Η Check Point Research (CPR), το τμήμα έρευνας της Check Point Software Technologies, προειδοποιεί για πιθανές επιθέσεις ransomware καθώς βλέπει δείγματα του Emotet to spread rapidly through it Trickbot. Since the authorities took down Emotet, CPR estimates 140.000 Trickbot victims, in 149 countries in just 10 months. New samples of it Emotet spread through Trickbot were discovered by CPR on November 15, 2021. 
Emotet is a strong indicator of future ransomware attacks, as the malicious software it gives ransomware gangs a way to get into compromised devices.
Check Point Research (CPR) sees samples of it Emotet spread rapidly through increased Trickbot activity. Emotet, once described as "the most dangerous malware in the world", provides threat backdoors to unsafe devices that could be leased to ransomware gangs and used for their own campaigns. Therefore, the return of Emotet is a strong indication for the future ransomware attacks.
Earlier this year, an international law enforcement operation coordinated by Europol and Eurojust managed to take control of Emotet's infrastructure and arrested two people. Ten months later, on November 15, 2021, Trickbot-infected devices began dropping Emotet samples by forwarding them to users with download-protected password files containing malicious documents that restructure Emotet's botnet network. Emotet has also upgraded its features, adding some new tricks to its toolbox.
1 Chart. The chart below shows the victims of Emotet in the year 2021.
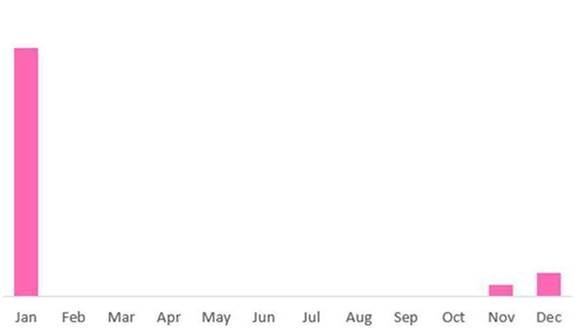
140,000 + Trickbot victims
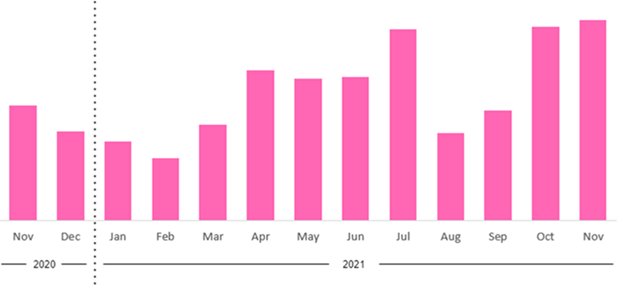
Trickbot has shown a persistent growth rate. CPR has identified more than 140.000 victims affected by it since the abolition of botnet, including organizations and individuals. Trickbot affected a total of 149 countries, or more than 75% of all countries in the world.
2 Chart. The Dynamics of the Trickbot on infected machines from November 1, 2020
Trickbot and Geographic Data
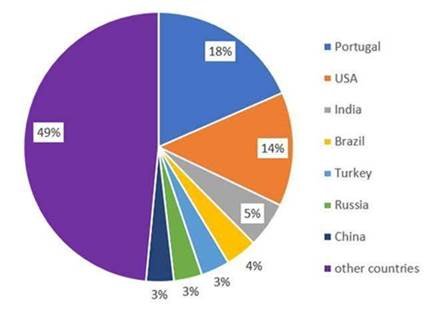
Almost one third of all Trickbot targets are in Portugal and the USA.
Graph 3. The victims of Trickbot from November 1, 2020 grouped by country
Trickbot per Market
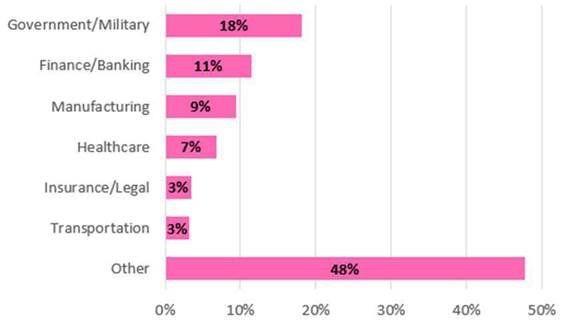
The CPR monitored the distribution of victims by industry, which is shown in the graph below. Victims from high-profile industries make up more than 50% of all victims.
4 Chart. Trickbot victims from November 1, 2020 grouped by industry
Comment by Lotem Finkelstein, Head of Threat Intelligence at Check Point Software:
"Emotet was the most powerful botnet in the history of cybercrime with a rich infection base. Now, Emotet has resold its infection base to other threat carriers to spread its most commonly malicious software. ransomware. The return of Emotet is an important warning sign for another increase in ransomware attacks as we enter 2022. ”
"Trickbot, which has always worked with Emotet, facilitates its return by promoting it to infected victims. This has allowed Emotetna to start from a very stable position and not from scratch. In just two weeks it became the 7th most popular malware, as you will notice in the most recent list of the most common malware. "Emotet is the best indicator we have for future ransomware attacks and as ransomware we have to deal with Emotet and Trickbot infections, otherwise it's only a matter of time before we deal with a real ransomware attack."





