Recently, we've heard a lot of news about Quishing – or the electronic fishing QR Code. This is when the link behind a QR Code is malicious, but it is not. There has been a report of a major US energy company being targeted by a phishing QR Code.
Other reports indicate an increase in this type of attack.

In fact, Harmony Email researchers have seen a 587% increase in QR Code phishing scams between August and September, and have also found that almost all of our customers have been targeted with a QR Code attack. That equates to thousands attacks the month!
But what is the reason for this upward trend? The QR Codes we use to scan menus look pretty harmless, and friendly.
That alone is a great way to hide behind malicious intent. The image may hide a malicious link behind it and if the original one is not scanned and analyzed then it will just appear as a normal image.
And since end users are used to scanning QR Codes, receiving one in an email is not necessarily a cause for concern. In fact, according to statista, in 2022, approximately 89 million smartphone users in the United States scanned a QR Code on mobile Appliances, a 26% increase compared to 2020. The use of mobile QR Code scanners is expected to see continued growth, reaching over 100 million users in the US by 2025.
Here's an analysis by Harmony Email researchers of how hackers use QR codes to obtain personal information.
The attack
In this attack, hackers send QR codes that lead to personal information collection pages.
● Vector: Email
● Type: Personal Information Collection, Quishing
● Techniques: Social Engineering
● Target: Any end user
Example of electronic post officeυ
It is very easy to create a QR Code. There are countless free websites that make creating them extremely simple.
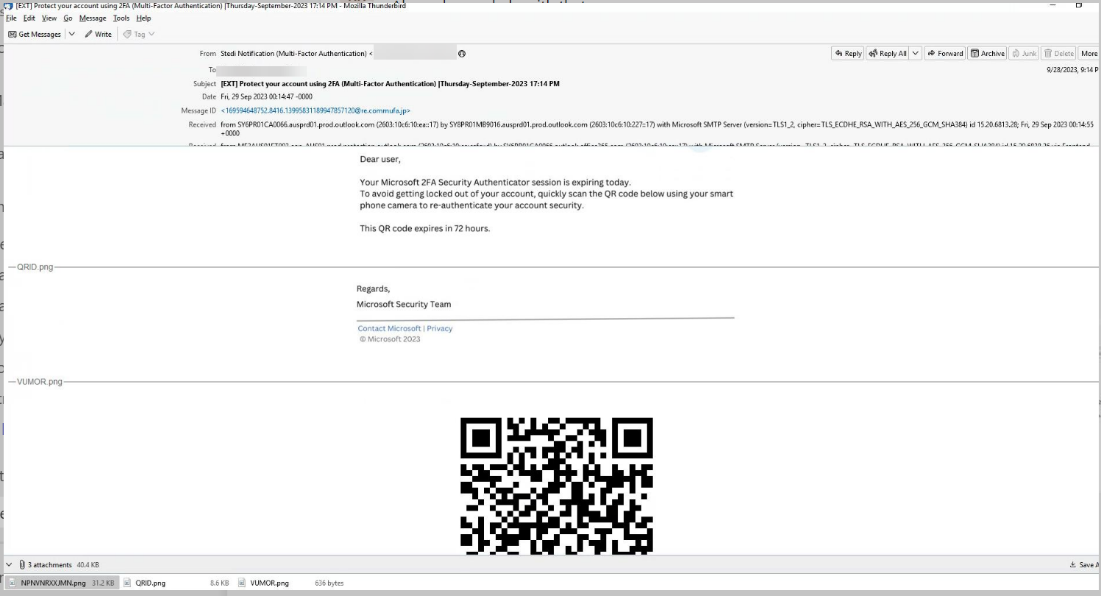
QR Codes redirect a link. Hackers – or anyone else – can enter anything into the link that the QR Code redirects.
In this particular attack, the hackers have created a QR Code that goes to a personal information collection page. The lure is the expiration of Microsoft's MFA and thus the reauthentication of the user.
Although the text says it's from Microsoft Security, the sender address is different.
Once the user scans the QR Code, they will be redirected to a page that looks like Microsoft, but is actually just a personal information collection page.
Best practices: guidance and recommendations
To protect against such attacks, security professionals can do the following:
● Implement email security that leverages OCR for all attacks, including quishing
● Implement security that uses AI, ML and NLP to understand the intent of a message and when phishing language might be used
● Implement security that has more than one way to detect malicious attacks





