Adwind: Its Global Research and Analysis Team Kaspersky Lab published an extensive research on the Remote Access Tool (RAT) Adwind, a multi-malicious malware that affects multiple platforms. This program is also known as AlienSpy, Fruits, Unrecom, Sockrat, JSocket and jRat and is distributed through a platform "Malware-as-a-Service".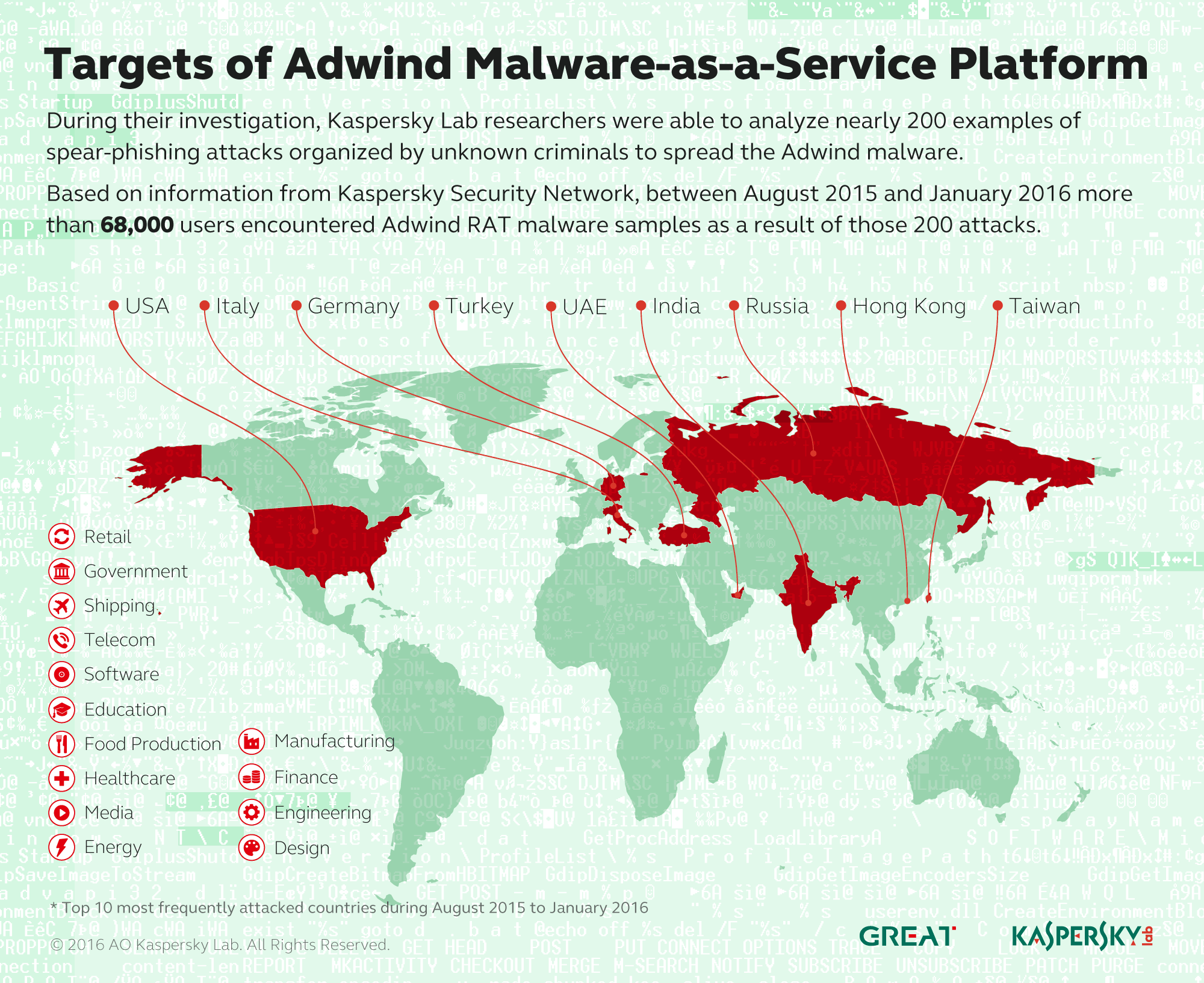
According to research findings, conducted between 2013 and 2016, different versions of Malware Adwind have been used in attacks by at least 443.000 users, businesses and non-commercial organizations around the world. The platform and the malicious software are still active. 