FOCA was launched in 2009 and is now in its third edition. Although a Linux version is included with Kali, it is quite old. Let's download the latest version for Windows and use it to do some reconnaissance.

FOCA is a great website recognition tool with many interesting features and capabilities. Remember, before attacking any site, it is important to gather as much information as possible. From this information, you can determine the attack that is most likely to work against that particular website or network.
In this guide, we'll look at FOCA's ability to find, download and recover archives from websites with the Metadata of the file.
This Metadata can give us information such as users (which can be critical for cracking passwords access), the functional system (exploits are OS-specific), email addresses (potentially for social engineering), software used (again, exploits are OS-specific and increasingly application-specific), and whether we are lucky, the passwords.
Step 1: Download FOCA for Windows
First, let's free download the SEAL which is for Windows.
Step 2: Choose where to save the results
When you install FOCA, you will be presented with a screen like the one below. The first thing we need to do is start a new project and then tell FOCA where we want to save our results.
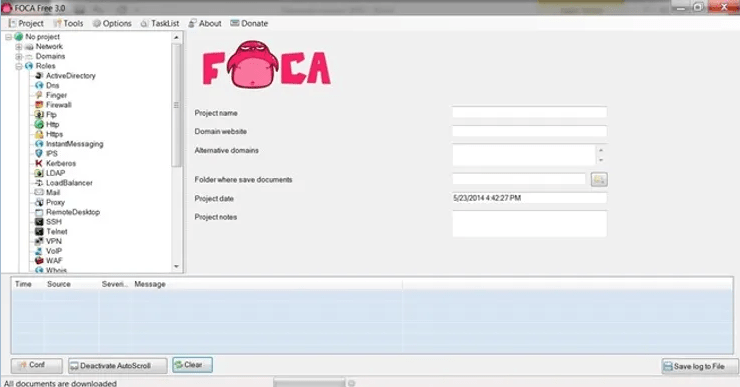
I created a new directory in the C:\foca and I will save all my results there. Of course, you can save your results wherever you like, or use the default directory temp.
Step 3: Create a new project
In this guide, I'll start with a project called SANS, which is at sans.org, and save my results to C:\foca.
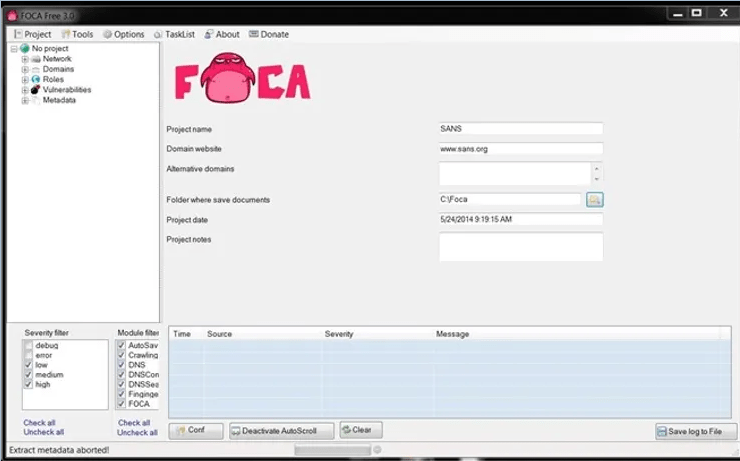
Step 4: Download Metadata
Once I've created my project, I can go to the object explorer on the left and select Metadata. This allows us to derive Metadata from the files on the website that contain Metadata. Files like .pdf, .doc, .xls, etc. contain Metadata that could be useful in hacking your target.
When you choose Metadata, a screen like the one below will appear. In our case here, we're going to search sans.org for .doc files, so the syntax to put in the search window is:
site: sans.org filetype: doc
This will search the entire sans.org site, looking for .doc files. When I press the Search button next to the window, it will start searching and find all the .doc files on sans.org.
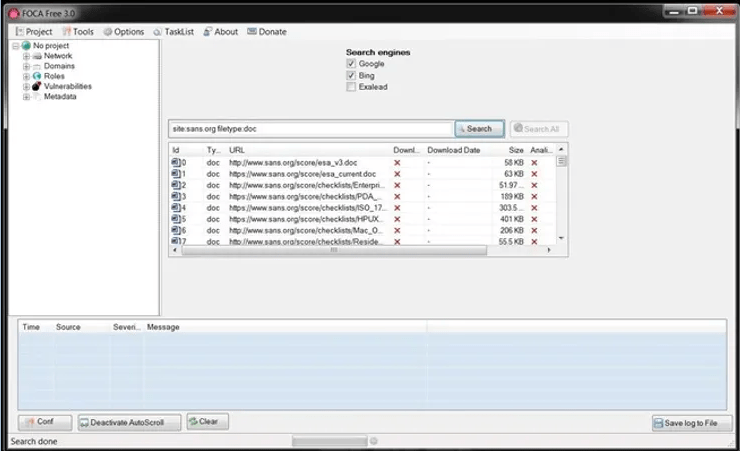
Of course, if you were looking for files . Pdf or other file types, you would put this file type. You can also search for multiple file types by listing them after the file type, such as:
site: sans.org filetype: pdf, doc, xls
Step 5: Download the files
Once FOCA has retrieved a list of all .doc files, we can then right-click on any file and download the file to our hard drive, download all files, or analyze the Metadata. I chose to download all files .doc which I found on sans.org.
