New Malvertising Attack: The DNSChanger exploit kit is back more efficient than ever. The new DNSChanger is widely used for malicious attacks targeting home routers. Note that home routers are also used by many companies…
According to researchers of Proofpoint, the main target of attackers is the DNS records on the target router. This way all queries go through the attacker's DNS servers. 
What is the benefit of malvertising for invaders?
Victims are served with ads that bring money to the attackers. Of course, malicious actions do not stop in distributing ads.
"When attackers take control of a DNS server on a network, they can carry out a wide range of malicious actions on devices connected to the network. These include bank fraud, man-in-the-middle attacks, phishing, ad fraud, and more. In this case, the DNSChanger exploit kit allows attackers to use the internet router itself, "said Proofpoint researcher Kafeine.
How does this Malvertising attack work?
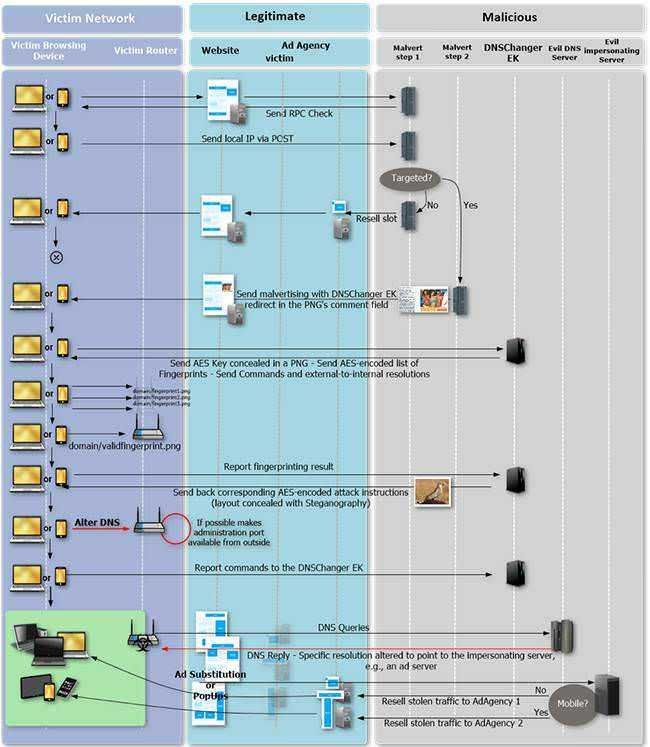
Everything starts with ads on legitimate websites. When served to a potential victim, they ping the attacker's server by offering it its local IP address.
If the IP address is already known or does not exist in the targeted areas, the user is served with a legitimate ad and the attack stops there.
However, if the IP addresses the attacker's requirements, a malicious ad (a PNG file) containing HTML code that redirects the victims into the destination page of the DNSChanger exploit kit is served to the victim. There are some JavaScript that start running various functions.
After checking the IP address (once again), the DNSChanger exploit kit loads multiple functions and an AES key that is concealed in a small image.
“This key will be used to decrypt the [router] list fingerprints Kafeine reports. "Then with the victim's browser, the malicious users will try to locate the router in use on the network."
The results were sent back to the exploit kit, which then sends instructions on how this particular router model can be violated.
Once the router is compromised, the settings of DNS. So attackers can intercept traffic from some large advertising companies.
How to protect yourself?
The list of routers that includes the exploit kit is great, and potentially vulnerable router models are not easy to detect.
"The safest approach for end users is to consider that all known exploits are contained in this exploit kit, so all routers should be updated to the latest known firmware," advises Kafeine. Of course, if the manufacturers do not have secure firmware this is another matter.
If you also use ad blocking software, you can minimize the risk of being infected by malicious advertising campaigns.
According to Caffeine, the current campaign is targeting Chrome users on Windows computers and Android devices.





