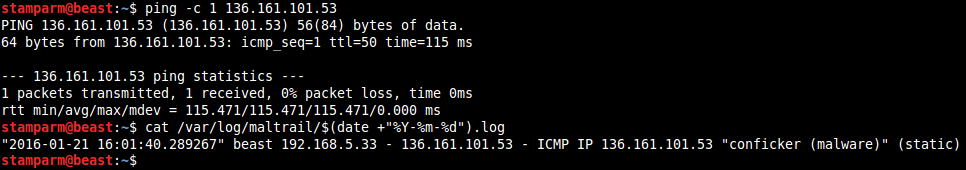
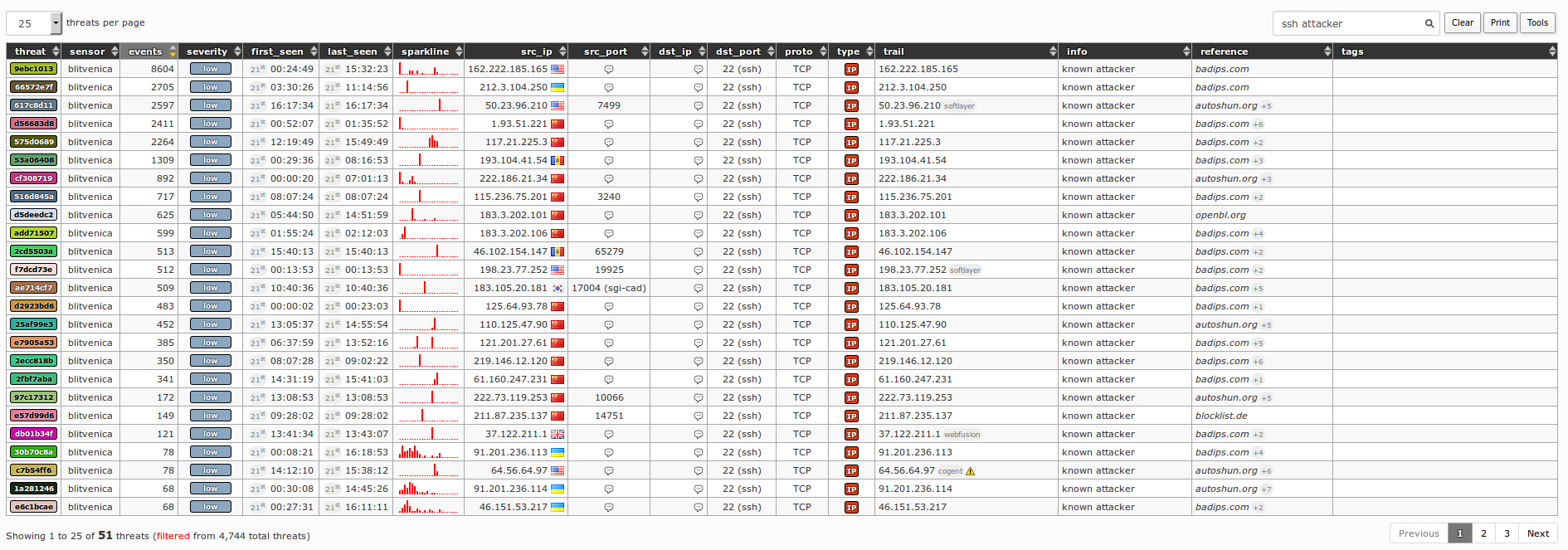

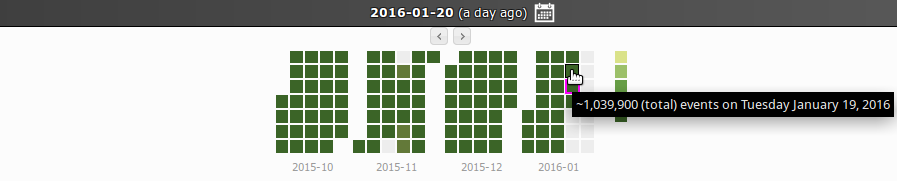
