The Mandiant RedLine is one of the free tools that help in conducting a digital forensic research.
Specifically it is one tool ελέγχου το οποίο συλλέγει όλες τις διεργασίες και τους οδηγούς από τη μνήμη, το ιστορικό του δικτύου , τις information network, system stream files, registry data, and event logs.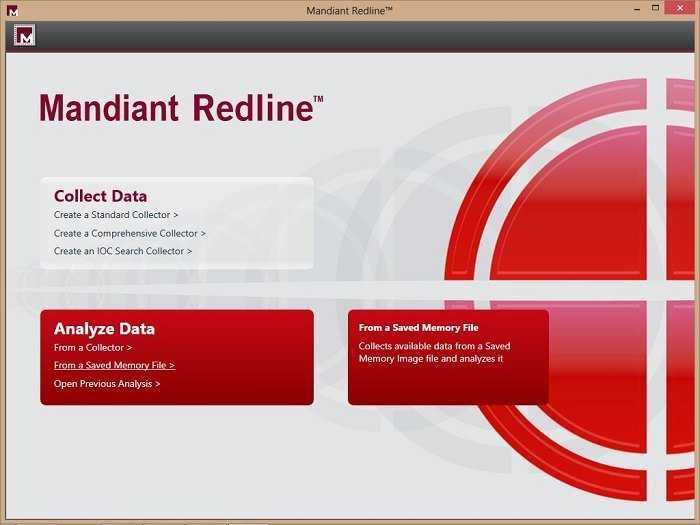
Its current version applicationMandiant RedLine is RedLine 1.14 and its release date is June 12, 2015. It is also an analysis tool that includes multiple usability improvements. Mandiant RedLine can reveal malicious software which is "hidden".
It also provides MD5 hashes that are files that contain the digital signatures of some other files to understand that the downloader is not corrupted.
The MD5 hashes used by RedLine filter some of the entries in the memory analysis.
RedLine also uses "Indicators of Compromise" (IOC) (Called the Compromise Index in Greek).
They are virus and IP signatures, MD5 hashes of malware (malicious) files and can be used to detect early attack attacks in the future.
When we put the data in RedLine:
1) We create a collector (IOC search collector )
2) We run the analysis We prefer to promote it from a USB
3) Analyze data From a collector, From a stored memory folder or from a previous resolution
It also supports operating systems such as Windows XP, Windows Vista, Windows 7, Windows 8 (32-bit and 64-bit). Downloading Redline is free and the file size is 66.2 MB.
Redline
MD5: F51F458F7A69F9EF8FFEC9693A4444C5
SHA-1: 60A972C62BF8AA6F33F133BDE5866A46F5164840
Release Notes: Redline 1.14 (PDF)
User Guide: Redline 1.14 (PDF)
Whitelist: Whitelist 1.0 for Redline (ZIP)
https://www.mandiant.com/resources/downloads/
Aristea Tousia, Konstantina Paitaridou @Wikibook





