New documents leaked by him Edward Snowden accuse the US National Security Service (NSA) of being able to break the links between the Google and Yahoo datacenters.
Η The Washington Post, citing the documents he received from Edward Snowden, says the NSA is able to have hundreds of millions of user accounts from around the world.
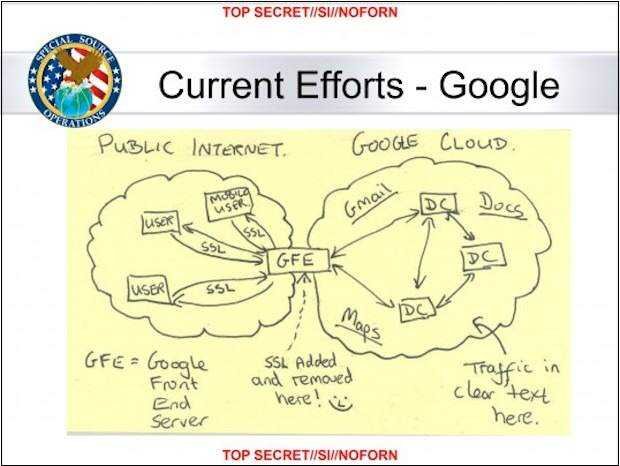
In a document classified as "top secret" dated January 9, 2013, it is stated that the service is able to send millions records daily from Yahoo and Google's data centers at its headquarters in Fort Meade. In the past 30 days, it is reported that the service managed to collect 181 million new records, including metadata as well as the content of communications.
The project, codenamed “Muscular,” operates in collaboration with the British secret service GCHQ, and aims to tap into the cables connecting the data centers of two large Internet technology companies.
The project uses the weaknesses of the systems as alleged by the service Cloud of Google and Yahoo That is, where their customers' data is stored.
Both Companies they use private fiber optic cables owned by businesses Tier 1, but leased to the Internet giants to have the speed, safety (!) and reliability (!) they need.
The leaked NSA transparency, entitled "Google Cloud Exploitation, ”Presents handwritten notes with a plan that explains how the service can access foreign networks. The manuscript shows a lot of evidence and with a smile please the point where the encryption is bypassed "SSL added and removed here. "