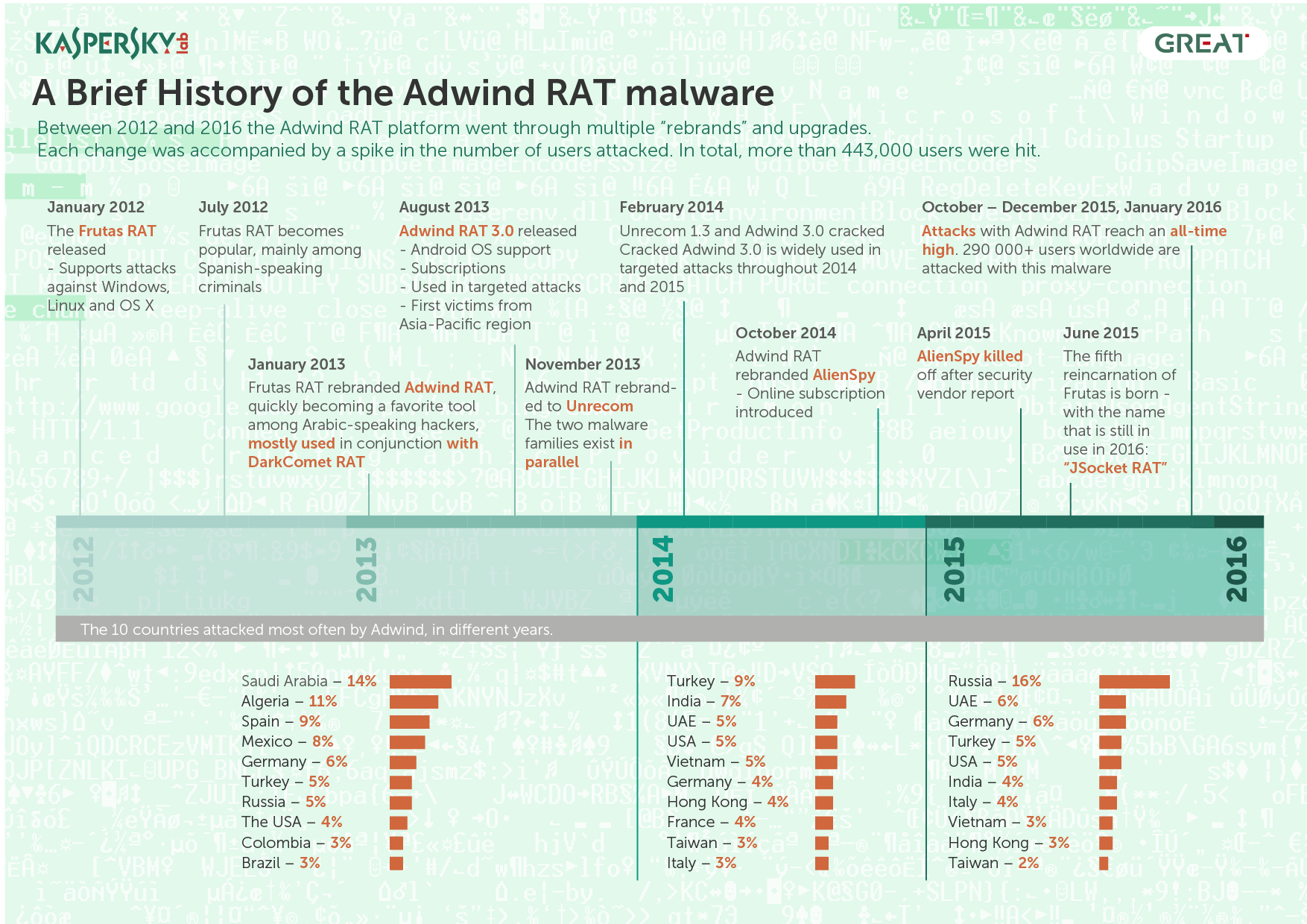
Στα τέλη του 2015, οι ερευνητές της Kaspersky Lab έλαβαν γνώση για ένα ασυνήθιστο κακόβουλο πρόγραμμα, το οποίο είχε ανακαλυφθεί κατά τη διάρκεια μιας απόπειρας στοχευμένης επίθεσης εναντίον μιας bankς στη Σιγκαπούρη. Ένα κακόβουλο αρχείο JAR ήταν συνημμένο σε ένα spear-phishing email που στάλθηκε σε υπάλληλο της τράπεζας. Οι πλούσιες δυνατότητες του κακόβουλου λογισμικού, συμπεριλαμβανομένης της ικανότητα να «τρέχει» σε πολλαπλές πλατφόρμες, καθώς