Symantec: Considering the large amount of work being done on the Internet today, websites are a primary target for cyber criminals. Although the methods used in online attacks are relatively well known, however, protection against threats remains untenable for many companies and tends to be compatible with it. The complexity of the internet, coupled with its lack of infrastructure, makes many websites vulnerable and threat is constantly increasing.
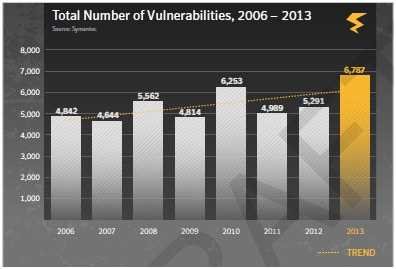
According to her latest report Symantec Internet Security Threat Report, there have been 6.787 vulnerabilities in 2013, as compared to 5.291 2012. Still worrying is the fact that one in eight sites had critical, unpatched, known vulnerabilities, with 67% of the sites used to distribute malware that appears as genuine / legitimate.
Over the last few years, the amount of malware on the Internet has increased dramatically and this is due to the use of automation and exploit kits.
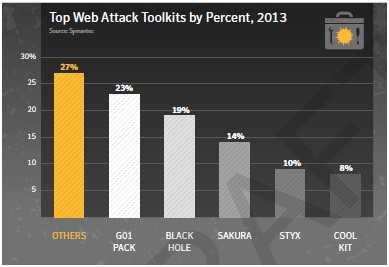
Οι hackers χρησιμοποιούν έτοιμο λογισμικό που περιέχει μία ευρύτατη γκάμα κακόβουλων προγραμμάτων και exploit kits, για να μεταφέρουν αυτοματοποιημένες «drive-by» επιθέσεις διαδίδοντας κακόβουλο λογισμικό και προσβάοντας ανυποψίαστους users. Με τα exploit kits, οι εγκληματίες του κυβερνοχώρου μπορούν εύκολα να βελτιώσουν τις επιθέσεις τους και να δοκιμάσουν πολλαπλές hacking τακτικές για να εκμεταλλευτούν τις ταυτοποιημένες ευπάθειες.
The wide spread of these tools becomes apparent in the average of malicious websites that are blocked on a daily basis. Increasing the popularity of exploit kits that are used on the internet does not only create a good ground for attacking hackers but puts higher barriers on companies to protect their infrastructure.
Today, any website can be infringed by cybercriminals and used to attack your data. Below are five of the most common methods of attack that are still the scourge of many websites. Tips for "Open Web Application Security (OWASP)" for detailed description of the methods are presented below:
1.SQL Injection
SQL injection is a code injection technique that maliciously injects SQL statements into an input field and causes them to be reset information which should not be on the web server. As a result, the web server provides access to information that should be secure, such as usernames and passwords.
2. Cross Site Scripting (XSS)
Cross-Site Scripting is the most common web application security vulnerability that occurs when an application gets unreliable data and sends it to a web browser without proper authorization. This allows attackers to run scripts on victims 'browsers when they visit a site, which can result in hijacking users' sessions, vandalizing websites, or driving the user to malicious websites.
3. CSRF (Cross-Site Request Forgery)
A CSRF attack intercepts victim's cookies and other authentication information that is used to link to a vulnerable website. Once the process has been completed, the attacker can check the victim's session, for example on a banking website, and have full control over the account. However, because the site considers that a legitimate user is logged in, it is very difficult to detect when the attack is successful.
4. Use Components of Known Fraud
Elements such as libraries, frameworks, as well as other software modules that have known vulnerabilities have become easy prey for attackers. However, as we saw with the recent HeartBleed virus, effective management των patches και η ασφαλή κωδικοποίηση μπορεί να είναι δύσκολη, ειδικά για σύνθετες διαδικτυακές εφαρμογές. Εφαρμογές που χρησιμοποιούν στοιχεία με γνωστές ευπάθειες μπορεί να υπονομεύσουν τους μηχανισμούς άμυνας της εφαρμογής και να επιτρέψουν την πραγματοποίηση μιας σειράς πιθανών επιθέσεων.
5. Man in the Middle
Η επίθεση «man-in-the middle» παρεμβαίνει στην επικοινωνία μεταξύ two συστημάτων. Για παράδειγμα, σε μια http συναλλαγή ο στόχος είναι η σύνδεση TCP μεταξύ πελάτη και server. Σε ορισμένες περιπτώσεις, έχουμε δει ιστοσελίδες να μεταφέρουν ευαίσθητες πληροφορίες χωρίς αρκετά ισχυρή κρυπτογράφηση.
These common online vulnerabilities are largely due to the lack of protection of the web application code itself. In theory, this means that vulnerabilities can be prevented by applying Best Practices to Software Development Life Cycle (SDLC). However, the pace of change and the demanding nature of growing business requirements has resulted in many organizations struggling to implement security in their SDLC until it is not too late.
For many businesses security is still reactive and is often applied since the attacker has already done the damage. Symantec is proposing to businesses to take advantage of security in the development process so they can be designed in the web application from scratch. The cost of a potentially slow development process for creating a secure code outweighs the waiting risks until it is revealed that you have been the victim of a sophisticated campaign focusing on your privacy.
In addition, it is recommended that both the development environment and the production environment be jointly controlled for any external threats. Most of the common attacks have known IDS / IPS signatures, making them easy to find Symantec Managed Security Services so as to warn and act for a quick recovery.