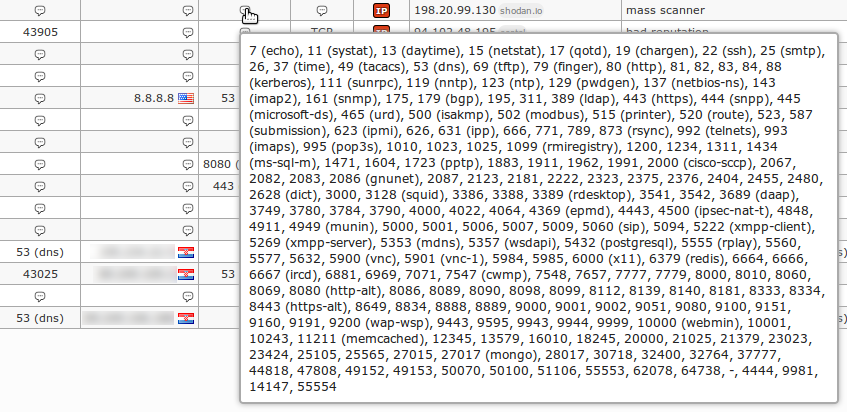

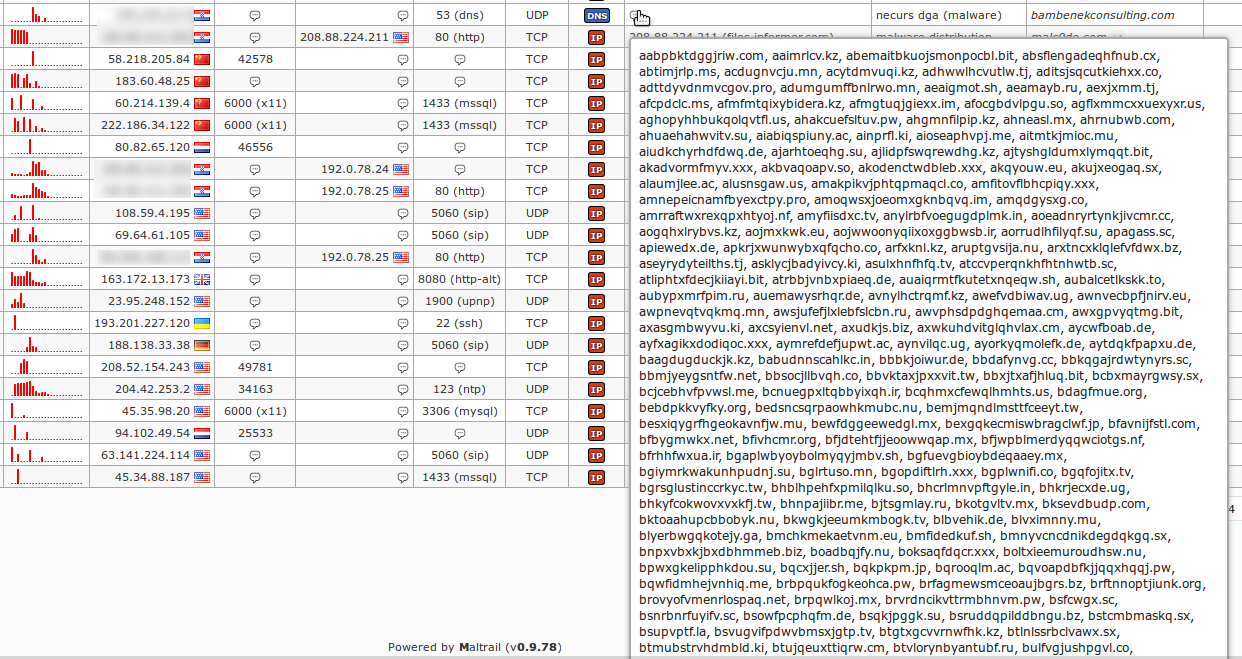
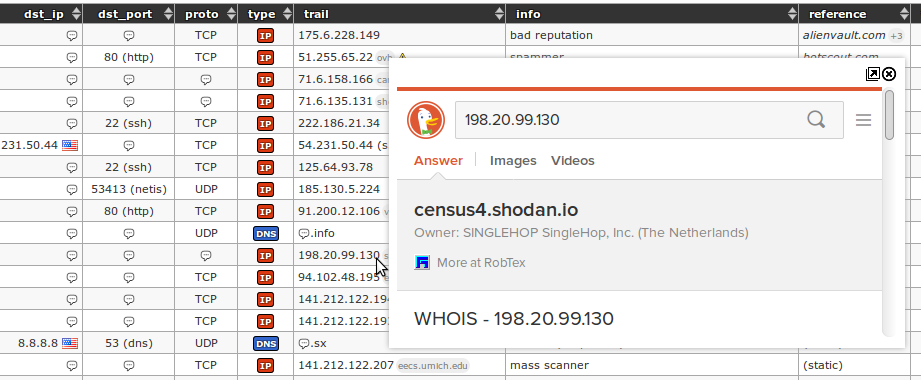