και το γεγονός ότι δεν εντοπίστηκε από οποιαδήποτε λύση antivirus, τράβηξαν αμέσως την προσοχή των ερευνητών.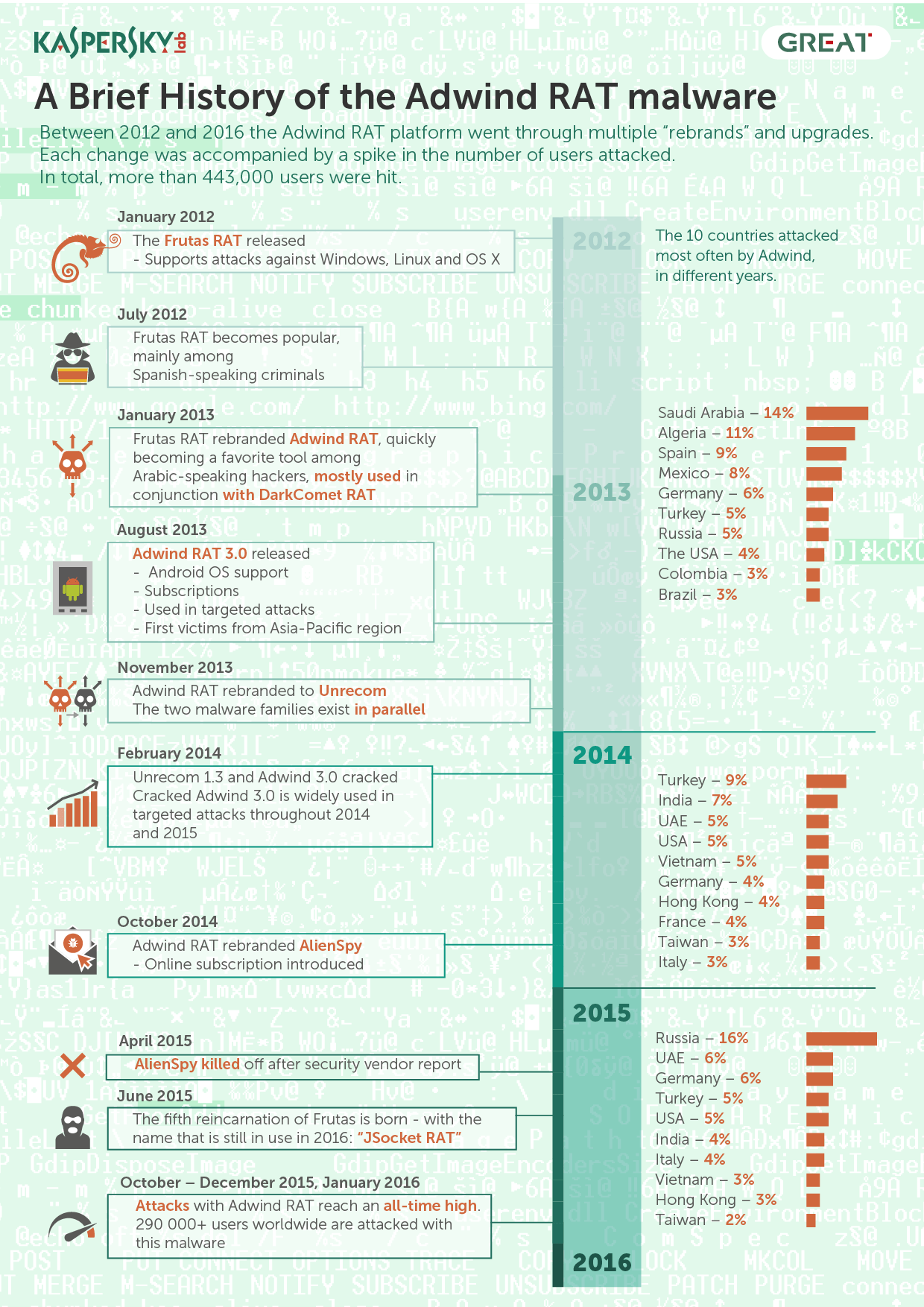
Adwind RAT
It turned out that the organization was attacked by Adwind RAT, a backdoor program that was available for purchase and "written" entirely in Java language, elements that make it capable of influencing and operating on multiple platforms. This program can run on platforms running Windows, OSX, Linux and Android, providing features for remote desktop control, data collection, data mining, and more.
