The iPhone has earned a reputation as device focused on security thanks (in part) to Apple's tight grip on the ecosystem.
However, no device is perfect when it comes to security. So, can your iPhone be hacked? What are the risks?
What does it mean to "hack" an iPhone
Invasion is a loose term that is often misused. Traditionally, it refers to the illegal acquisition of access to a computer network. In the case of an iPhone, the intrusion could refer to any of the following:
- Access someone's personal information stored on iPhone.
- Monitor or use an iPhone remotely without the knowledge or consent of the owner.
-
Change the way an iPhone works using additional software or hardware.
Technically, someone guessing your password could be an intrusion. Installing tracking software on your iPhone so that someone can spy on your activities can also be something one would expect a hacker to do.
There is also jailbreaking or installing custom firmware on a device. This is one of the most common definitions of hacking, but it is also widely used. Many people have "scratched" their own iPhones by installing a modified version of iOS to remove Apple restrictions.
Malware is another problem that has plagued the iPhone in the past. Not only have apps in the App Store been classified as malware, but exploits have been found zeroς ημέρας στο πρόγραμμα περιήγησης ιστού της Apple, Safari. Αυτό επέτρεψε στους χάκερ να εγκαταστήσουν λογισμικό υποκλοπής spyware που παρακάμπτει τα μέτρα security of Apple and steal personal information.

The jailbreaking space is moving fast. It's an ongoing cat and mouse game between Apple and tweakers. If you keep your device up to date, it is likely to be "safe" against any jailbreaking-based breaches.
However, there is no reason to be disappointed. Piracy groups, governments and law enforcement agencies are interested in finding ways to protect Apple. Any of them could make a breakthrough at any time and alert Apple or the public.
Your iPhone cannot be used remotely
Apple does not allow anyone to remotely control an iPhone through remote access applications such as TeamViewer. While macOS comes with a Virtual Computer Network (VNC) server installed that allows your Mac to be controlled remotely if enabled, iOS does not.
This means that you can not control someone's iPhone without breaking it. There are VNC servers available for jailbroken iPhones that allow this functionality, but iOS does not.
IOS uses a powerful permissions system to give applications explicit access to certain services and information. When you first install a new app, you are often asked to authorize location services or your iOS camera. Applications will not be able to access this information without your express permission.
There is no license level available on iOS that provides full access to the system. Each application is a sandbox, which means that the software is separated from the rest of the system in a secure "sandbox" environment. This prevents potentially harmful applications from affecting the rest of the system, including restricting access to personal information and application data.
You should always be careful about the rights you grant to an application. For example, an app like Facebook wants access to your contacts but does not require it to work. Once you have access to this information, the application can do whatever it wants with this data, including uploading it to a private server and storing it forever. This may violate Apple's developer and App Store agreement, but it is technically possible for an application to do so.
While it is normal to worry about malware attacks on your device, you are probably at greater risk of giving your personal information to a "secure" application that you just asked politely. Check your iPhone app licenses regularly and always think twice before accepting the requirements of an app.
Apple ID and iCloud Security
Your Apple ID (which is your iCloud account) is probably more sensitive to external interference than your iPhone. Like any online account, many third parties can obtain your credentials.
You may have enabled 2-factor authentication (XNUMXFA) on your Apple ID already. However, you may want to make sure by going to Settings> [Your Name]> Password and Security on your iPhone. Click "Enable two-factor authentication" to set it up if it is not already enabled.
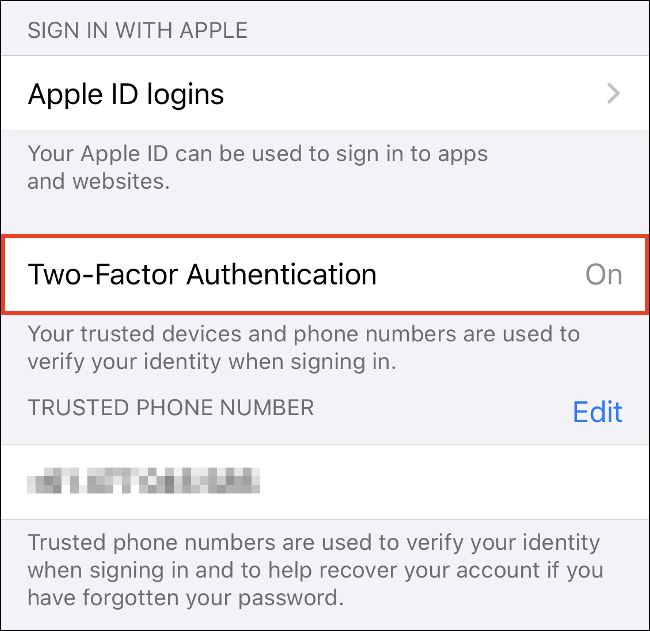
In the future, whenever you sign in to your Apple ID or iCloud account, you will need to enter a code sent to your device or phone number This prevents someone from logging in to your account even if they know your password.
Even 2FA is prone to social engineering attacks, however. Social engineering has been used to transfer a phone number from one SIM card to another. This could give an aspiring "hacker" the last piece of the puzzle in your entire online life if they already know your master email password.
This is not an attempt to scare or misunderstand you. However, it proves that something can be hacked if given enough time and intelligence. You should not worry too much about these things, but you should be aware of the dangers and be careful.
What about "Spy" iPhone software?
One of the closest things to a hack to affect iPhone owners is the so-called spyware. These applications dispel paranoia and fear by inviting people to install monitoring software on devices. These are commercially available to concerned parents and suspicious spouses as a way to track someone else's iPhone activity.
These apps cannot run on iOS stock, so they require the device to be jailbroken first. This opens up the iPhone to further manipulation, security issues and possible application compatibility issues, as some applications will not work on jailbroken devices.
After stopping the device and installing the monitoring service, users can spy on individual devices from web dashboards. This person will see every message text sent, the details of all calls made and received, even new photos or videos taken with the camera.
These apps will not work on the latest iPhones (including the XS, XR, 11 and latest SE) and only a connected jailbreak is available for some iOS 13 devices. They fell out of favor because Apple makes it so hard to do jailbreak recent devices, so they pose a small threat to iOS 13.
However, it will not stay that way forever. With each major jailbreak development, these companies start marketing again. Not only is spying on a loved one questionable (and illegal), jailbreaking someone's device also exposes them to malware. It also void any warranty that was withdrawn.
Wi-Fi may still be vulnerable
No matter what device you use, wireless networks are still one of the biggest threats to the security of mobile devices. Hackers can (and do) use "man in the middle" attacks to create fake, insecure wireless networks to capture traffic.
By analyzing this traffic (known as packet sniffing), an attacker may be able to see the information you send and receive. If this information is not encrypted, you may have passwords, login credentials, and other sensitive information.
Be smart and avoid using wireless networks and be careful when using a public network. For complete peace of mind, encrypt your iPhone traffic with a VPN.





