Proxy Mask is a network tool to protect your privacy.
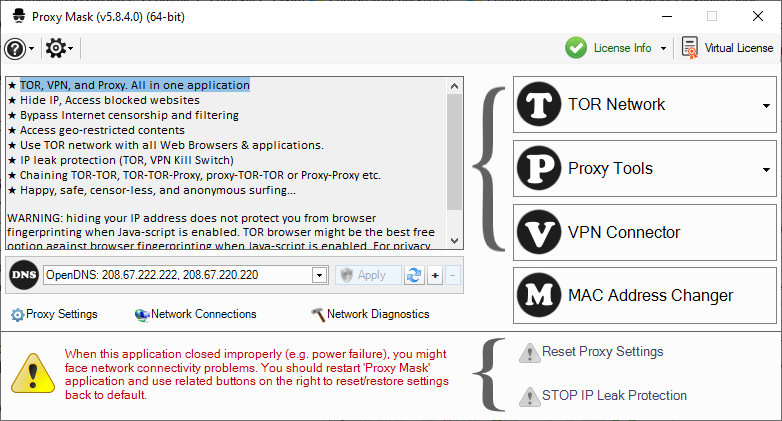
In short it allows users to increase online privacy, bypass internet censorship and filtering, access blocked and censored websites, hide your real address IPs from websites, access geo-restricted content, use the TOR network with all web browsers and applications, etc.
Main characteristics
TOR Network: Use the TOR network with all or specific applications
Multi-TOR: Create multiple TOR proxies and use them separately to increase your download speed over TOR
Chain TOR: Multiple TOR server chain. e.g. proxy-TOR-TOR-Proxy
Proxy Checker & Switcher: Proxy testing/testing up to 40 simultaneous tests.
Proxy Converter & chain: Chain multiple proxies and conversion socks to HTTP proxy.
VPN: List free VPN you can use.
Change MAC address: Change (spoof) Media Access Control (MAC) Network Interface Card (NIC) address and bypass network MAC address filtering.
DNS Changer: Bypass Internet censorship and DNS filtering. Or set a restrictive DNS to block harmful content for children.
IP Leak Protection: Firewall rules that block all incoming and outgoing connections except for specific IP addresses (IP address, bridge TOR etc.)
FORCE to HTTPS: forces all connections to websites to use a secure encrypted connection (HTTPS). Highly recommended
DOH: DNS over HTTPS for socks4 proxies.
Download the application
More information
https://www.rentanadviser.com/products/proxy-mask/proxy-mask.aspx