If the target user opens the attached JAR file, the malware installs itself and tries to communicate with the command and control server. The list of malware features includes options for:
- Keystroke interception
- Tracking cached passwords and data from online formats
- Download screenshots
- Take photos and record video via webcam
- Microphone recording
- Transferring folders
- Collecting general information about system and user
- Handwriting of keys for electronic money purses
- Manage SMS messages (for Android platforms)
- Theft of VPN certificates
Although it is mainly used by aggressively acting aggressors and distributed to massive spam campaigns, there are cases where Adwind was used in targeted attacks. In August of 2015, references to Adwind were found in publications which concerned a case of digital espionage against an Argentine prosecutor, who was finally found dead in January of 2015. The incident against the bank in Singapore was another example of a targeted attack. A deeper look at events related to the use of Adwind RAT showed that these targeted attacks were not the only ones.
The goals
During the investigation, Kaspersky Lab experts analyzed nearly 200 examples of spear-phishing attacks, organized by unknown criminals, with the aim of spreading Adwind malware. They were also able to identify the industries for which most of the targets worked. The list includes companies from industry, financial services, engineering and design, retail, government agencies, shipping companies, telecommunications providers, software companies, educational organizations, food, manufacturing and healthcare companies, media and business energy.
Based on information from Kaspersky Security Network, the 200 examples of spear-phishing attacks observed from August 2015 to January 2016 showed that over 68.000 users encountered samples of the Adwind RAT malware.
Κατά την ίδια περίοδο, η γεωγραφική κατανομή των χρηστών που δέχτηκαν επίθεση και έχουν καταχωρηθεί στο KSN, δείχνει ότι σχεδόν οι μισοί από αυτούς (49%) ζούσαν στις ακόλουθες 10 χώρες: Ηνωμένα Αραβικά Εμιράτα, Γερμανία, Ινδία, ΗΠΑ, Ιταλία, Russia, Βιετνάμ, Χονγκ Κονγκ, Τουρκία και Ταϊβάν.
Based on the profile of the recognized goals, Kaspersky Lab researchers believe that Adwind customers are in the following categories: fraudsters wanting to go to the next level (using malware for more advanced scams), unfair media , digital mercenaries (spies who rent out their services) and individuals who want to spy on people they know.
Threat-as-a-Service
One of the main features that Adwind RAT distinguishes from other "commercial" malware programs is that it is distributed openly in the form of a paid service where the "customer" pays a fee in exchange for using the malicious program. Based on a survey of user activity in the internal message board and some other observations, Kaspersky Lab researchers estimate that there were approximately 1.800 users in the system by the end of 2015. This is one of the largest malware platforms to date.
"The Adwind platform, in its current state, significantly reduces the minimum level of professional knowledge needed to enter the field of digital crime. What we can say, based on our investigation of the attack on the bank in Singapore, is that the criminal behind it has nothing to do with a "professional" hacker. We also believe that most of Adwind's "customers" have the same level of knowledge of Computer Science up and down. And this is a worrying trend, said Aleksandr Gostev, Chief Security Expert of Kaspersky Lab.
"Despite multiple reports about the different generations of this tool, which have been published by various security solutions providers in recent years, the platform is still active and used by criminals of all kinds. We conducted this research to draw the attention of the security community and the law enforcement authorities to take the necessary steps to stop the action of this platform completely, said Vitaly Kamluk, Director of Kaspersky Labia's Asia Pacific Research and Analysis Worldwide Group.
Kaspersky Lab has submitted its findings for the Adwind platform to the law enforcement authorities.
To protect users and organizations from this threat, Kaspersky Lab encourages businesses to review the feasibility of using a Java platform and block it for all unauthorized sources.
More information on the "Malware-as-a-Service" Adwind Platform is available on the site Securelist.com.
More information on how investigations are conducted on advanced targeted attacks are available on Kaspersky Lab's videos YouTube.
More information about digital espionage companies can be found on the site https://apt.securelist.com/.





