The next time you're forced to create a code access (password), with combinations of upper and lower case, numbers and symbols, do not think that you are safe.
 Randy Abrams, senior security analyst at Webroot, did some simple tests. Count all possible passwords you can create with eight characters, numbers, uppercase and lowercase letters and symbols.
Randy Abrams, senior security analyst at Webroot, did some simple tests. Count all possible passwords you can create with eight characters, numbers, uppercase and lowercase letters and symbols.
He found that 95 ^ 8 possible combinations can be made (26 uppercase + 26 lowercase + 10 numbers + 33 symbols = 95 characters), which are 6.634.204.312.890.625 codes.
Suppose now that someone is trying to find your password with a typical brute-force attack. Suppose they can try out about 31 billion passwords per second. So breaking the code mentioned above can be done, in a maximum of 212,903 seconds, or 3.548 minutes, or about two and a half days.
Now, let's talk about restrictions. Suppose a service you are using requires an eight-character code.
Abrams reports that there are 70,6 trillion 8-letter passwords. This saves the brute-force attack 2,277 seconds, or almost 38 minutes.
But what if, at name of security, you use an eight-character password (so you can remember it), and a service forces you to use only capital letters and symbols. Is it safer that way? Is it a more complex password, which makes it difficult for the decoder? Not exactly.
According to Abrams, you just cut 18,5 percent from the potential password group. So in two days, the attacker will discover your password.
If a service requires you to add a number to this password, you have cut the potential passwords to 41 percent. So the attack will last 34 hours, or a day and a half.
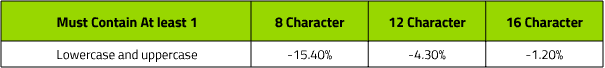
Abrams states that it is much better to choose a longer password:
Each additional character in a password actually increases the group of passwords (passwords). There are 6,5 million times more combinations of words with 16 lowercase characters than there are eight-character codes using all four character sets. This means 'toodlesmypoodles' is much harder to crack than 'I81B @ gle'
Of course after all the above you understand the value of using the two phase authentication (2FA).
___________________
- Chrome: Activate the password generator
- Easily find your Wi-Fi password
- PassProtect: Addon alerts you to insecure passwords