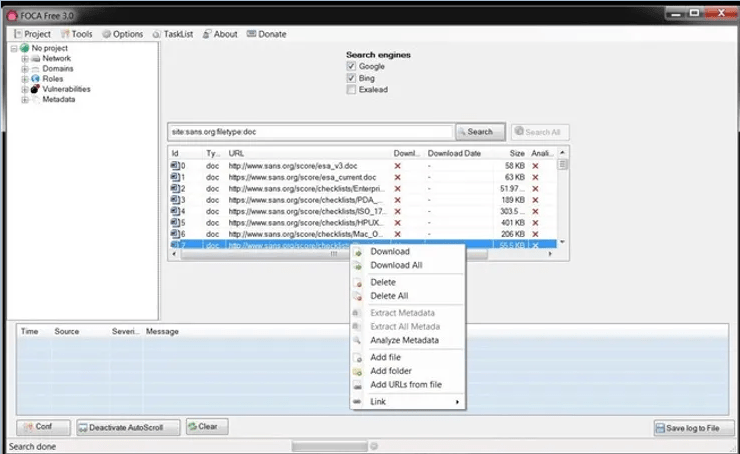
Step 6: Collection and Analysis of Metadata
Now that we have downloaded all the .doc files, I chose to analyze all their metadata. Microsoft Office files collect significant amounts of data as they are created and processed, which we can then export.
When we expand the Metadata folder in the object explorer, you can see that we have 156 .doc files and 2 .docx files.
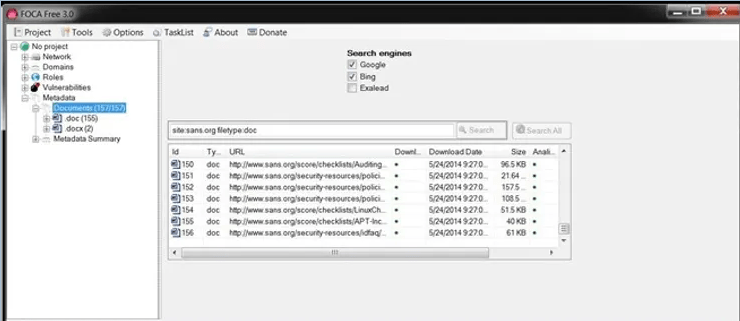
The types of Metadata collected
Right under the envelope Metadata documents there is another envelope titled Metadata Summary. We can click on it and it reveals the type of Metadata it has collected from the files. This Metadata is divided into eight (8) categories:
-
Users
-
Folders
-
Software
-
Emails
-
Operating Systems
-
Passwords
-
Servers
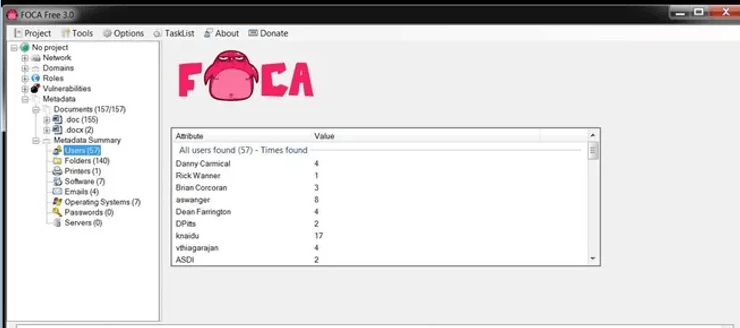
Let's look at them first users. When we click on Users, we see that FOCA has collected the names of every user that exists in these files.
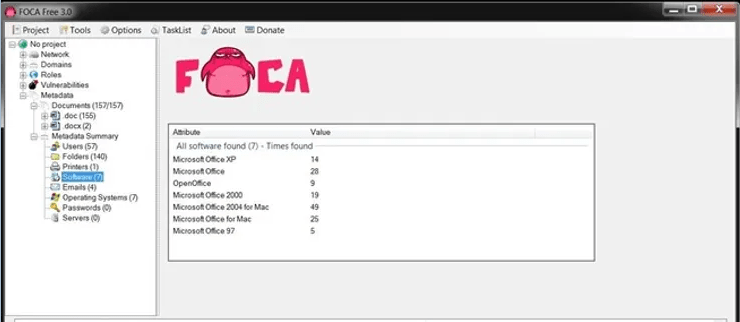
When we click on the option Software, we can see the different versions of Microsoft Office used, including five (5) users who created their documents with Office '97.
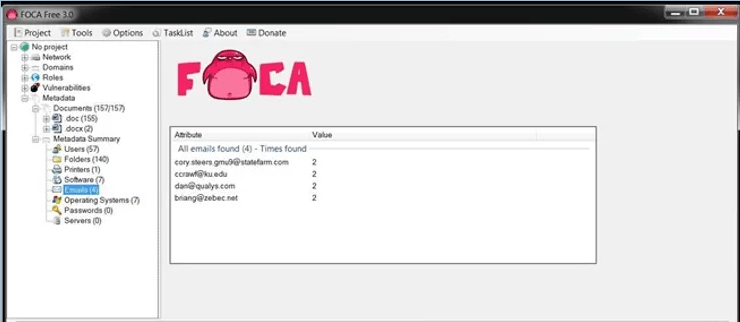
We can also search for email addresses embedded in documents, as shown below. Obviously, these people are potential targets for a social engineering attack.
We may also collect printer, folder, password and server information from them metadata depending on the documents we retrieve. All of this information can then be used to determine what is the best attack against that organization/website.





