Check Point Research (CPR) has discovered new and complex details about its development Trickbot.
The well-known banking Trojan steals and exposes its victims' data, targeting high-profile victims. CPR has recorded more than 140.000 machines infected with Trickbot since November 2020, many of which are customers of well-known companies such as Amazon, Microsoft, Google and PayPal. In total, CPR recorded 60 companies whose customers fell victim to it during the past 14 months.
1 Chart. Companies whose customers are the target of Trickbot

Basic details of implementing Trickbot
Malware is very selective in the way it chooses its targets
- Various tricks - including anti-analysis and anti-Deobfuscation - applied inside the modules demonstrate the high technical background of its creators
- Its infrastructure can be used by various families of malware to cause more damage to infected computers
- Sophisticated and flexible malware with more than 20 modules that can be downloaded and run to order
How Trickbot works:
1. Perpetrators receive a database of stolen emails and send malicious documents to selected addresses.
2. The user downloads and opens such a document, allowing macros to be executed during the process
3. The first stage of the malware is executed and the main load of the Trickbot is downloaded.
4. The main load of the Trickbot is executed and it establishes its stay in the infected machine.
5. Trickbot auxiliary modules can be downloaded to the infected machine to order from the threat carriers, the functionality of these modules can vary: it can spread through corrupt corporate network, steal corporate credentials, snatch bank links. λπ.
Impact
The following is a map of the percentage of organisms affected by Trickbot in each country according to CPR telemetry data:
2 Chart. Percentage of organisms affected by Trickbot (the darker the color - the greater the impact)
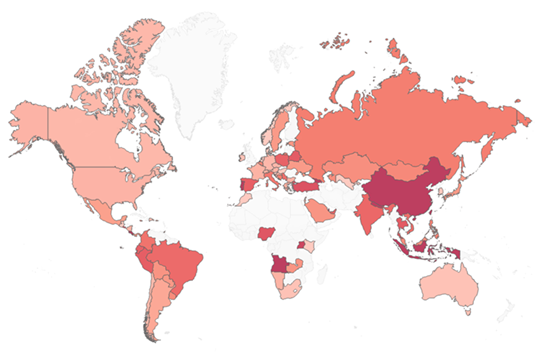
The following is a table showing the percentage of organisms affected by Trickbot in each area:
|
Area |
Affected organizations |
Rate |
|
Global |
1 on 45 |
Present in several = 2.2% |
|
APAC |
1 in 30 |
Present in several = 3.3% |
|
Latin America |
1 in 47 |
Present in several = 2.1% |
|
Europe |
1 in 54 |
Present in several = 1.9% |
|
Africa |
1 in 57 |
Present in several = 1.8% |
|
North America |
1 in 69 |
Present in several = 1.4% |
Comment by Alexander Chailytko, Cyber Security, Research & Innovation Manager at Check Point Software Technologies,
“Τα νούμερα του Trickbot είναι συγκλονιστικά. Έχουμε καταγράψει πάνω από 140.000 μηχανές που στοχεύουν τους πελάτες μερικών από τις μεγαλύτερες και πιο αξιόπιστες εταιρείες στον κόσμο. Συνεχίσαμε να παρατηρούμε ότι οι δημιουργοί του Trickbot έχουν τις ικανότητες να προσεγγίζουν την ανάπτυξη κακόβουλου λογισμικού από πολύ χαμηλό επίπεδο και να δίνουν προσοχή σε μικρές λεπτομέρειες. Το Trickbot επιτίθεται σε θύματα υψηλού προφίλ για να κλέψει τα διαπιστευτήρια και να παρέχει στους χειριστές του πρόσβαση στις πύλες με ευαίσθητα δεδομένα, όπου μπορούν να προκαλέσουν ακόμη μεγαλύτερη ζημιά. Ταυτόχρονα, γνωρίζουμε ότι οι χειριστές που βρίσκονται πίσω από την εφαρμογή έχουν επίσης μεγάλη εμπειρία στην ανάπτυξη κακόβουλου λογισμικού σε υψηλό επίπεδο. Ο συνδυασμός αυτών των δύο παραγόντων είναι αυτός που επιτρέπει στο Trickbot να παραμένει μια επικίνδυνη απειλή εδώ για περισσότερό από 5 χρόνια. Προτρέπω τους χρήστες να ανοίγουν έγγραφα μόνο από αξιόπιστες πηγές και να χρησιμοποιούν διαφορετικούς κωδικούς πρόσβασης σε διαφορετικές τοποθεσίες στο Internet".
Security tips
1. Only open documents that you receive from trusted sources. Do not enable macro execution in documents.
2. Make sure you have the latest operating system and anti-virus updates.
3. Use different passwords on different websites.
| Annex - The list of target companies | |
| Company | Field |
| Amazon | E-commerce |
| American Express | Credit Card Service |
| AmeriTrade | Financial Services |
| AOL | Online service provider |
| Associated Banc Corp. | Bank Holding |
| BancorpSouth | Banks |
| Bank of Montreal | Investment Banking |
| Barclays Bank Delaware | Banks |
| Blockchain.com | Cryptocurrency Financial Services |
| Canadian Imperial Bank of Commerce | Financial Services |
| Capital One | Bank Holding |
| Card Center Direct | Digital Banking |
| Centennial Bank | Bank Holding |
| Chase | consumer banking |
| Citi | Financial Services |
| Citibank | Digital Banking |
| Citizens Financial Group | Banks |
| Coamerica | Financial Services |
| Columbia Bank | Banks |
| Desjardins Group | Financial Services |
| e-trade | Financial Services |
| Fidelity | Financial Services |
| Fifth Third | Banks |
| FundsXpress | IT service management |
| Technology | |
| GoToMyCard | Financial Services |
| Hawaii USA Federal Credit Union | Credit Union |
| Huntington bancshares | Bank Holding |
| Huntington bank | Bank Holding |
| Interactive Brokers | Financial Services |
| JPMorgan Chase | Investment banking |
| Keybank | Banks |
| LexisNexis | data mining |
| M&T Bank | Banks |
| Microsoft | Technology |
| Federal Navy | Credit Union |
| paypal | financial technology |
| PNC Bank | Banks |
| RBCBank | Banks |
| Robinhood | Stock Trading |
| Royal Bank of Canada | Financial Services |
| Schwab | Financial Services |
| Scotiabank Canada | Banks |
| SunTrust Bank | Bank Holding |
| Synchrony | Financial Services |
| Synovus | Financial Services |
| T Rowe Price | Investment Management |
| TD Bank | Banks |
| TD Commercial Banking | Financial Services |
| TIAA | Insurance |
| Truist financial | Bank Holding |
| US Bancorp | Bank Holding |
| Unionbank | commercial banking |
| USAA | Financial Services |
| Vanguard | Investment Management |
| Wells Fargo | Financial Services |
| Yahoo | Technology |
| ZoomInfo | Software as a service |