![]()
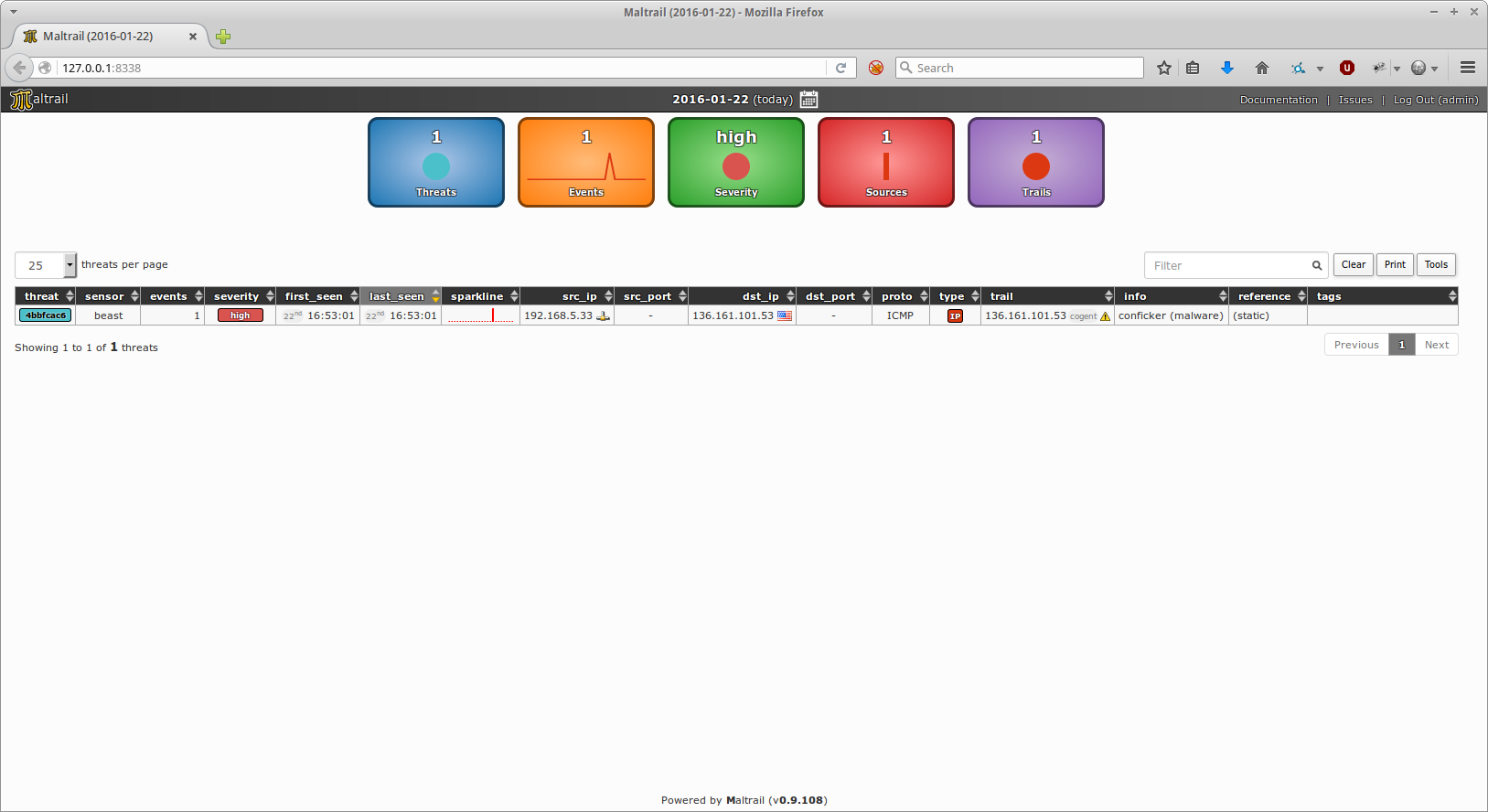
Information on using the program, you will find here.





